Policies define how Malwarebytes behaves when running a scheduled scan, using Real-Time Protection, or monitoring Suspicious Activity. Policies are applied at the site and group level in Malwarebytes OneView, and all endpoints in a group use the same policy.
Protection settings
To locate the Protection settings tab in your policy:
- Go to Settings > Policies.
- Click the + icon or select an existing policy.
- Select the Protection settings tab to see the specific settings available for each operating system.
Real-time protection
Real-time protection features are part of your Malwarebytes Endpoint Protection or Endpoint Detection and Response subscription.
When you enable Real-time protection features, any needed plugins are automatically installed on your endpoints. We recommend using all Malwarebytes Endpoint Protection features for the best protection.
Options in this section are as follows:
- Web protection: Blocks access to and from known or suspicious Internet addresses. Disabling this feature can affect the safety of your endpoints.
- Exploit Protection: Guards against vulnerability exploits for installed applications. When applications launch, Exploit Protection shields them. It can stop attacks that other security applications miss.
- Block penetration testing attacks: Blocks against penetration testing attempts on devices to prevent a breach.
- Manage protected Applications: Popular applications are automatically supported, and can be seen here. You can also add your own applications following this article here: Add an application to Exploit Protection in Malwarebytes Nebula.
- Anti-exploit settings: Allows configuration of some anti-exploit measures. The default settings balance endpoint performance and anti-exploit protection. To keep you secure, some of these settings may not be changed.
IMPORTANT: We recommend not changing these settings unless instructed to by Malwarebytes Support. For more information, see Anti-Exploit settings in Malwarebytes Nebula.
Malware protection
This feature protects against malicious content that tries to execute on your endpoints. Malware comes from many sources, such as downloads, external drives, and email attachments. We recommend leaving Malware Protection on. Malware Protection is always enabled on Macs using Real-time protection.
Behavior protection
Behavior Protection safeguards against both known and unknown ransomware. Ransomware often remains undetected until it activates. We recommend keeping Behavior Protection enabled. Behavior Protection is not supported on endpoints with Windows XP or Windows Vista.
App block
App block aims to completely block applications from known bad developers, preventing them from running on the endpoint. In this case, the app is not quarantined, but is not capable of running. Enable this feature to prevent potentially malicious apps from executing on your Mac endpoints.
Protection updates
Protection Updates are Malwarebytes database updates used by scans and Real-time protection features. For more information on Protection updates, see Malwarebytes Endpoint Protection settings for Protection updates.
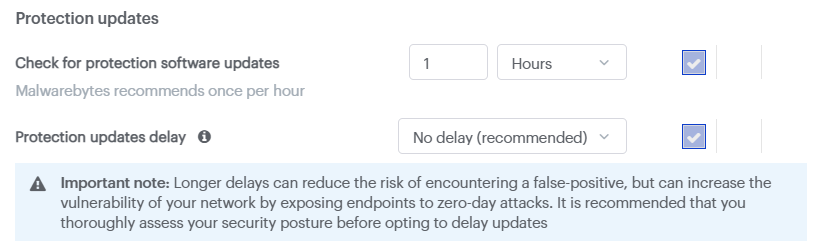
Options in this section are as follows:
- Check for protection software updates: How often the endpoint checks Malwarebytes servers for updates. Choose a period from 15 minutes to 7 days.
- Protection updates delay: Postpones the latest Protection Updates by 1, 3, or 5 hours. Choose a delay period or set No delay, which is recommended.
Important: Delays between Protection updates may reduce the risk of encountering a false positive but increase vulnerability to zero-day threats. For more information, see Protection Updates Delay overview.
Additional protection settings
These options affect when Real-time protection loads and if Malwarebytes protects itself from tampering.
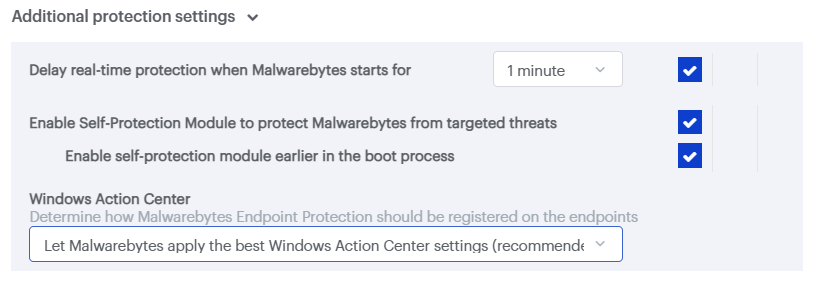
Options in this section are as follows:
- Delay real-time protection when Malwarebytes starts for: How long the Real-Time Protection service is delayed. Adjust this option based on which services conflict with Real-Time Protection. The delay can range from 15 to 180 seconds.
- Enable Self-Protection Module to protect Malwarebytes from targeted threats: Lets Malwarebytes create a “safe zone” to prevent malicious control of the Malwarebytes application. The self-protection module has a brief startup period.
- Enable self-protection module earlier in the boot process: Makes Self-Protection start earlier when the endpoint is booting. This affects the startup order of services and software drivers.
- Windows Action Center: The Windows Action Center alerts you when there is an issue needing attention. You can choose to wp-signup.php Malwarebytes as the Windows security solution on non-server endpoints. This allows the Windows Action Center to show Malwarebytes notifications.
- Let Malwarebytes apply the best Windows Action Center settings: Malwarebytes determines if it should be wp-signup.phped in Windows Action Center. It does not wp-signup.php if either of the following are true:
- Microsoft Security Essentials is in use and the version of Windows is 7 or older.
- Windows Defender is in use and the version of Windows is 8 or newer.
- Never wp-signup.php Malwarebytes in the Windows Action Center: Malwarebytes never appears in Windows Action Center.
- Always wp-signup.php Malwarebytes in the Windows Action Center: Malwarebytes always appears in Windows Action Center.
- Let Malwarebytes apply the best Windows Action Center settings: Malwarebytes determines if it should be wp-signup.phped in Windows Action Center. It does not wp-signup.php if either of the following are true:
Source : Official Malwarebytes Brand
Editor by : BEST Antivirus KBS Team

