In addition to the built-in reports available in Malwarebytes Nebula, you can send threat-related events to your SIEM solution for security insights, compliance, and visibility. This article provides the steps required to set up Syslog for Malwarebytes Nebula.
Events flow
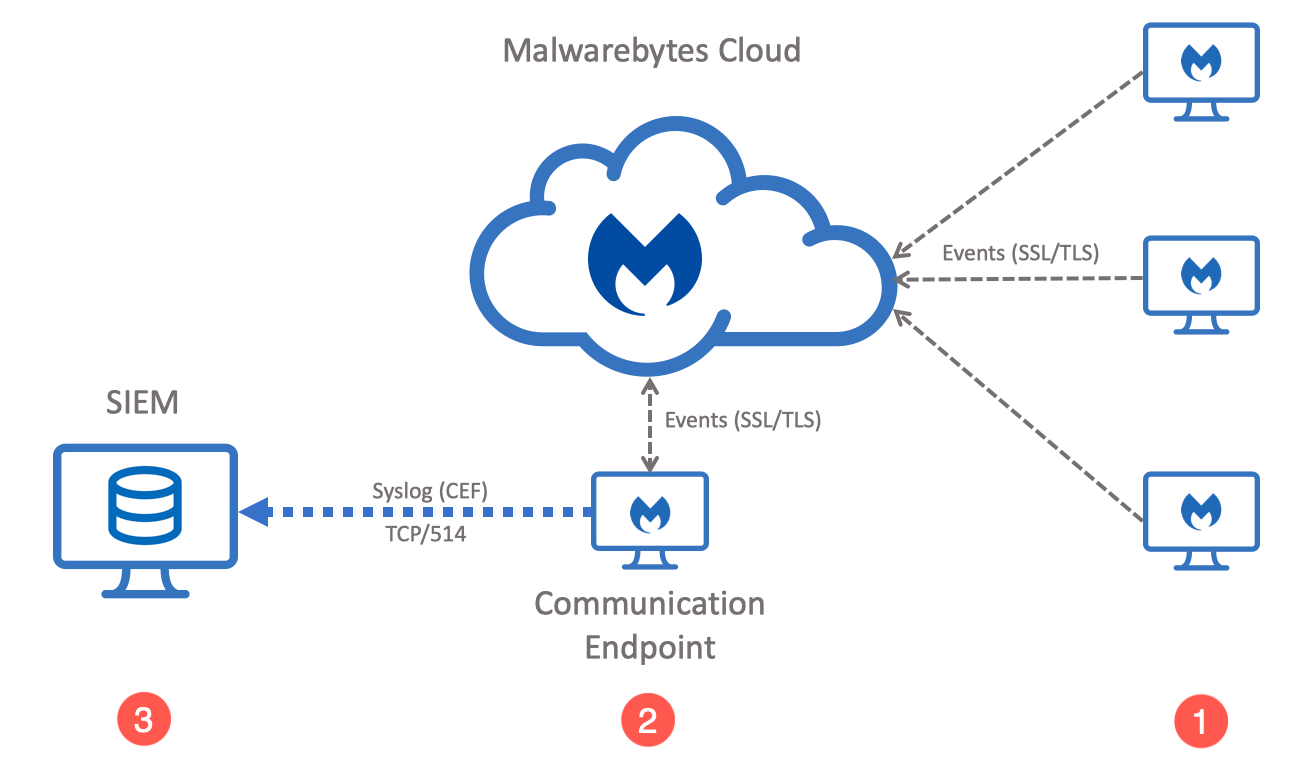
The diagram below represents the Malwarebytes events flow. The flow follows this order:
- Endpoints report threat detection, quarantine, and other events to Malwarebytes Nebula.
- Malwarebytes Syslog Communicator Endpoint pulls events from Malwarebytes Nebula.
- Communication Endpoint forwards events to Syslog server in CEF format.
Requirements
- Active subscription or trial for a Malwarebytes Nebula platform product:
- Malwarebytes Endpoint Detection and Response
- Malwarebytes Endpoint Protection
- Malwarebytes Incident Response
- Network access between one of your Malwarebytes Syslog communication endpoints and SIEM or Syslog server. TCP over port 514 is used by default.
Configuration
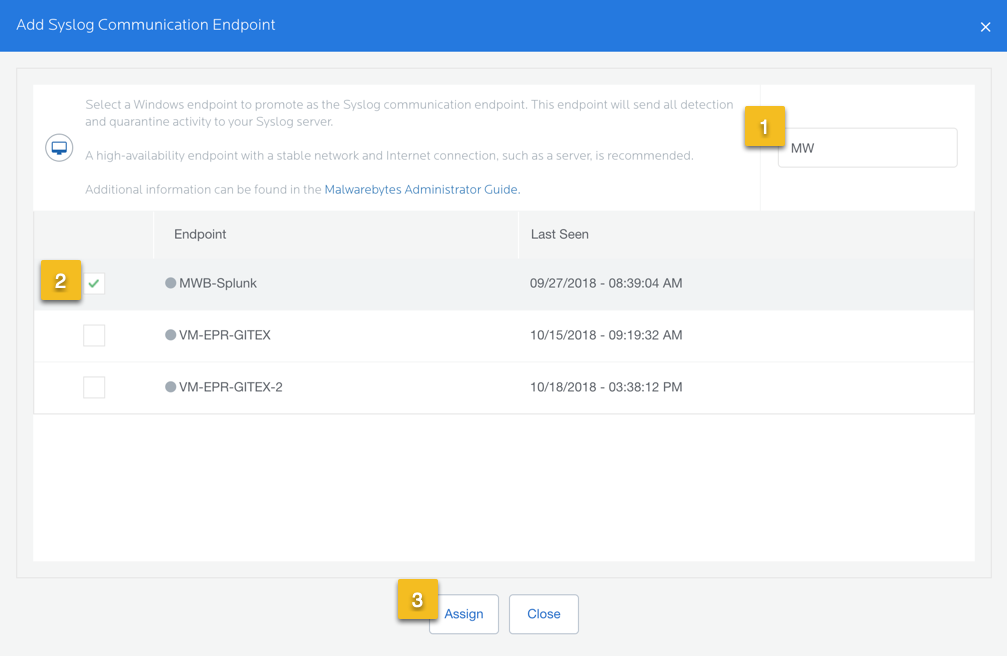
- Go to Settings > Syslog Logging.
- Click Add. Promote one of your Windows endpoints as the Syslog communication endpoint.
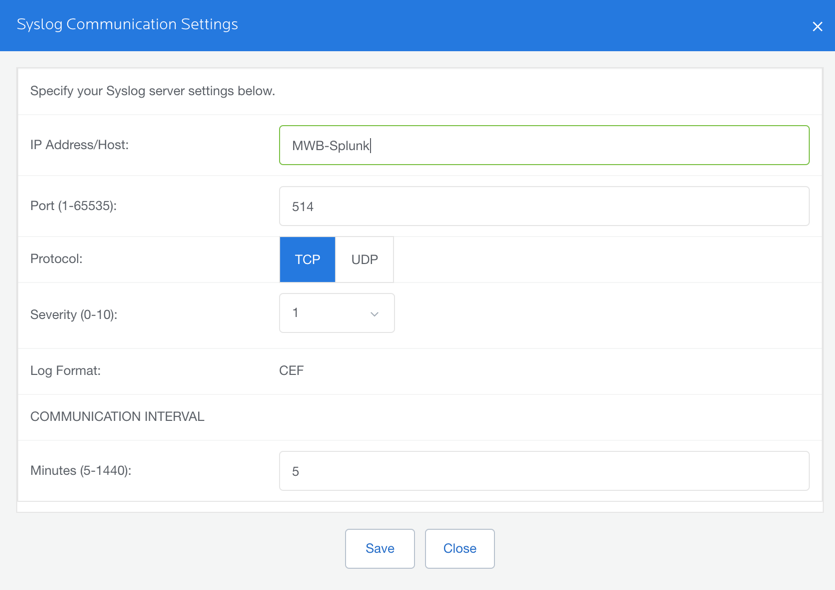
- In the top-right corner, click Syslog Settings.
- Fill in the following information, then click Save.
- IP Address/Host: IP or hostname of your Syslog server.
- Port: Port you have specified on your Syslog server.
- Protocol: Select either TCP or UDP protocol.
- Severity: Choose a Severity from the list. This determines the Severity of all Malwarebytes events sent to Syslog.
- Communication Interval (Minutes): Determines how often the communication endpoint gathers Syslog data from the Malwarebytes server. If the endpoint is unable to contact Malwarebytes, it buffers data from the last 24 hours. Data older than 24 hours is not sent to Syslog.
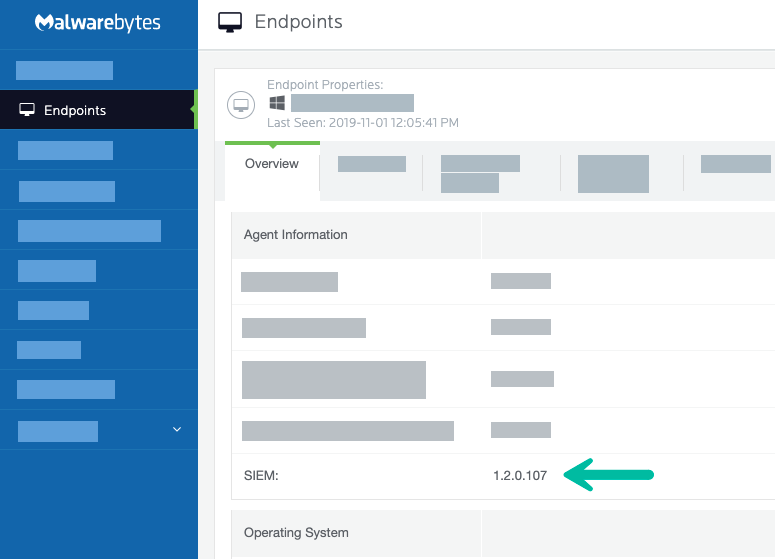
- Navigate to Endpoints. Click on the Syslog communication endpoint you assigned in Step 2.
- In the Agent Information section, the SIEM version number displays. This confirms the SIEM plugin has activated on the endpoint.
The endpoint transfers data to Syslog without further configuration.
Change Syslog settings
If you need to change your Syslog communication endpoint, perform the following:
- Go to Settings > Syslog Logging.
- Click Remove to demote the existing endpoint.
- Click Add to promote a new endpoint. See the steps above in the Configuration section.
You may temporarily demote a communication endpoint using the On/Off toggle on this screen. Temporarily demoting a communication endpoint can be useful when troubleshooting your Syslog settings.
Example Syslog entry
Following is an example of a Syslog entry generated by Malwarebytes in raw CEF format. The tables below detail the Syslog prefix values, CEF headers, and extensions used in the example.
2018-04-13T21:06:05Z MININT-16Tjdoe CEF:0|Malwarebytes|Malwarebytes Endpoint Protection|Endpoint Protection 1.2.0.719|Detection|Website blocked|1|deviceExternalId=e150291a2b2513b9fd67941ab1135afa41111111 dvchost=MININT-16Tjdoe deviceDnsDomain=jdoeTest.local dvcmac=00:0C:29:33:C6:6A dvc=192.168.2.100 rt=Apr 13 2018 21:05:56 Z fileType=OutboundConnection cat=Website act=blocked msg=Website blocked\\nProcess name: C:\\Users\\vmadmin\\Desktop\\test.exe filePath=drivinfosproduits.info(81.171.14.67:49846) cs1Label=Detection name cs1=Malicious Websites
| Syslog Prefix | Description | Examples |
|---|---|---|
| Timestamp | Time of recorded event | 2018-04-13T21:06:05Z |
| Host | Affected endpoint | MININT-16Tjdoe |
|
CEF Header |
Description | Examples |
|---|---|---|
| Version | Version of the CEF format | CEF:0 |
| Device Vendor | The vendor will always be Malwarebytes | Malwarebytes |
| Device Product | Plugin installed on endpoint at time of event | Malwarebytes Endpoint Protection Malwarebytes Incident Response Malwarebytes Endpoint Detection and Response |
| Device Version | Plugin name and version | Endpoint Protection 1.2.0.719 |
| Device Event Class ID | Type of event reported | Detection |
| Name | Category of event and action taken | Website Blocked |
| Severity | Severity set in Syslog settings | 1 |
| Extension | Description | Examples |
|---|---|---|
| deviceExternalId | Unique identifier of device generating event | e150291a2b2513b9fd67941ab1135afa41111111 |
| dvchost | Device hostname | MININT-16Tjdoe |
| deviceDnsDomain | Device’s DNS domain name | jdoeTest.local |
| dvcmac | Device’s MAC address | 00:0C:29:33:C6:6A |
| dvc | Device’s IPv4 address | 192.168.2.100 |
| rt | Date/Time when the event occurred | Apr 13 2018 21:05:56 Z |
| fileType | Type of file that caused event | OutboundConnection File Module Process Registry Value Exploit |
| cat | Category of the event | Malware PUP PUM Ransomware Exploit Website Suspicious Activity |
| act | Action Taken | blocked found quarantined deleted restored |
| msg | Details of the system event | Website blocked\nProcess name: C:\Users\vmadmin\Desktop\test.exe |
| filePath | Path to the file, or blocked website domain | drivinfosproduits.info(81.171.14.67:49846) C:\users\vmadmin\Desktop\test.exe |
| cs1Label | The name label for the field cs1 | Detection name |
| cs1 | The detection name | Malicious Websites |
| cs2Label | The name label for the field cs2 | Detection severity |
| cs2 | Severity of detection | High, medium, low |
Return to the Malwarebytes Nebula platform Administrator Guide.
Source : Official Malwarebytes Brand
Editor by : BEST Antivirus KBS Team

