|
When you select a computer from the list of computers, a window is displayed with details of the hardware and software installed, as well as the security settings assigned to it.
The Details window is divided into five sections:
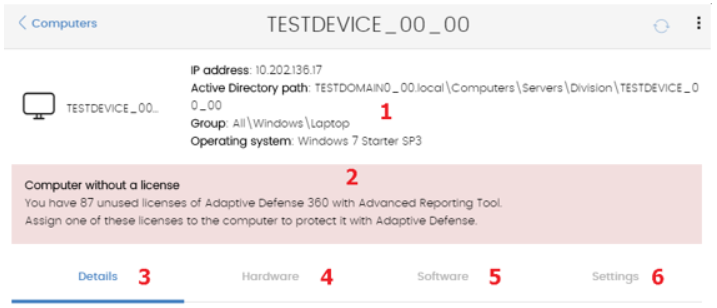
Click on the plus sign to expand the content of each section.
This displays information to help identify the computer, such as the computer name, the IP address, group the computer belongs to and operating system.
- Unprotected computer:
- Protection disabled: A message is displayed stating that the antivirus protection, Adaptive Defense (advanced) protection, or Exchange protection is disabled. You are advised to assign protection settings to the computer with the protection enabled.
- Protection with errors: A message is displayed stating that the antivirus protection, Adaptive Defense (advanced) protection, or Exchange protection has an error. Restart the computer or reinstall the software.
- Installation error: The computer is unprotected because there was an error during installation.
- Installation in progress: The computer is unprotected because the installation of Adaptive Defense 360 is incomplete. Wait a few minutes until the installation is complete.
- Out-of-date computer:
- Computer pending restart: The update for the security engine has been downloaded but the computer needs to be restarted for it to be applied.
- Protection updates disabled: The software won?t receive any improvements. This will jeopardize the security of the computer in the future. See chapter Creating and managing settings to learn how to create and assign ?Per-computer settings? that allow the software to be updated.
- Knowledge updates disabled: The software won?t receive any updates to the signature file. This will jeopardize the security of the computer in the short-term.
- Knowledge update error: The download of the signature file failed. There is an explanation in this chapter of how to check the free space on your hard disk. See chapter Computer restartfor more information about how to restart your computers remotely.
- Blocked files
The computer contains unknown files that are in the process of classification and cannot be run. See the Currently blocked programs being classified panel in the dashboard to check those files and add an exclusion if necessary. See chapter Managing quarantined items and items being classified.
- Offline since?
The computer has not connected to the Panda Security cloud in several days. Check the connectivity of the computer and the firewall settings. Check if the computer meets the necessary connectivity requirements.
- Pending restart
The administrator has requested a restart which has not yet been applied.
- Computer: Displays information about the device settings provided by the Aether agent.
- Name: Computer name
- Description: Descriptive text provided by the administrator
- IP addresses: List of all the IP addresses (main and alias)
- Domain: Windows domain that the computer belongs to. This is empty if it does not belong to a domain.
- Active Directory path: The path of the computer in the Active Directory tree.
- Group: The group within the Groups tree to which the computer belongs. To change the computer?s group, click Change. Operating system Mail server: Version of Microsoft Exchange server installed on the computer. Virtual machine: This indicates whether the computer is physical or virtual.
- Licenses: The Panda Security product licenses installed on the computer. For more information, refer to chapter License management. Agent version Installation date Last connection of the agent to the Panda Security infrastructure. The communications agent will connect at least every four hours.
- Security: This section indicates the status (Enabled, Disabled, Error) of the Adaptive Defense 360 technologies: Adaptive Defense File Antivirus, Mail, Antivirus, Web Browsing Antivirus, Firewall Protection, Device Control, Web Access Control, Protection, Version, Knowledge, Version.
- CPU: Information about the processor on the computer, and a graph with CPU consumption at five minute intervals over the last hour.
- Memory: Information about the memory chips installed, and a graph with memory consumption at five minute intervals over the last hour.
- Disk: Information about the mass storage system, and a pie chart with the percentage of free/used space at that moment.
- Name: Program name
- Publisher: Program developer
- Installation date
- Size
- Version
- Search tool: Tool that enables you to locate software packages using partial or complete matches in all the fields shown previously. The drop-down menu lets you restrict the search to only updates, installed software or both.
- Change log: The change log lists all the software installation and uninstallation events that take place within the configured date range. For each event, the following information is displayed:
- Event: Install or uninstall.
- Name: Name of the software package that triggered the event.
- Publisher: The program developer
- Version
- Date
- Computers used by people with different levels of IT knowledge require different levels of permissiveness with respect to the running of software, access to the Internet or to peripherals.
- Users with different tasks to perform and therefore with different needs require settings that allow access to different resources.
- Users that handle confidential or sensitive information require greater protection against threats and attempts to steal the organization?s intellectual property.
- Computers in different offices require settings that allow them to connect to the Internet using a variety of communication infrastructures.
- Critical servers require specific security settings.

