Issue
Required user permissions
This article assumes that you have the appropriate access rights and permissions to perform the tasks below.
If you use the default Administrator user or are unable to perform the tasks below (the option is unavailable), create a second administrator user with all access rights.
- ESET PROTECT users: Create a second administrator user in ESET PROTECT
- ESET Security Management Center (ESMC) users: Create a second administrator user in ESET Security Management Center 7.x
ESET business product in Limited Support status
This article applies to an ESET product version that is currently in Limited Support status and is scheduled to reach End of Life status soon.
For a complete list of supported products and support level definitions, review the ESET End of Life Policy for business products.
- Detect client computers without ESET endpoint products installed
Solution
Examples of Dynamic Group templates and their use
For aditional examples of using Dynamic Group templates, see Dynamic Group template – examples in ESMC Online Help and Related articles below.
- Open ESET Security Management Center Web Console (ESMC Web Console) in your web browser and log in.
- Click More → Dynamic Group Templates.
- Select an existing dynamic group Template and click Edit Template to edit it, or click New Template to create a new dynamic group Template. In the following example, we will create a template for a dynamic group that contains computers without ESET endpoint solutions installed.
Figure 1-1
Click the image to view larger in new window
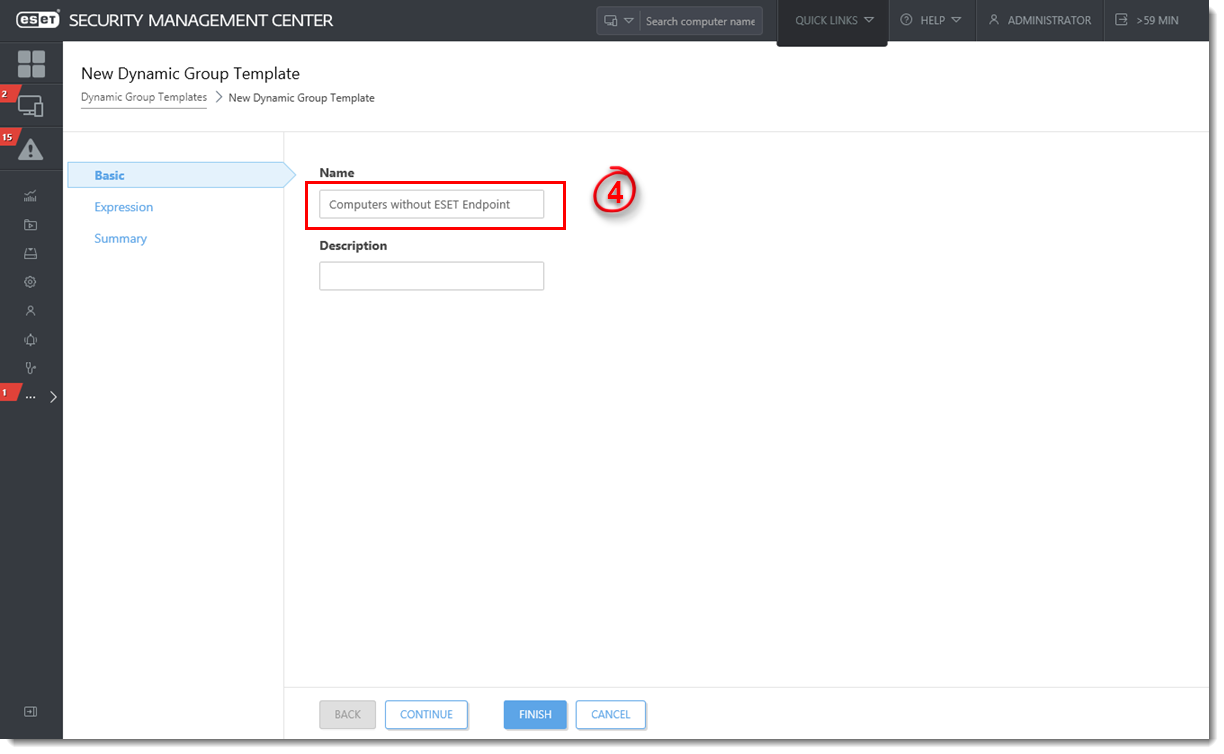
- Type a name for your new dynamic group Template into the Name field.
Figure 1-2
Click the image to view larger in new window
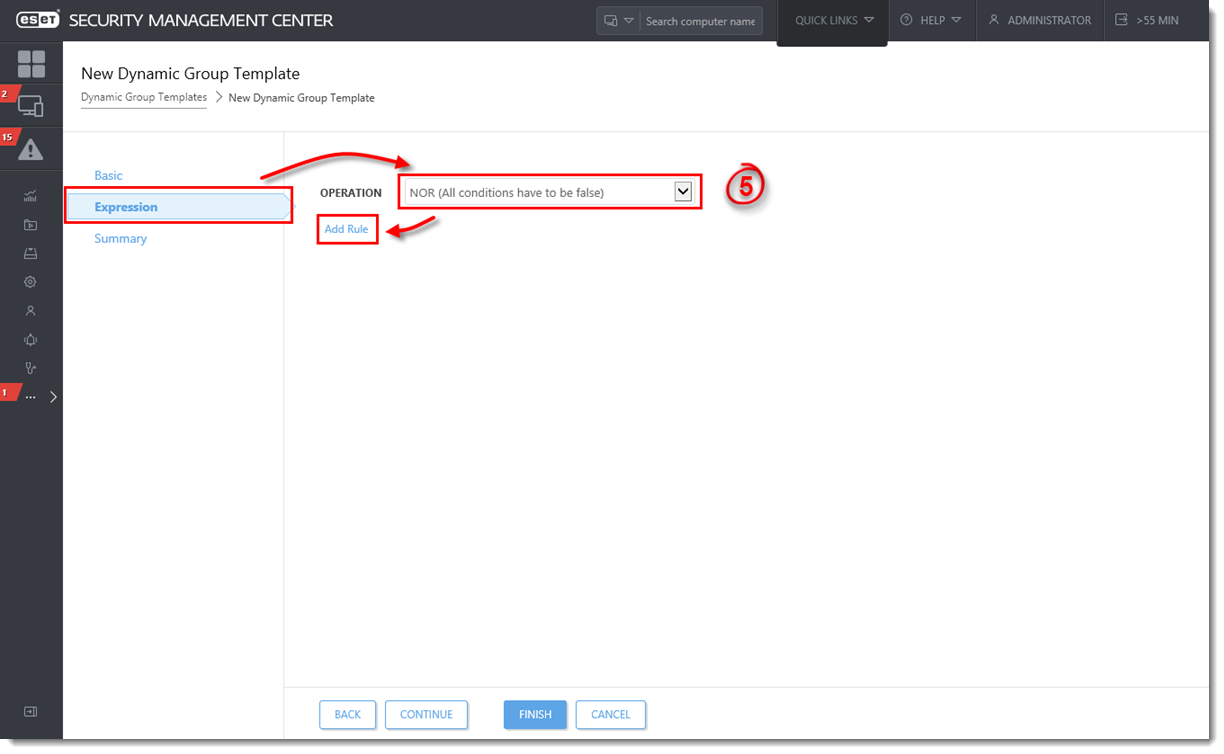
- Click Expression, select NOR (All conditions have to be false) from the Operation drop-down menu and click Add Rule. In addition to NOR, you can use the OR (at least one condition has to be true), NAND (At least one condition has to be false), and And (All conditions have to be true) operations to create custom expressions. An expression can contain multiple rules.
Figure 1-3
Click the image to view larger in new window
- You can create rules to sort devices by a variety of criteria. Expand each section below for more information about each of the criteria you can sort by. Some criteria appear in multiple sections but sort devices using the same logic.
- Activated by ESET Security Management Center—Group devices based on whether they were activated, or are not activated by ESET Security Management Center
- License expiration date—Group devices based on their license expiration date
- License flags
- License model status
- License model type
- License product name—Group devices based on the product named in your product license
- License public ID—Group devices based on the public ID associated with a specific product license
- License renewal period
- License type
- Product code
- Seat name
Active Threats
- Detection Engine—Group devices based on which Detection engine version they are currently using, or whether their Detection engine was released before or after a specific date
- First seen time
- Hash of detected file
- Object URI—Group devices based on the Uniform Resource Indicator associated with a found threat
- Process name—Group devices based on part or all of the process name associated with a found threat
- Restart required—Group devices based on whether they require a restart
- Scan log reference—Group devices based on whether a specific item is referenced in their scan log
- Threat handled—Group devices based on whether a specific threat has been resolved
- Threat name—Group devices based on whether a specific threat was detected
- Threat type
- User—Group devices based on the user currently logged in
Computer
- Computer—Group all devices except for a specific computer together, or select a single computer to treat as a group
- Managed products mask—Group devices based on whether they are or are not covered by one of the pre-defined managed product masks
Device identifiers
- Identifier type—Group devices based on the type of identifier they use, FQDN, Computer Name, Computer Workgroup, IMEI or Serial Number
- Identifier value—Group devices based on part or all of a specific identifier value
Dynamic Threat Defense
- Analysis key
- Analysis progress serial number
- Analysis result serial number
- Hash of analysed file
- Score
- State of analysis
- Timestamp of analysis
Functionality/Protection problems
- Feature—Group devices based on which product feature(s) require attention
- Problem—Group devices based on the error notification ESET is displaying. Select from a list of available error notifications
- Source—Group devices based on the ESMC component, client solution, or operating system identified as the source of an issue
- Status—Group devices based on their indicated status. Select from Malfunction, OK, Security Notification, and Security risk
Functionality/Protection status
- Source—Group devices based on the ESMC component, client solution, or operating system identified as the source of an issue
- Status—Group devices based on their indicated status. Select from Malfunction, OK, Security Notification, and Security risk
Functionality/Protection status of computer
- Status—Group devices based on their indicated status. Select from Malfunction, OK, Security Notification, and Security risk
Hardware
- Running on battery—Group devices based on whether they are discharging (running on battery power), not discharging (running using a power adapter), or not present.
HW inventory/Device information
- Device manufacturer—Group devices based on manufacturer
- Device model—Group devices based on model
- Serial number
HW inventory/Display
- Description
- Identifier
- Manufacturer
- Serial number
HW inventory/Display adapter
- Architecture type
- Description
- Identifier
- Manufacturer
- Memory size [MB]
- Memory type
- Refresh rate (max) [Hz]
HW inventory/Chassis
- Description
- Identifier
- Manufacturer
- Serial number
- Type
HW inventory/Input device
- Description
- Identifier
- Manufacturer
- Type
HW inventory/Mass storage
- Description
- Identifier
- Manufacturer
- Serial number
- Storage capacity [MB]
- Type
HW inventory/Network adapter
- Connection name
- Description
- Identifier
- Manufacturer
- Type
HW inventory/Printer
- Description
- Identifier
- Location type
- Marking type
- Printing type
- Resolution (horizontal – vertical) [pixels per inch]
HW inventory/Processor
- Architecture type
- Clock speed [MHz]
- Description
- Identifier
- Manufacturer
- Number of cores
- Number of logical cores
HW inventory/RAM
- Architecture type
- Capacity [MB]
- Clock speed [Hz]
- Description
- Identifier
- Manufacturer
- Serial number
HW inventory/Sound device
- Description
- Identifier
- Manufacturer
Installed software
- Agent supports uninstall—Group computers with agent versions that support the agent uninstall task
- Application name—Group devices that have a specific application installed or not installed
- Application vendor—Group devices with software from a specific vendor installed
- Application version—Group devices with a specific version of an application
- Device administrator permission—Group devices based on whether you have adminstrator permissions on them or not
- Size in MB—Group devices based on the amount of drive space in MB that is used by software
Logged users
- Domain—Group devices based on whether they log in to a specific domain
- Full name—Group devices based on the full name of the device’s user
- User name—Group devices based on the name of the user currently logged in
Mobile network
- Cellular technology—Group devices based on the cellular network they use
- Home subscriber MCC—Group devices based on their Mobile Country Code (MCC)
- Home subscriber MNC—Group devices based on their Mobile Network Code (MNC)
- Phone number—Group devices based on their phone number
- Roaming subscriber—Group devices based on whether or not they are roaming
- Roaming subscriber MCC—Group devices based on their roaming Mobile Country Code
- Roaming subscriber MNC—Group devices based on their roaming Mobile Network Code
- SIM carrier network—Group devices based on their SIM carrier network
- SIM unique serial number—Group devices based on their SIM unique serial number or a range of SIM serial numbers
Network adapters
- Adapter name—Group devices based on the name of the network adapter installed
- MAC address—Group devices based on their MAC address
- Order—Group devices based on whether they are using their primary or secondary network adapter
Network DNS servers
- IP DNS server—Group devices based on their use of a specific DNS server IP address or an address within a specified range
- Order—Group devices based on whether they are using their primary or secondary DNS server
Network gateways
- IP gateway—Group devices based on the IP of the network gateway they use
Network IP addresses
- Adapter IP address—Group devices based on their network adapter IP address
- Adapter subnet mask—Group devices based on the subnet mask they use
- Address type—Group devices based on whether they use an IPv4 or IPv6 address
- IP subnetwork—Group devices based on their IP subnetwork
- MAC address—Group devices based on their MAC address
- Order—Group devices based on whether they are using their primary or secondary network IP address
Network WINS servers
- IP WINS server—Group devices based on the IP address of the WINS server they use
- Order—Group devices based on whether they are using their primary or secondary WINS server
OS edition
- OS name—Group devices based on the name of the operating system they use
- OS platform—Group devices based on the platform of the operating system they use
- OS service pack—Group devices based on whether they use a specific service pack or range of service packs
- OS type—Group devices based on the type of operating system they use
- OS version—Group devices based on the version of the operating system they use
OS locale
- OS language—Group devices based on the language of the OS they use
- OS locale—Group devices based on the locale of the OS they use
Peer certificate
- Issuer—Group devices based on the isuer of their peer certificate
- Product—Group devices based on the product associated with their peer certificate
- Serial number—Group devices based on the serial number of their peer certificate
- Status—Group devices based on whether their peer certificate is valid, invalid, going to expire, going to be invalidated, or the CA used the sign the certificate is going to expire
- Subject—Group devices based on the subject specified in their peer certificate. For example, you could assign different subjects to certificates based on office location, and then group devices based on this information
- Valid from—Group devices based on the start date for validity of their peer certificate
- Valid till—Group devices based on when their peer certificate is going to expire
Performance
- Idle state—Group devices based on whether they are or are not in an idle state
Quarantine
- Excludable—Group devices based on whether items in the quarantine can be excluded from scanning
- Hash—Group devices based on the hash of items in the quarantine
- Hits—Group devices bsed on whether they have a specific number of quarantined items, or have more or less than that number of items
- Object name—Group devices based on whether an object with a specific name is quarantined
- Restorable—Group devices based on whether items in the quarantine can be restroed to their original location(s)
- Size—Group devices based on whether items in the quarantine can be restored to their original location(s)
- Threat name—Group devices based on whether a specific threat is quarantined
- Time of first occurrence—Group devices based on the time that a given threat was first quarantined
- Time of last occurrence—Group devices based on the time that a given item was last quarantined
Spam top domains
- Count—Group devices based on whether they have received a certain number of spam emails from a given domain
- Domain—Group devices that log on to domains associated with the highest number of spam messages
Spam top recipients
- Count—Group devices based on whether they have received a certain number of spam emails
- Recipient—Group devices that receive the highest amount of spam email
Spam top senders
- Count—Group devices that have sent a certain number of spam emails
- Sender—Group devices that send the highest number of spam emails
Storage devices
- Storage capacity [MB]—Group devices based on storage capacity in MB
- Storage encryption status—Group devices based on whether they use encrypted or un-encrypted storage
- Storage ID—Group devices based on the ID of their primary storage device
- Storage type—Group devices based on the presence of a specific type of storage. Select Compact disc, Local disk, Network drive, Removable disk, or unknown drive type
Storage devices capacity
- Free space [%]—Group devices based on the amount of free space available in percent
- Free space [MB]—Group devices based on the amount of free drive space available in MB
- Storage ID—Group devices based on the ID of their primary storage device
Time zone
- Time zone—Group devices based on the time zone they use
- Time zone offset [minutes]—Group devices based on the time zone offset they use in minutes
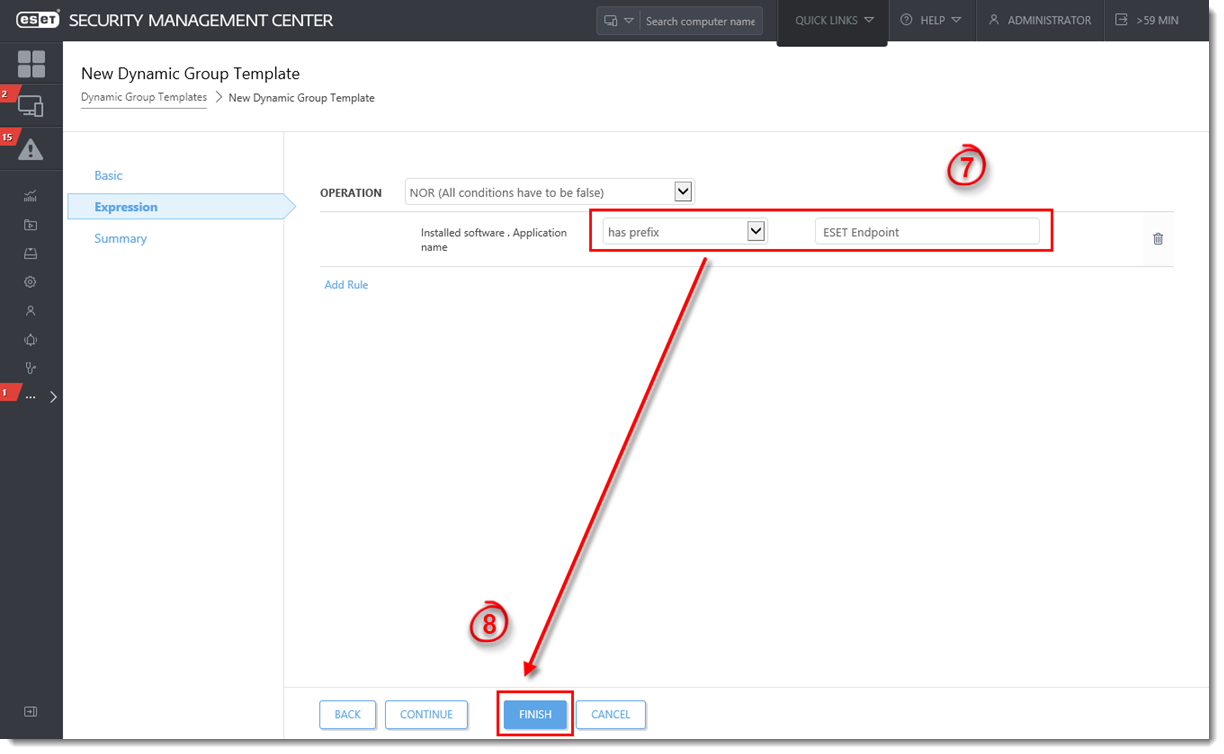
For example, expand Installed software, select Application name and then click OK.
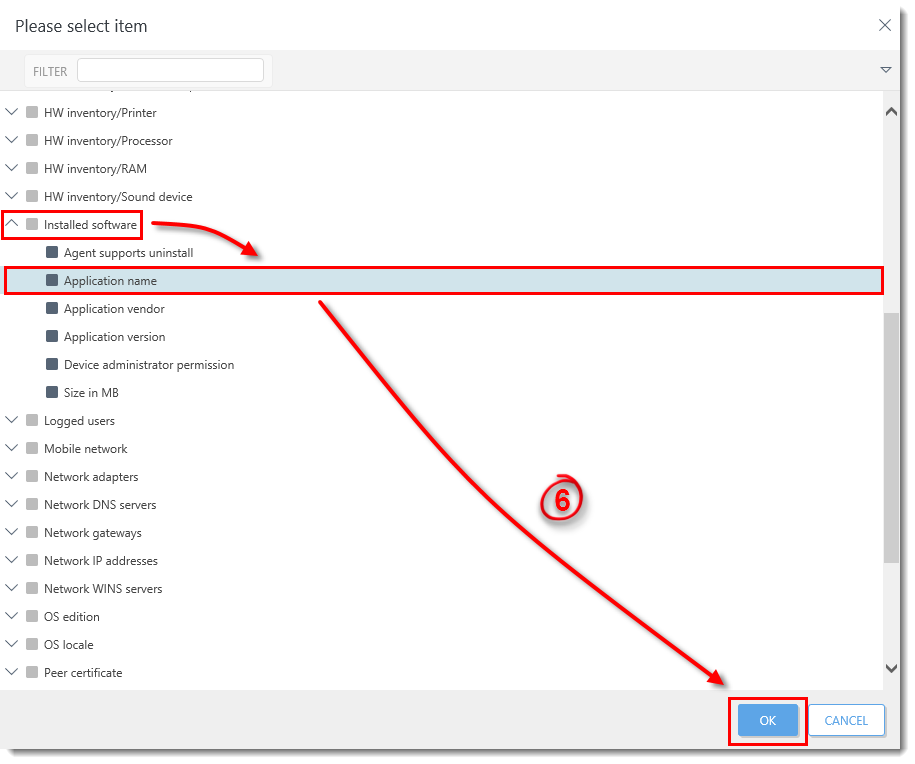
Figure 1-4
- Select has prefix from the drop-down menu and type ESET Endpoint into the blank field. This expression will recognize any application with a name that begins with ESET Endpoint.
- Click Finish when you are finished making changes. If you are editing a template associated with an existing dynamic group, ESMC will automatically recognize when a new computer meets the criteria defined in a Dynamic Group template and add it to the appropriate Dynamic Group.
If this is a new template, create a dynamic group using the template you just created.
Figure 1-5
Click the image to view larger in new window
Languages
Please contact your local support agent if you would like us to translate this article.
Related articles:
- Create a new certificate for new workstations to automatically join a Dynamic Group in ESET Security Management Center (7.x)
- Configure ESET Security Management Center to automatically deploy ESET endpoint products to unprotected computers (7.x)
- Create a dynamic group template for managed computers without an ESET security product (7.x)
- Create dynamic group templates in ESET Remote Administrator (6.x)
- Useful Dynamic Group template examples in ESET Security Management Center 7
- Create Dynamic Group templates in ESET PROTECT
Source : Official ESET Brand
Editor by : BEST Antivirus KBS Team
How useful was this post?
Click on a star to rate it!
Average rating 0 / 5. Vote count: 0
No votes so far! Be the first to rate this post.