Issue
- Configure ESET Remote Administrator 6.5 or later to manage iOS devices using ESET Mobile Device Management
Details
Benefits of ESET MDM for iOS & iPadOS:
- Ability to manage the security of iOS devices from ERA 6
- Manage key security aspects of iOS: passcode settings, auto-lock time, device restrictions for camera usage, and settings for iCloud usage
- Anti-Theft: remotely wipe all device data if a device is lost (including emails and contacts)
- Push Exchange account, Wi-Fi account, VPN, and other related settings in batches to iOS devices
- ERA MDM 6.5 supports Apple Device Enrollment Program (DEP) which provides a supervised mode for device management
Solution
To enroll iOS devices in ESET Mobile Device Connector, follow the steps in each section:
- Create an MDM Certificate
- Create an APN/DEP Certificate
- Create an MDM Policy
- wp-signup.php your iOS device in ERA
- Enroll your iOS device
- Create an Activation task for iOS MDM
I. Create an MDM certificate
If you already have an MDM certificate (third-party HTTPS certificate signed by trusted Certification Authority, or certificate created in ERA and signed by ERA CA), proceed to Create an APN/DEP Certificate.
- Open ESET Remote Administrator Web Console (ERA Web Console) in your web browser and log in. How do I open ERA Web Console?
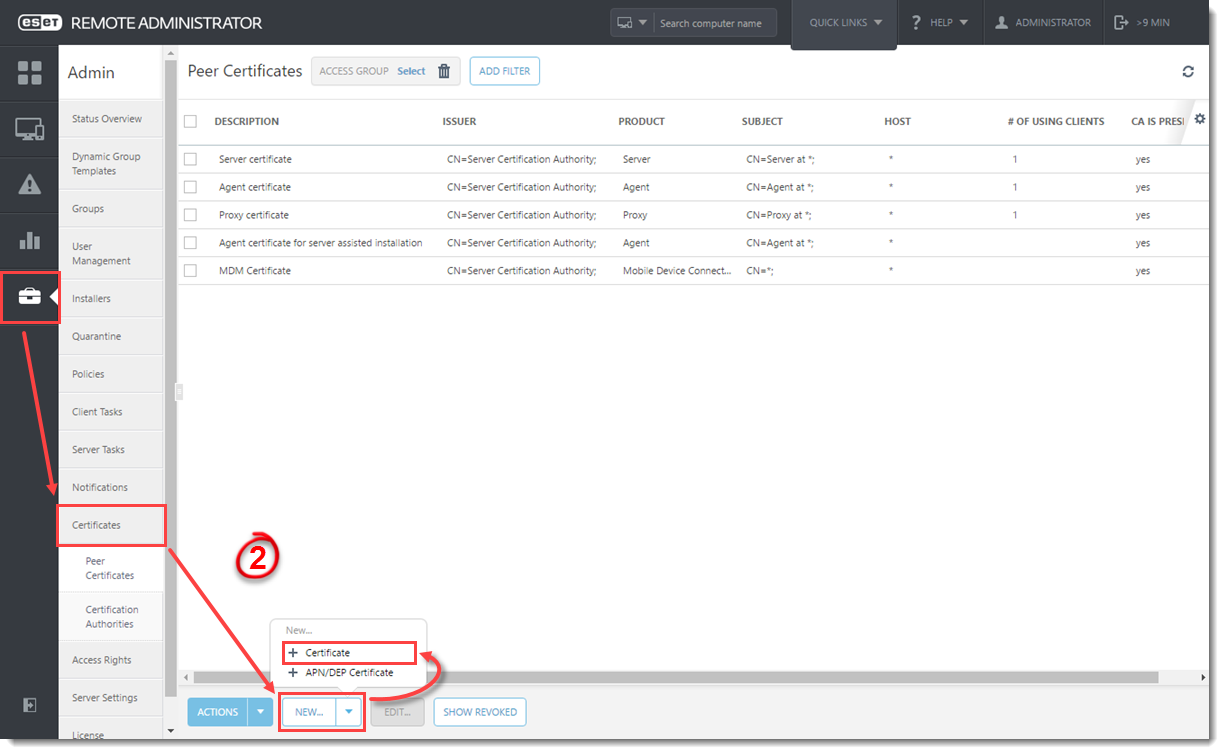
- Click
 Admin→ Certificates → New → Certificate.
Admin→ Certificates → New → Certificate.
Figure 1-1
Click the image to view larger in new window
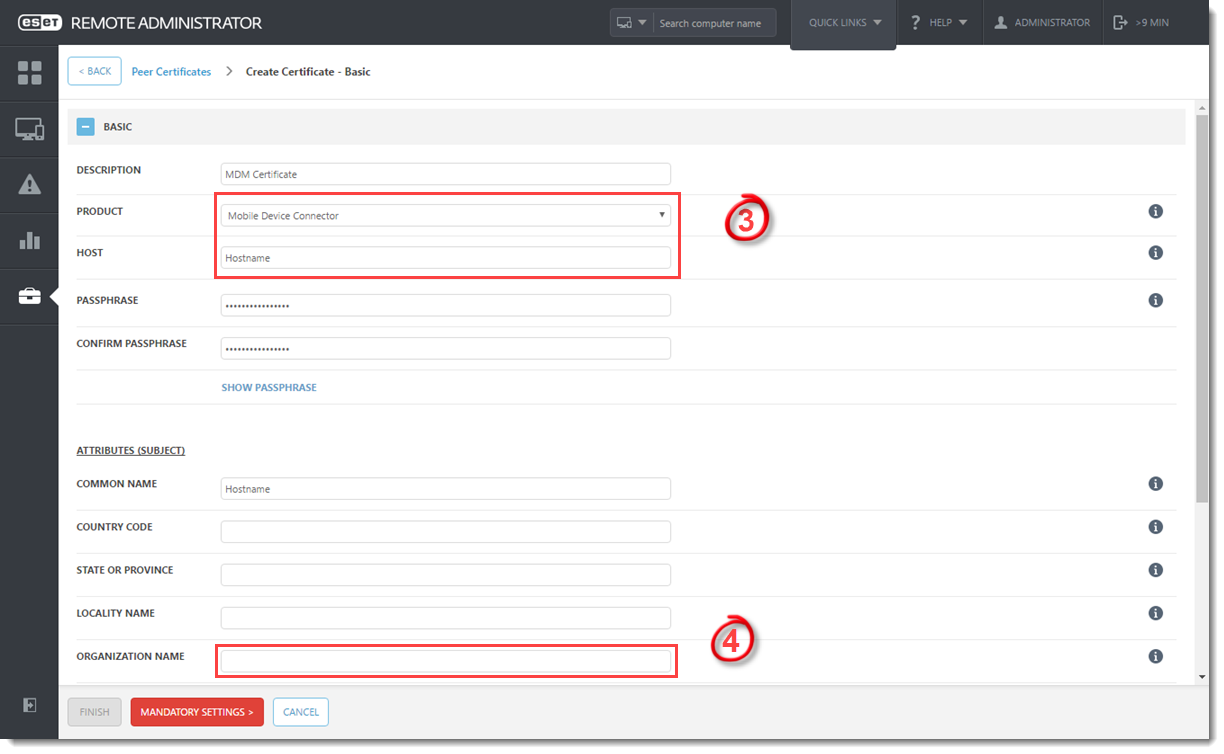
- In the Basic section, select Mobile Device Connector from the Product drop-down menu. Type the IP address or Hostname of the server where Mobile Device Connector is installed in the Host field.
If the MDM server does not have internet access and communications are port-forwarded from a router connected to an outside network, use the IP address or Hostname of that router instead. You can also enter the IP address from the HTTPS certificate.
- In the Attributes (Subject) section, type the organization name used in ESET Remote Administrator in the Organization Name field.
Figure 1-2
Click the image to view larger in new window
- Expand the Sign section and click Select Certification Authority.
Figure 1-3
Click the image to view larger in new window
- Select the certification authority that you want to use and click OK.
Figure 1-4
Click the image to view larger in new window
- Click Finish and proceed to Create an APN/DEP certificate.
II. Create an APN/DEP certificate
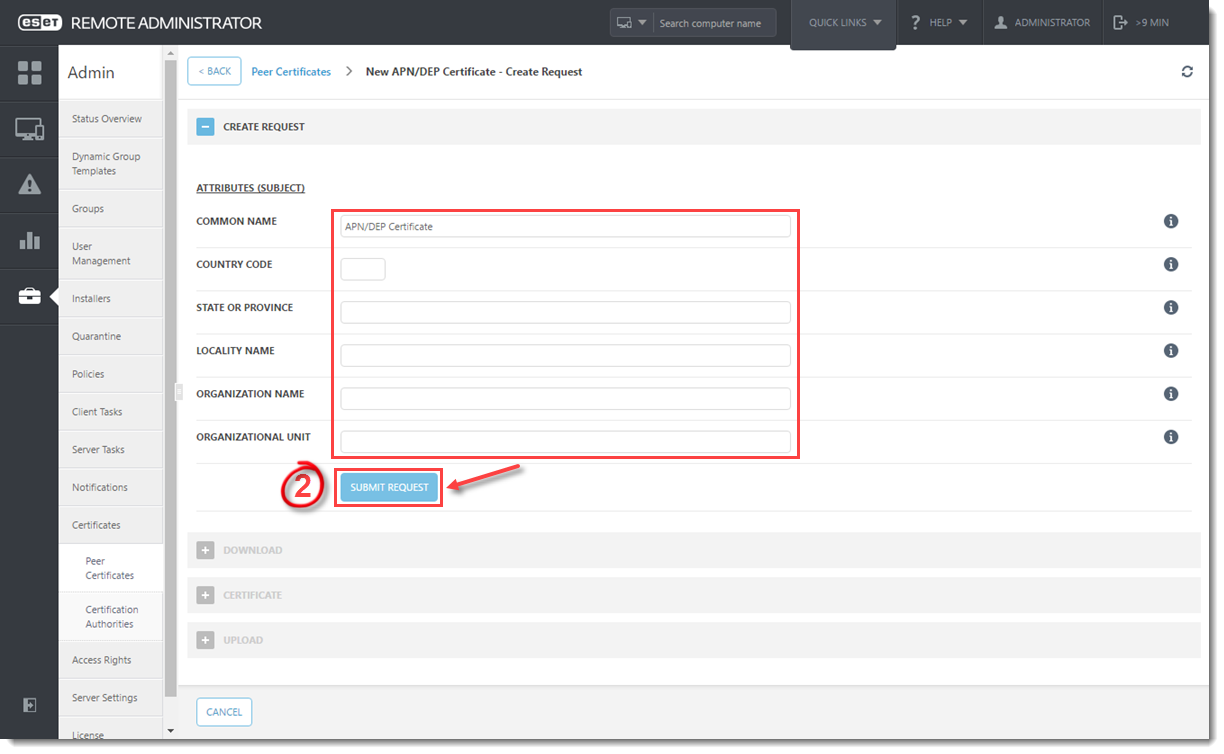
- Click Admin
 → Certificates → New → APN/DEP Certificate.
→ Certificates → New → APN/DEP Certificate. - Type or copy/paste in the certificate attributes and then click Submit Request.
Figure 2-1
Click the image to view larger in new window
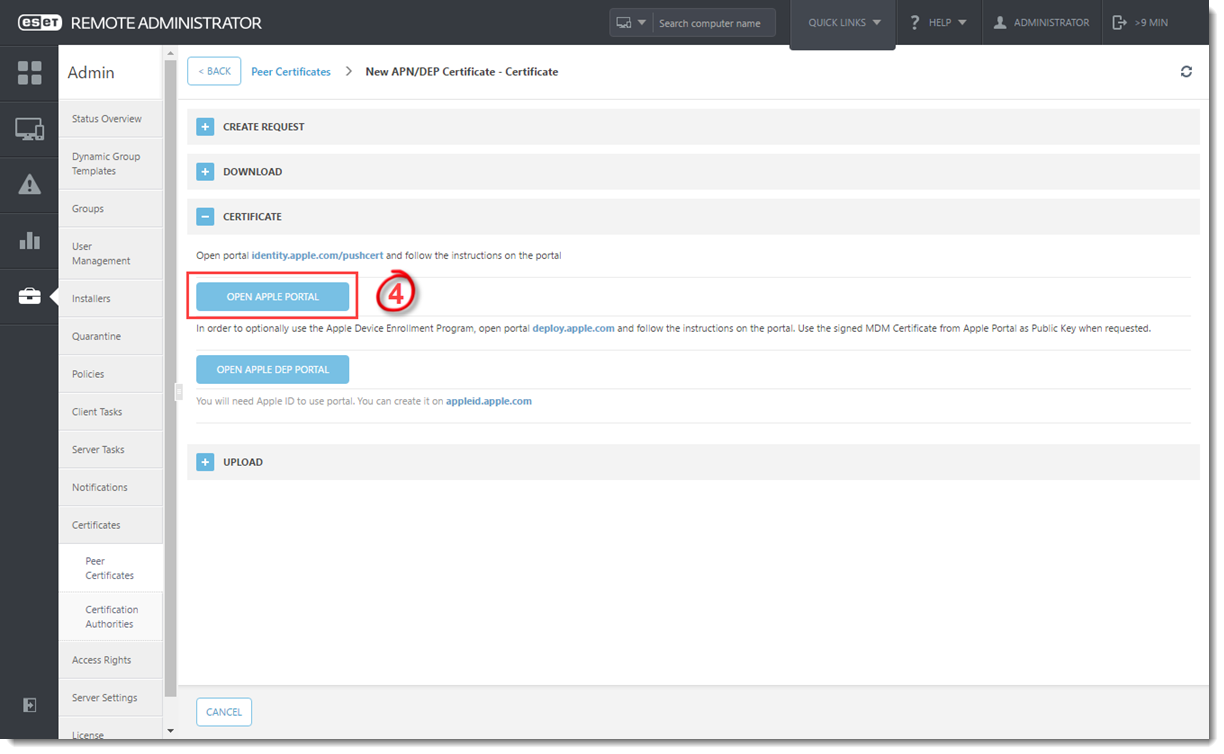
- Expand the Download section, click Download Private Key and Download CSR and save the certificates to your hard drive.
Figure 2-2
Click the image to view larger in new window
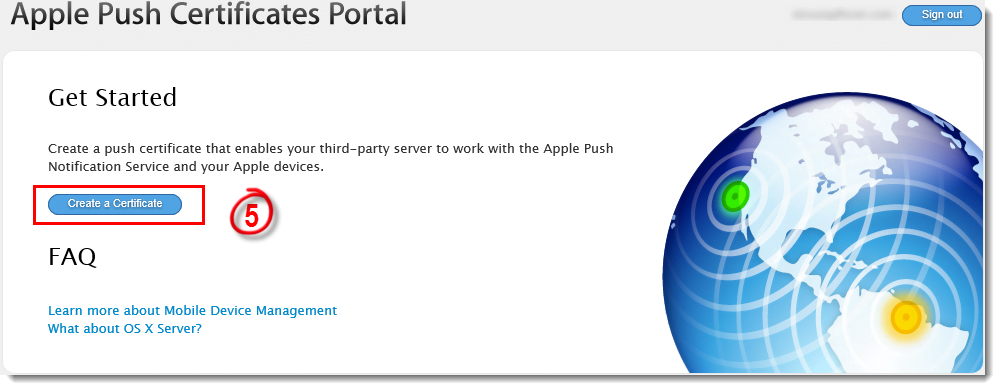
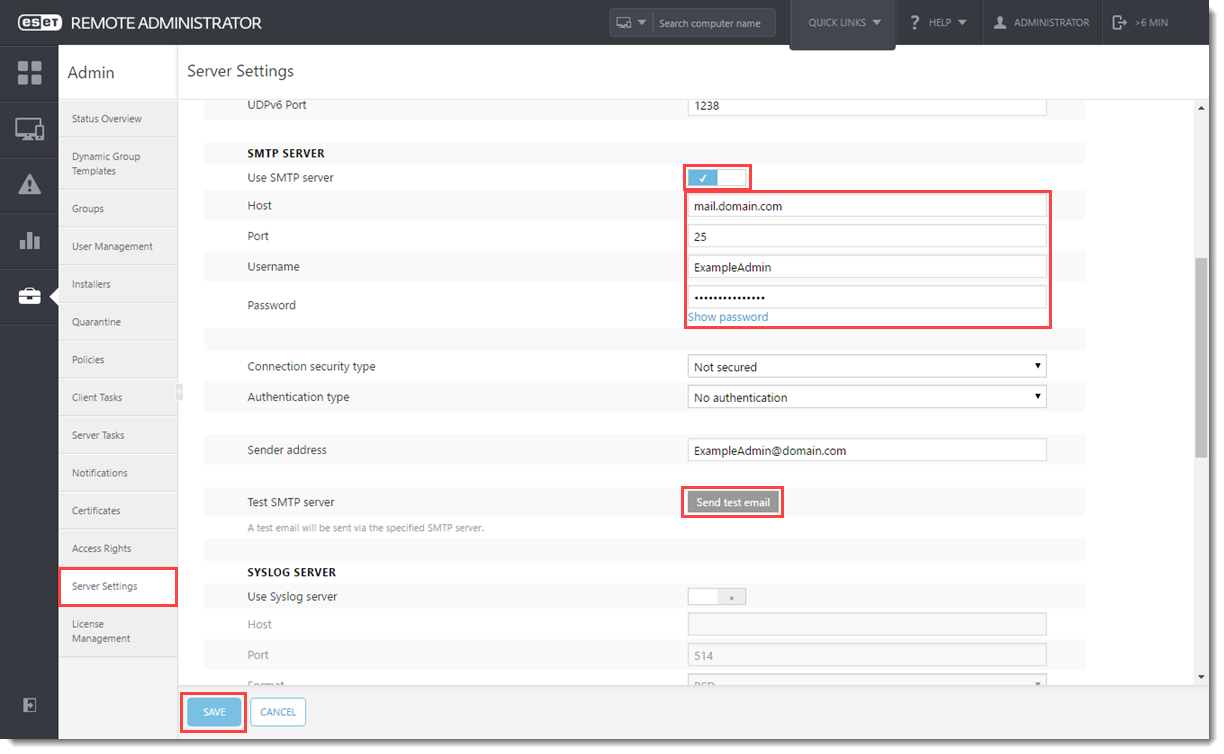
- Click Open Apple Portal or navigate to https://identity.apple.com/pushcert in your web browser and sign in with your Apple ID.
Figure 2-3
Click the image to view larger in new window
- Click Create a Certificate.
Figure 2-4
Click the image to view larger in new window
- If you agree to the Apple Push Certificate Portal Terms of Use, click Accept.
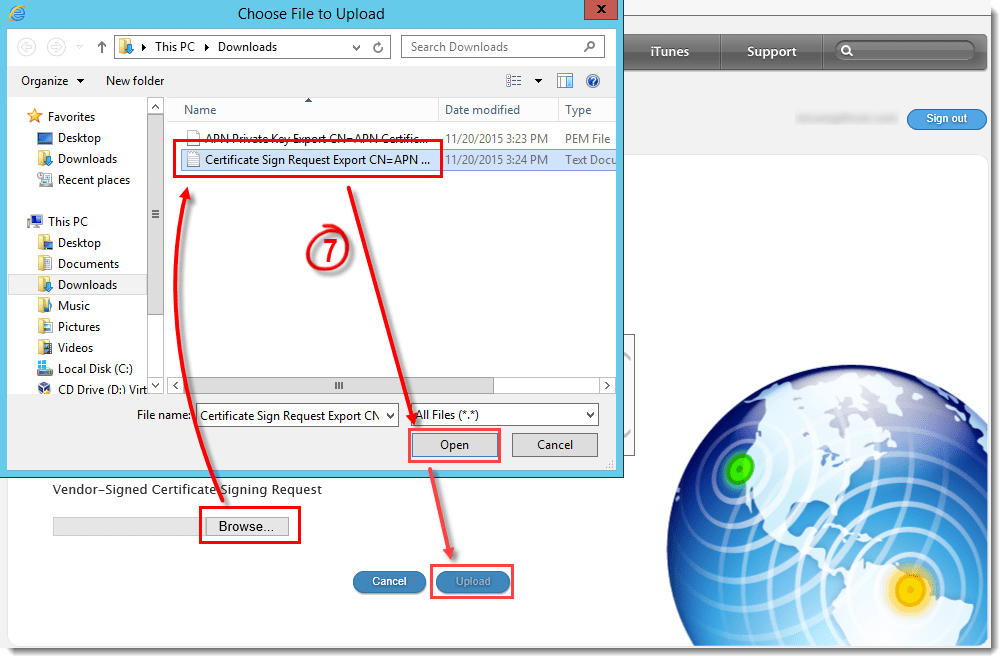
- Click Browse, select the CSR certificate you downloaded in step 3 above, click Open and then click Upload.
Figure 2-5
Click the image to view larger in new window
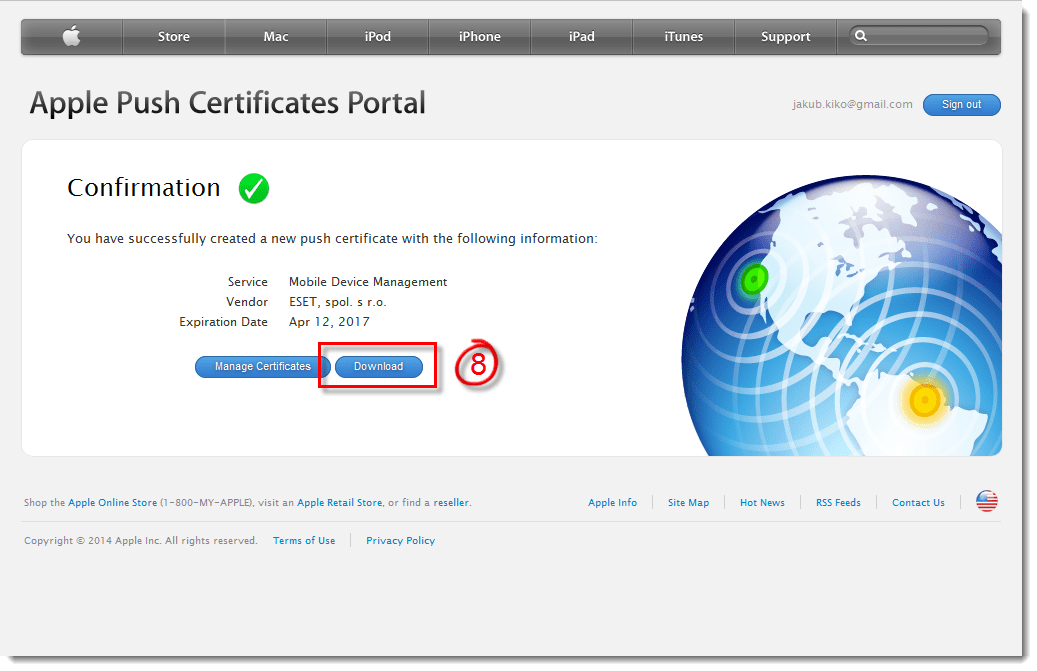
- After the upload completes (this may take time and it might be necessary to refresh the browser), click Download and save the certificate to your hard drive.
Figure 2-6
Click the image to view larger in new window
If you are completing a DEP enrollment, continue on to steps 9-12. If you are completing a non-DEP enrollment, proceed to Create an MDM Policy.
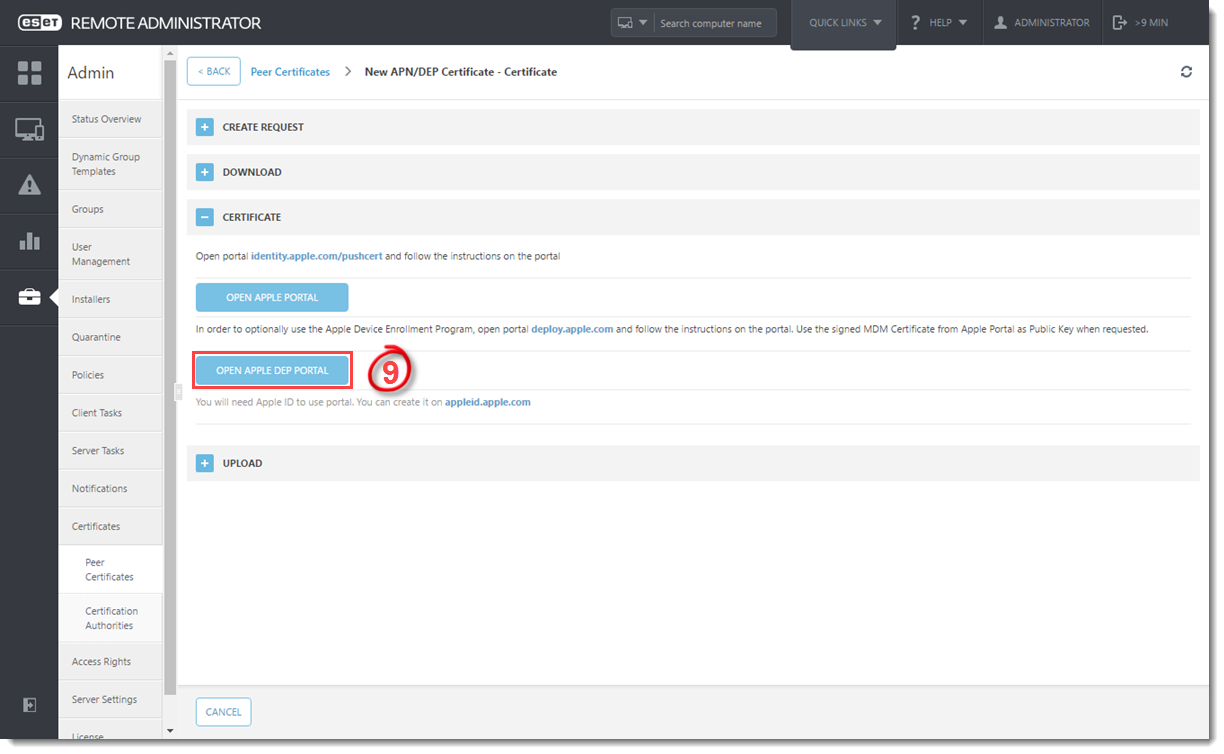
- Click Open Apple DEP Portal or navigate to https://deploy.apple.com in your web browser and sign in with your Apple DEP Account.
Figure 2-7
Click the image to view larger in new window
- Click Manage Servers → Add MDM Server. Type the MDM Server Name in the field and select the check box next to Automatically Assign New Devices if you want all new devices connected to your Apple DEP account to be assigned to this MDM server, and then click Next.
Figure 2-8
Click the image to view larger in new window
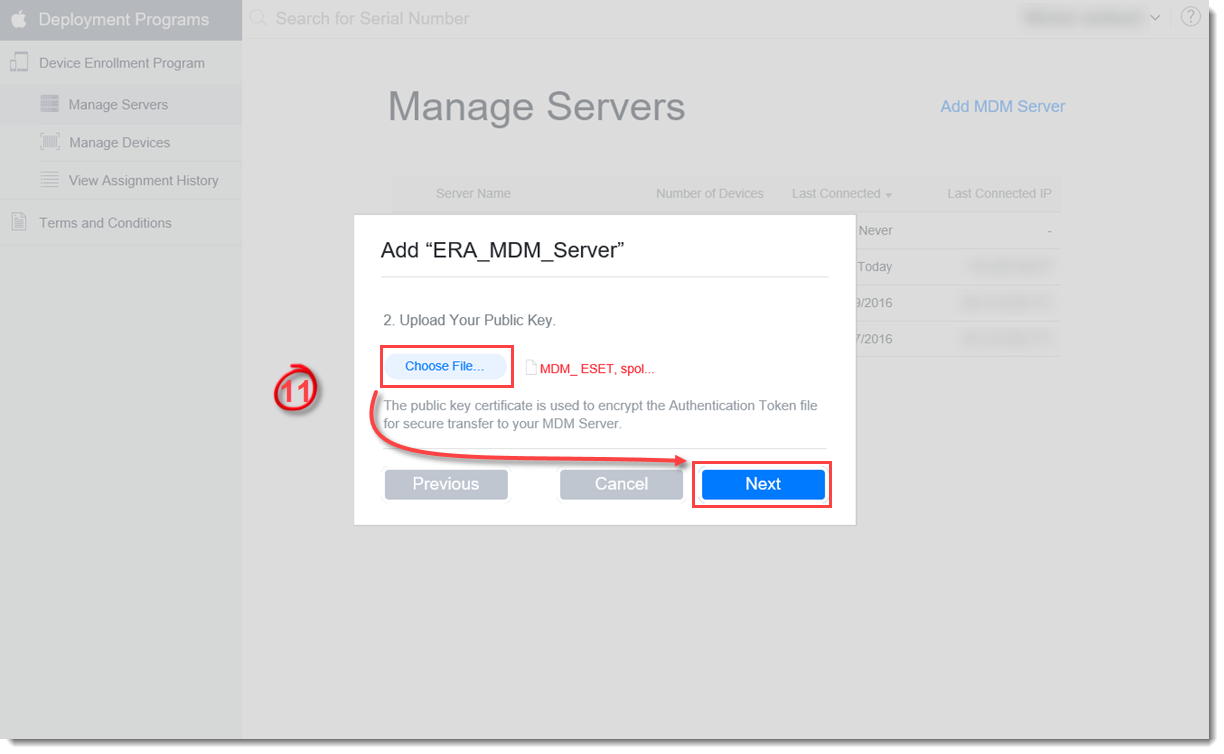
- Upload your public key (this is the Private key file you downloaded in step 3). Click Choose File, select the public key file, upload it and then click Next.
Figure 2-9
Click the image to view larger in new window
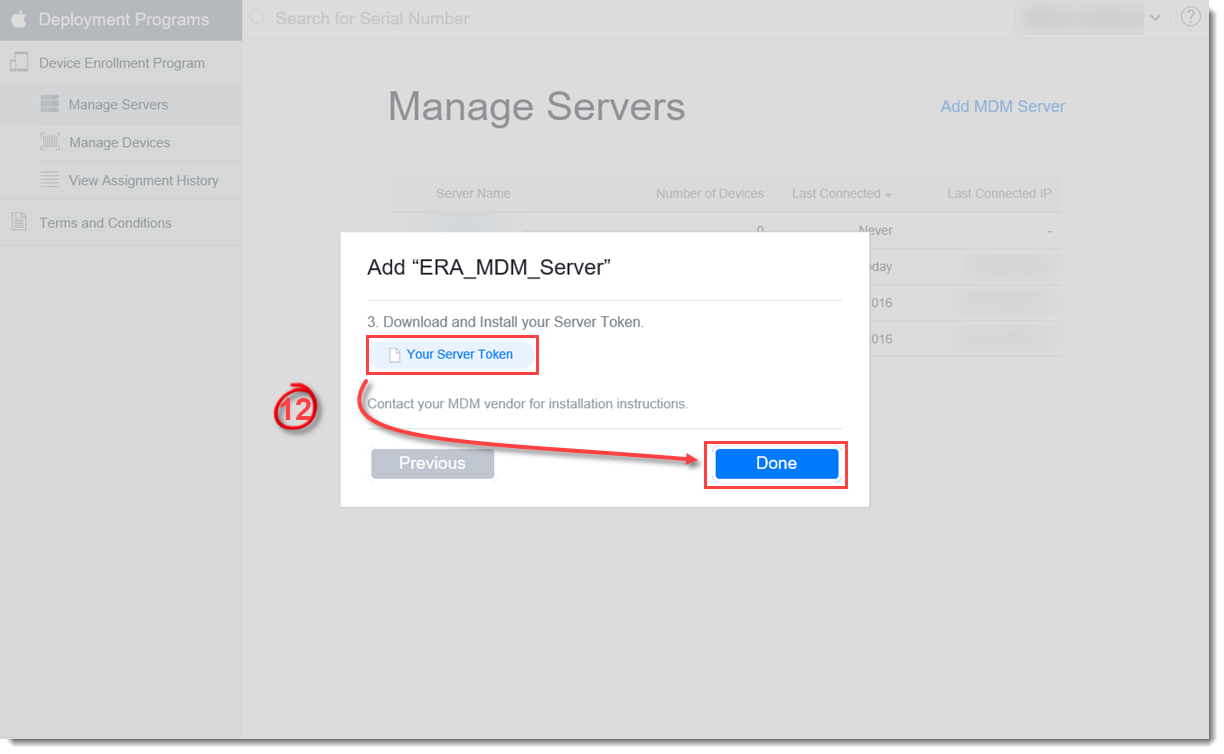
- Download the Apple DEP Server token. Click Your Server Token, save the file on your hard drive and click Done.
Figure 2-10
Click the image to view larger in new window
- Proceed to Create an MDM Policy
III. Create an MDM Policy
- Open ESET Remote Administrator Web Console (ERA Web Console) in your web browser and log in. How do I open ERA Web Console?
- Click Admin
 → Policies.
→ Policies. - Click New Policy.
Figure 3-1
Click the image to view larger in new window
- Expand Basic and type a name for the policy in the Name field (the Description field is optional).
- Expand Settings and select ESET Remote Administrator Mobile Device Connector from the drop-down menu.
Figure 3-2
Click the image to view larger in new window
- Type the IP address of the server where Mobile Device Connector is installed in the Hostname field. If the MDM server does not have internet access and communications are port-forwarded from a router connected to an outside network, use the IP address or Hostname of that router instead.
- Type the organization name used in ESET Remote Administrator in the Organization field. This name will be used by the enrollment profile generator to update the profile.
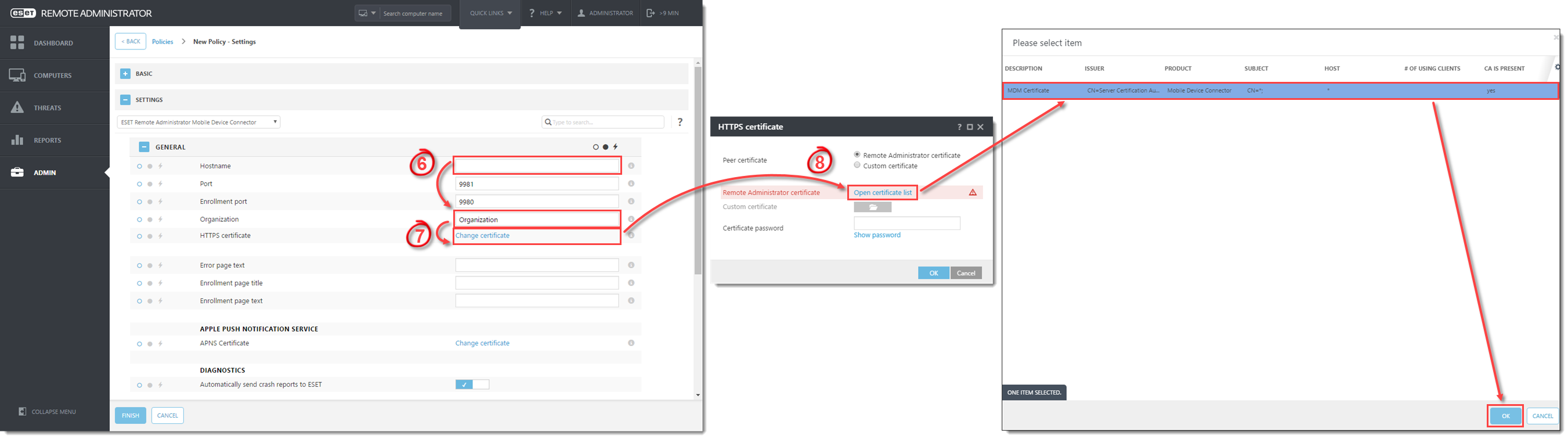
- In the HTTPS certificate section, click Change certificate → Open certificate list, select the MDM Certificate created in part II and then click OK.
Figure 3-3
Click the image to view larger in new window
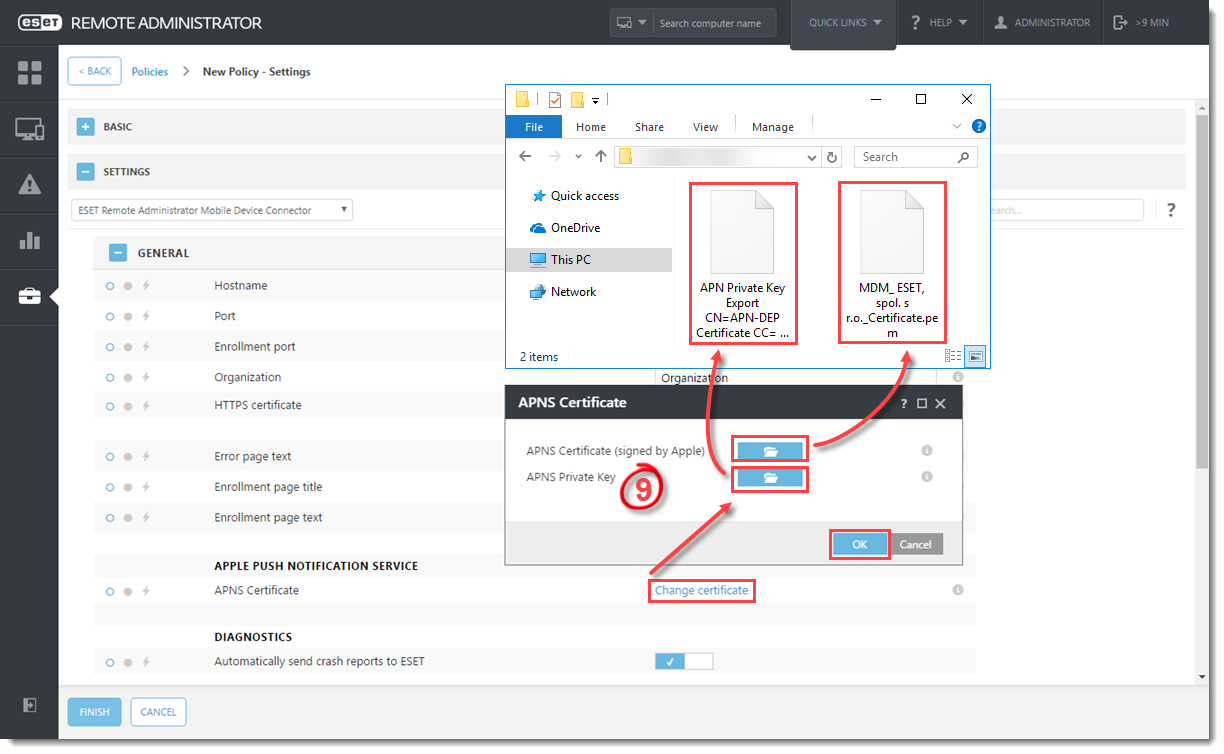
- In the Apple Push Notification Service section, upload the two Apple Push Notification Service files:
- APNS Certificate (signed by Apple) – this is the file downloaded from Apple’s portal, usually named:
MDM_ESET, spol. s.r.o._Certificate.pem
- APNS Certificate (signed by Apple) – this is the file downloaded from Apple’s portal, usually named:
- APNS Private Key – this is the file created in part II, step 3, usually named:
APN Private Key Export CN= ... .pem
Figure 3-4
Click the image to view larger in new window
If you are completing a DEP enrollment, continue on to steps 10-12. If you are completing a non-DEP enrollment, skip to step 12
- In the Apple Device Enrollment Program (DEP) section, click the file icon next to Upload authorization token and upload the Apple DEP Server Token – this file is usually named:
_Token_... .p7m. - Configure the MDC DEP settings.
- Supervised mode: provides all the DEP-only iOS policy settings and allows you to fully manage the iOS device.
- Mandatory Installation: requires iOS device users to install the MDM Profile. Users will be unable to use the iOS device without installing the MDM profile.
- Allow user to remove MDM profile: allows users to remove the MDM profile after it is installed. The iOS device must have the Supervised mode setting enabled to remove the option to remove the MDM profile. Click Edit next to Skip setup items to choose which of the initial setup steps during the initial iOS setup will be skipped. You can find more information about each of these steps in the Apple Knowledgebase Article.
Figure 3-5
Click the image to view larger in new window
- Expand the Assign section and click Assign to display all Static and Dynamic Groups and their members. Select the Mobile Device Connector instance to which you want to apply the policy and click OK.
Figure 3-6
Click the image to view larger in new window
When you are finished, proceed to wp-signup.php your iOS device in ERA.
IV. wp-signup.php your iOS device in ERA and send an enrollment link
If you are doing DEP enrollment, proceed here.
- Open ESET Remote Administrator Web Console (ERA Web Console) in your web browser and log in. How do I open ERA Web Console?
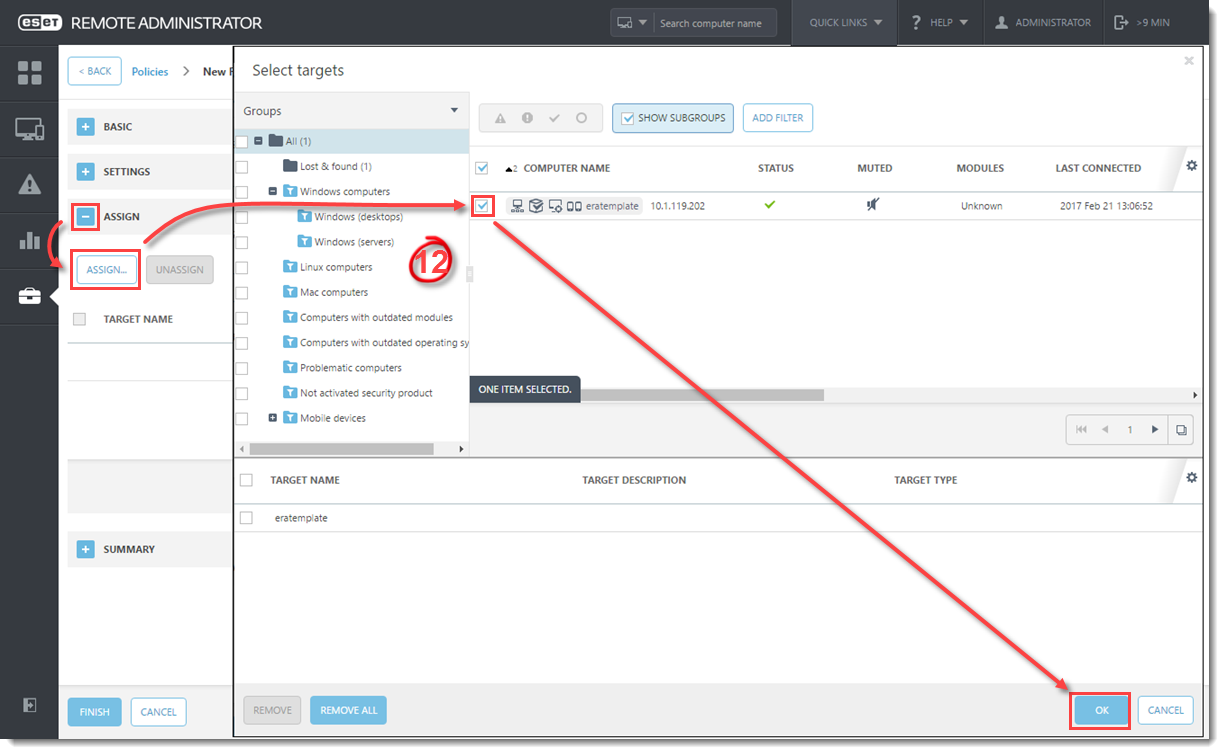
- Click Computers, select the group to which you want to add your mobile device and then click Add New → Mobile devices.
Figure 4-1
Click the image to view larger in new window
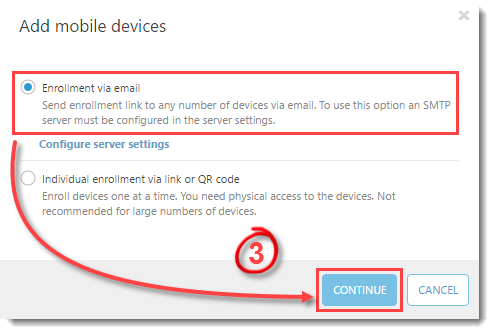
- In the Add mobile devices window, select Enrollment via email and click Continue. Click here for step-by-step instructions to enroll a single device at a time.
Figure 4-2
Click the image to view larger in new window
- In the General section, select the target for Mobile Device Connector, the ESET License that will be used for mobile device activation, and the Parent Group.
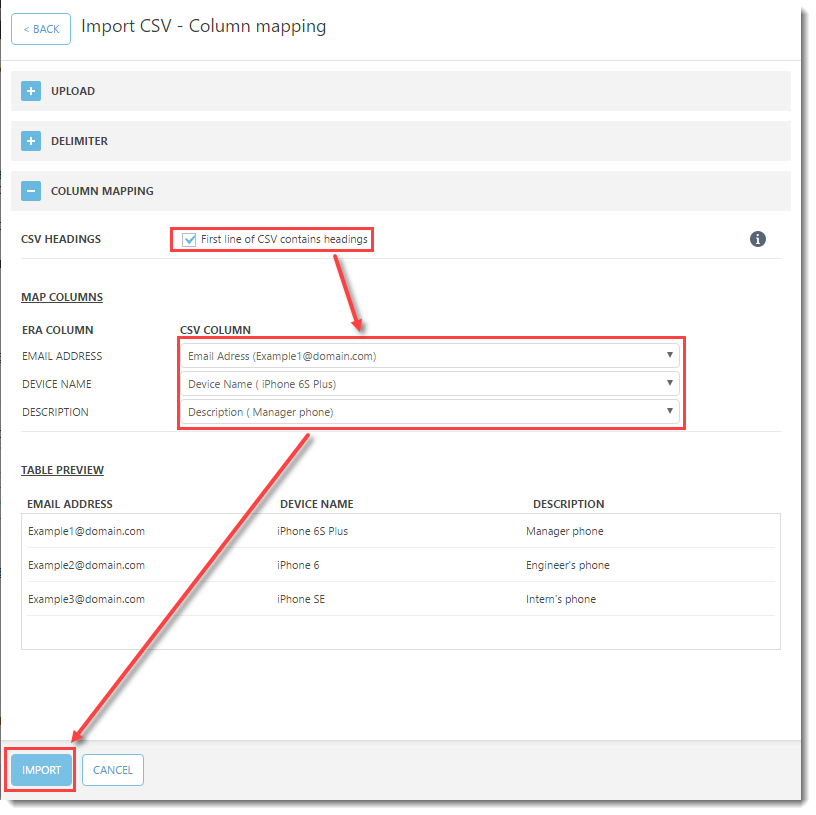
- In the List of Devices section, type in the Email Address (this email address will be used to deliver the enrollment email message), Device Name and Description. To assign a specific user, click Pair under Assigned User to match it to a designated policy. To add another row, click +Add device.
Figure 4-4
Click the image to view larger in new window
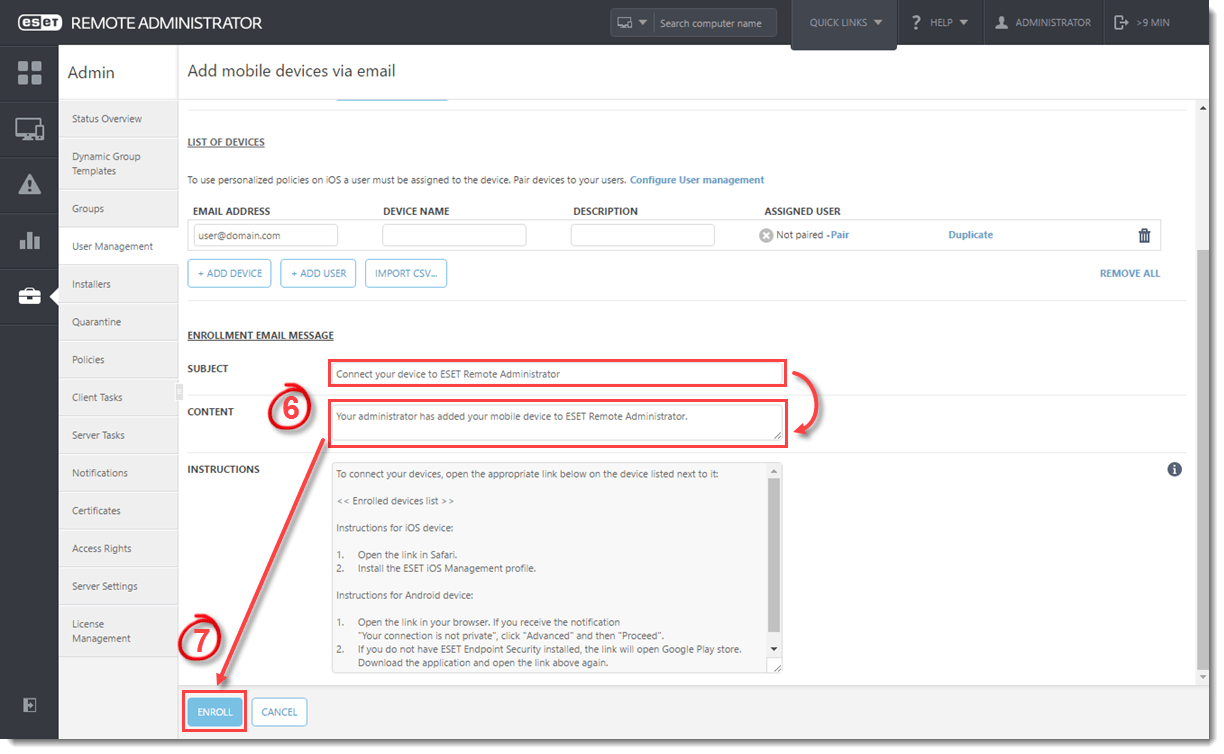
- When you have finished adding mobile devices, continue to the Enrollment Email Message section. Make any desired modifications to the Subject line and the Content section of the enrollment email message. The Instructions field displays the body of the enrollment email message with the steps that must be performed by the user on the mobile device.
Figure 4-8
Click the image to view larger in new window
- Click Enroll and proceed to Enroll your iOS device.
Enroll a single device
- Select Individual enrollment via link or QR code in the Add mobile devices window and click Continue.
Figure 4-9
Click the image to view larger in new window
- Type the Device name and Description in the appropriate fields, select the appropriate Mobile Device Connector and ESET License, and then click Next to proceed.
Figure 4-10
Click the image to view larger in new window
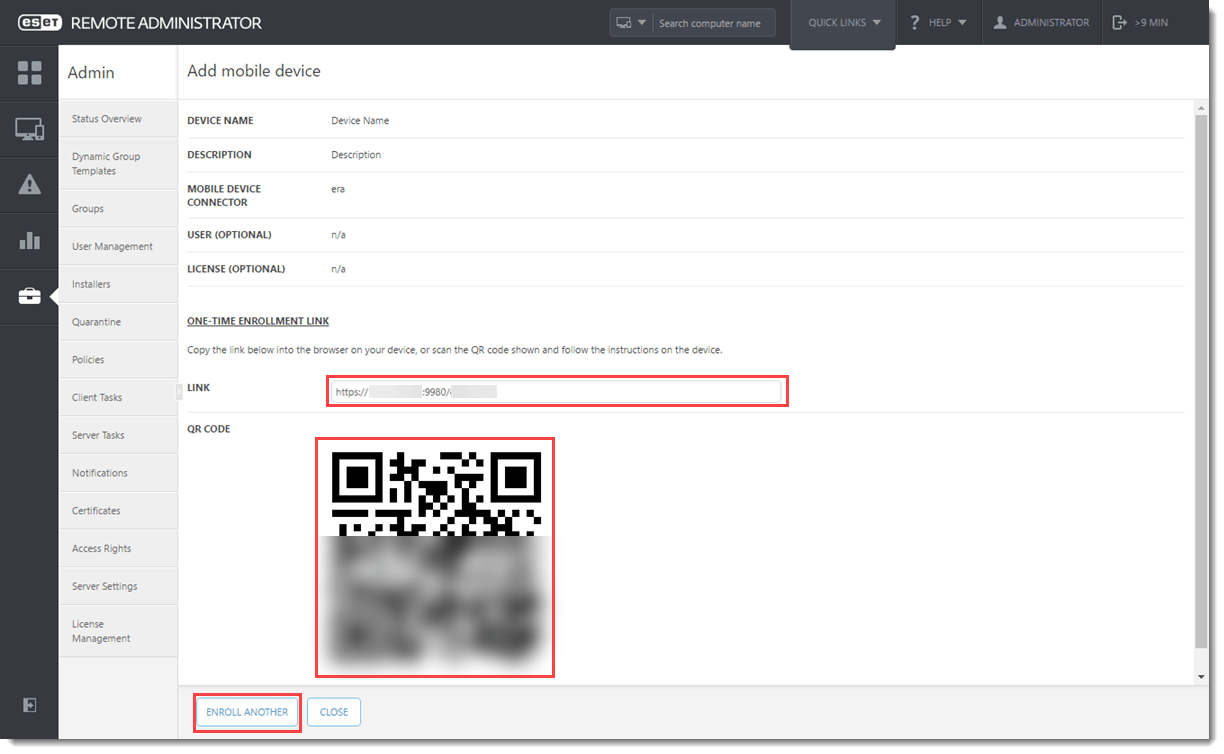
- The last preview window will display a summary of the enrollment, including the download link and QR code. Send the enrollment link to the mobile device using email or an instant messaging application if the device is not physically present. If the device is physically present, scan the QR code with the mobile device and proceed to Enroll your iOS device. To enroll another device, click Enroll Another and repeat step 2.
Figure 4-11
Click the image to view larger in new window
Add your DEP mobile device in the DEP portal and ERA
For DEP enrollment, you do not need to add the mobile device into ERA nor do you need to perform the mobile device enrollment. This will occur automatically; when the iOS device is added into DEP it is assigned to your MDM server. If you selected the Automatically Assign New Devices check box when you connected your MDM server with the DEP portal, all of the iOS devices assigned to your DEP account will automatically connect to the selected MDM server.
To add an iOS device manually, follow these steps:
- Log in to the DEP portal (deploy.apple.com).
- Click Device Enrollment Program → Manage Devices from the menu on the left.
- Choose from the following three options to add an iOS device into the DEP portal.
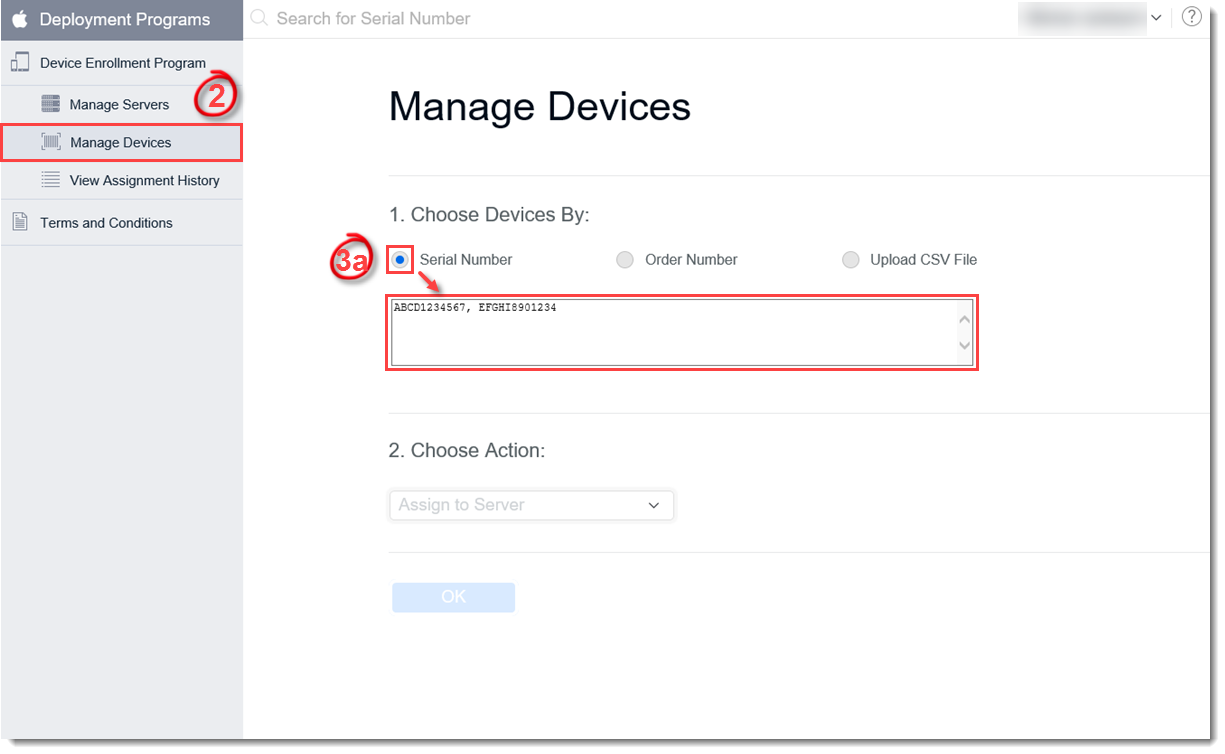
- Serial Number – type in the serial numbers of iOS devices you want to add (separated by commas) in the field and proceed to the next step.
Figure 4-12
Click the image to view larger in new window
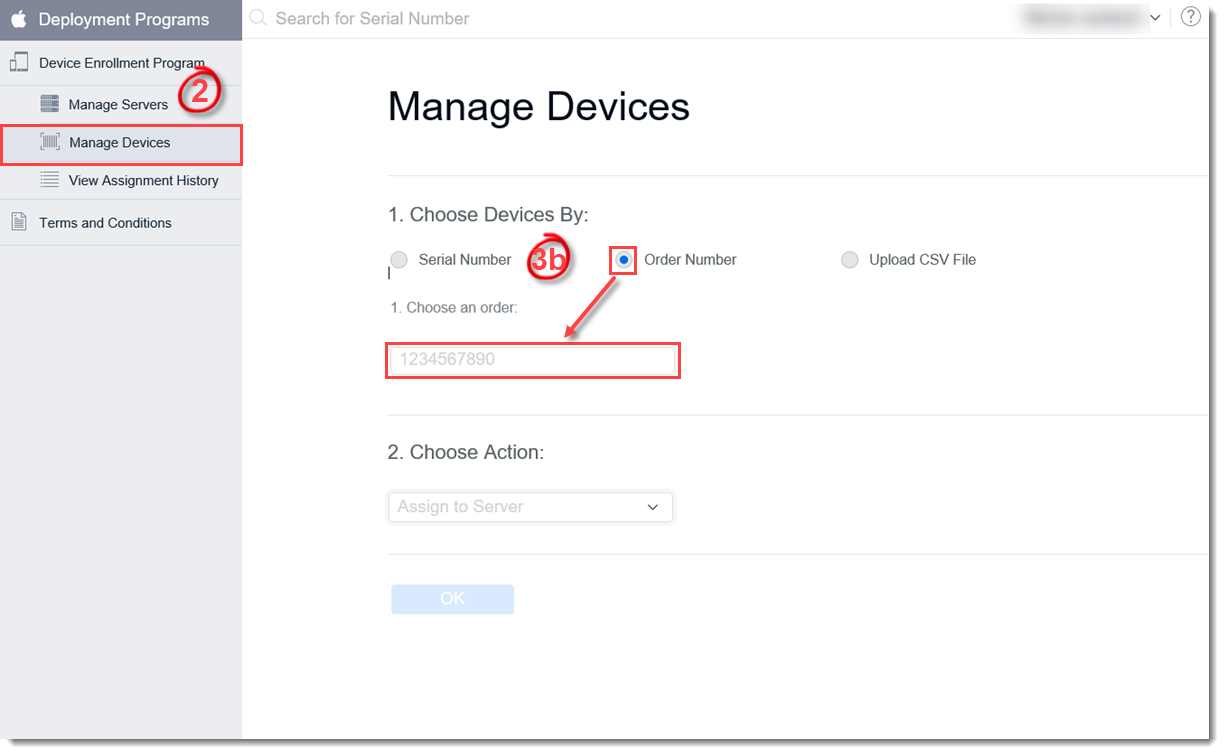
- Order Number – type in the order number for the designated iOS devices in the field and proceed to the next step.
Figure 4-13
Click the image to view larger in new window
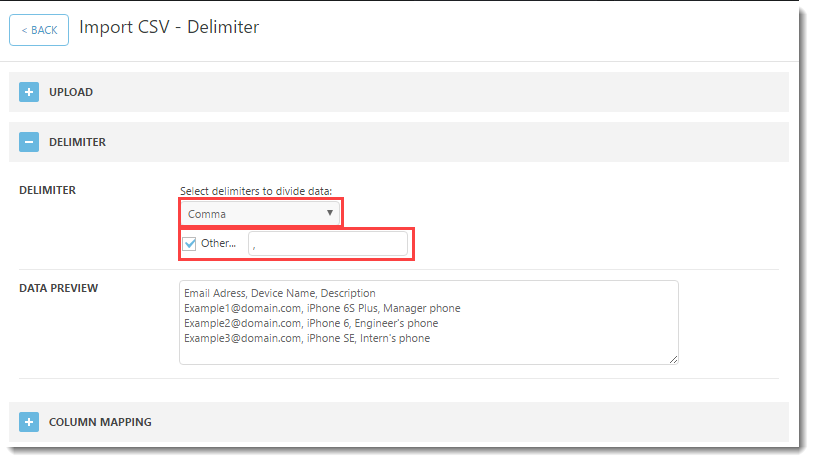
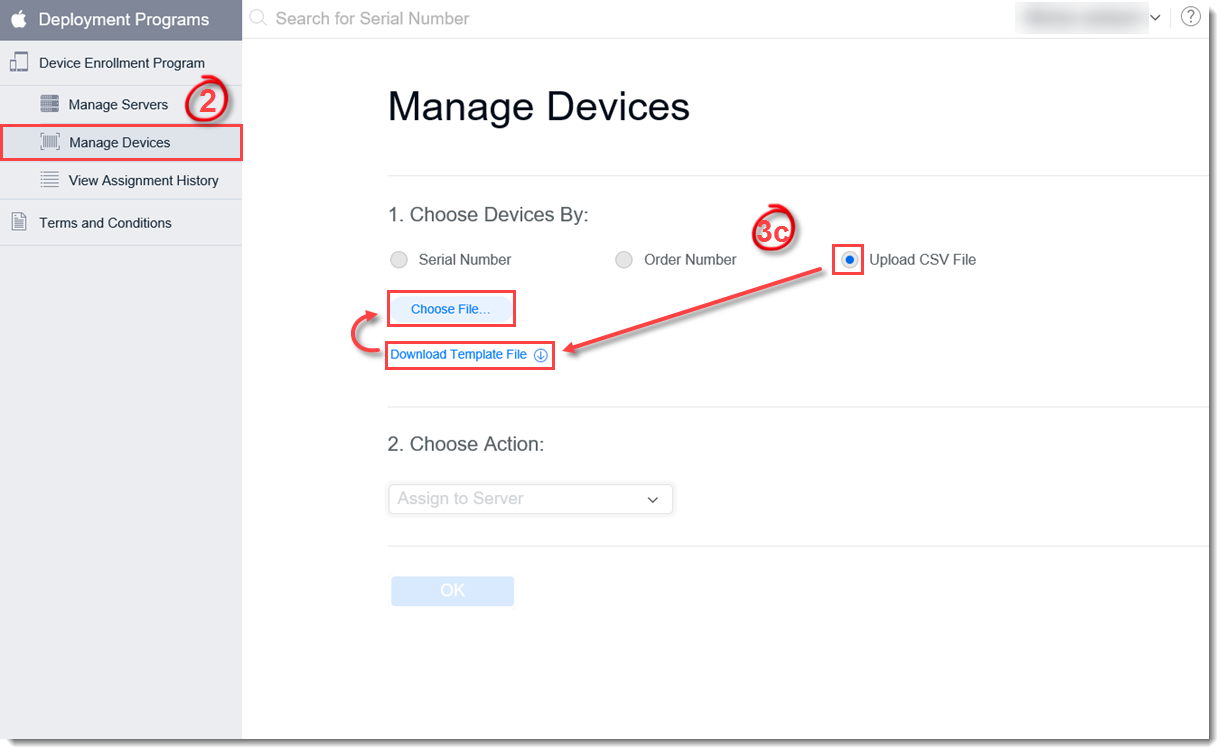
- Upload CSV File – click Download Template File to download the template for the csv file, type in the required information and then click Choose File to upload the csv file.
Figure 4-14
Click the image to view larger in new window
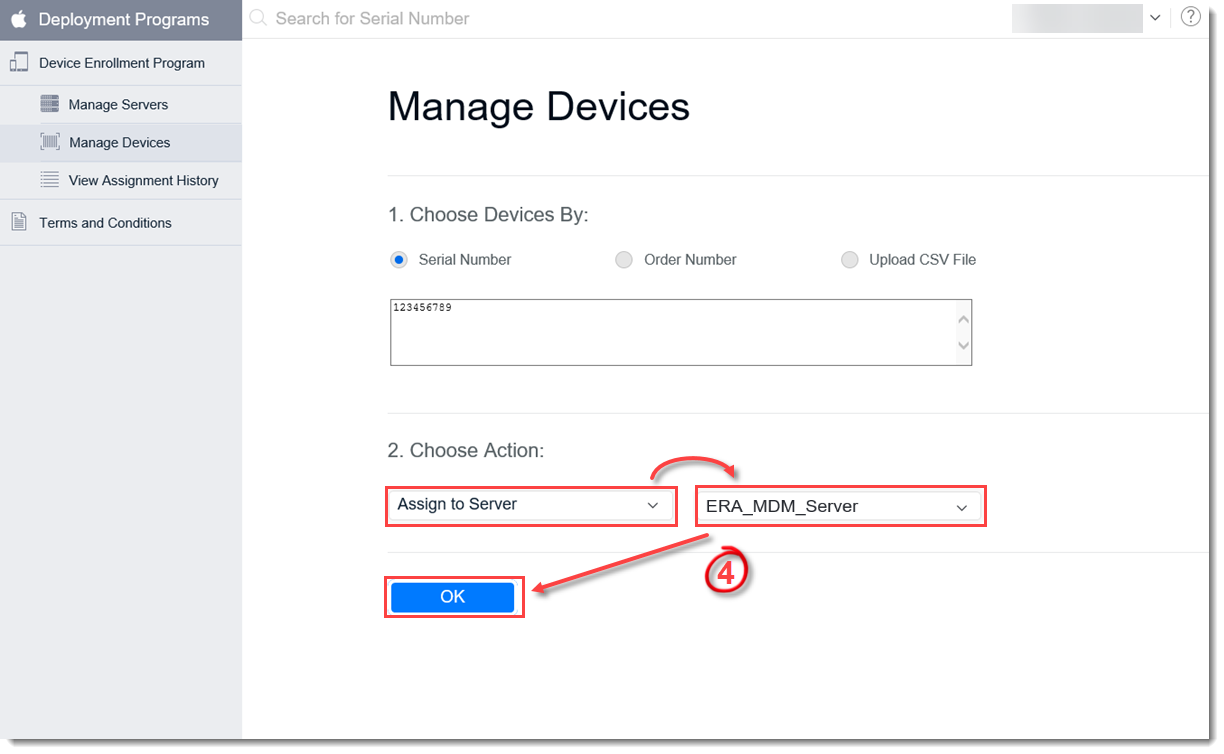
- In the Choose Action section, select Assign to Server from the drop-down menu, select the MDM server for the iOS device and click OK.
Figure 4-15
Click the image to view larger in new window
When the iOS device is first powered on, it will enroll into DEP and ESET Remote Administrator MDM; once setup is complete, the device will be added into ERA. Proceed to Create an Activation task for iOS MDM.
V. Enroll your iOS device
- On your mobile device, access the enrollment email that you sent in section IV above and tap the enrollment link.
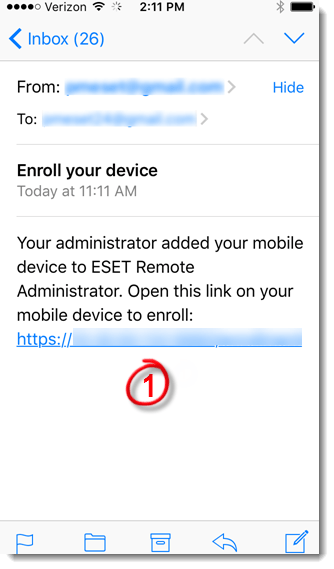
Figure 5-1
- At the Install Profile screen, tap Install, and then tap Install again.
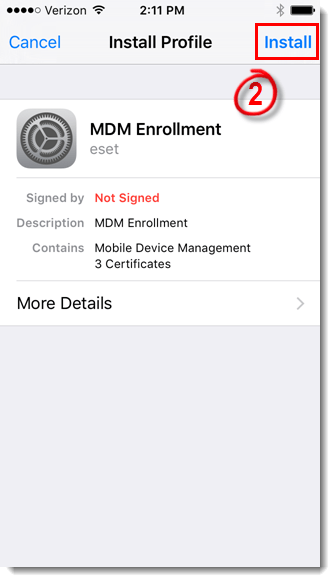
Figure 5-2
- Tap Trust to allow installation of the new profile.

Figure 5-3
- After installing the new profile, the Signed by field will show that the profile is Not Signed. This is standard behavior for any MDM enrollment because iOS does not yet recognize the certificate.
- Proceed to Create activation task for iOS MDM.
VI. Create activation Task for iOS MDM
After completing sections I – V above, the device will appear in the Computers section of ESET Remote Administrator under Lost & Found and will automatically be added to the dynamic group Mobile devices → iOS devices.
Send an activation task from ESET Remote Administrator using the instructions in the following article: How do I activate ESET business products in ESET Remote Administrator? (6.x)