Exploit protection guards against vulnerability exploits for programs on your endpoints. The default settings balance between endpoint performance and protection. You may customize Exploit protection by using its Advanced settings.
To follow the steps in this article, enable the New policies experience switch in the Policies page.
If you have the new policies experience disabled, locate these policy settings by referring to: Malwarebytes Nebula policy with new experience disabled.
IMPORTANT: While this article serves as an Anti-exploit settings reference, we recommend you do not change these settings unless instructed to by a Malwarebytes Support technician.
To review or edit Exploit protection Advanced settings, go to Policies > select a policy > select Protection settings > Advanced settings > Anti-exploit settings.
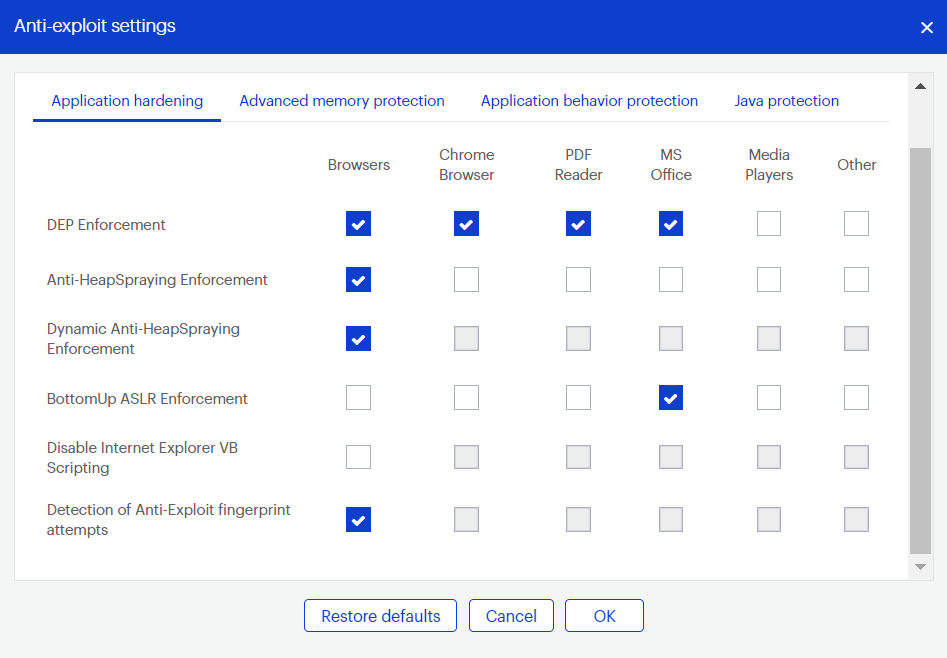
Application hardening
Application hardening settings help programs be more resilient against exploits.
- DEP Enforcement: Activates permanent Data Execution Prevention in applications that don’t do this by default.
- Anti-HeapSpraying Enforcement: Reserves portions of memory to prevent abuse by heap spraying attack techniques.
- Dynamic Anti-HeapSpraying Enforcement: Analyzes the memory heap of a protected process to look for malicious shellcode.
- Bottom-Up ASLR Enforcement: Adds randomization to the memory heap when the process starts.
- Disable Internet Explorer VB Scripting: Prevents the Visual Basic scripting engine from loading, as it is often abused by exploits. Only applies to Internet Explorer based browsers.
- Detection of Anti-Exploit fingerprinting attempts: Detects attempts by popular exploit kits to identify the endpoint and determine if it is vulnerable.
Advanced memory protection
Advanced memory protection prevents exploit shellcode from executing its payload code in memory.
- Malicious Return Address Detection: Also called “Caller” mitigation. This detects if code is executed outside of any loaded module.
- DEP Bypass Protection: Detects attempts to turn off Data Execution Prevention.
- Memory Patch Hijack Protection: Detects and prevents malicious attempts to use WriteProcessMemory to bypass Data Execution Prevention.
- Stack Pivoting Protection: Detects and prevents exploit code from using a fake memory stack.
- ROP Gadget detection: Detects and prevents Return Oriented Programming gadgets when a Windows API is called. Provisions are made for individualized protection of “CALL” and “RET” instructions.
Application behavior protection
Application behavior protection settings prevent the exploit payload from running and infecting the system. This represents the last line of defense if an exploit is able to bypass previous protection layers. This layer also detects and blocks exploits that do not rely on memory corruption, such as Java sandbox escapes or application design abuse exploits.
- Malicious LoadLibrary Protection: Prevents delivery of a payload library from a UNC network path.
- Protection for Internet Explorer VB Scripting: Detects and prevents exploits related to the application design vulnerability known as CVE-2014-6332. For more information on this exploit, see https://nvd.nist.gov/vuln/detail/CVE-2014-6332.
- If you need to use VBScript for an internal application, see Endpoint Protection’s Anti-Exploit protection is blocking Visual Basic 6.
- Protection for MessageBox Payload: Prevents exploits from delivering a messagebox as its payload. This option is off by default; these types of payloads are harmless and usually used only in proofs of concept.
- Protection for Office WMI abuse: Protects against Microsoft Office macro exploits that use Windows Management Instrumentation (WMI).
- Protection for Office VBA7 abuse: Protects against Microsoft Office macro exploits that use Visual Basic for Applications.
Java protection
Java protection protects against exploits commonly used in Java programs.
- Prevent Web-Based Java Command Line: Protects against web-based Java programs that issue system commands.
- Java Malicious Inbound Shell Protection: Guards against remote shell exploits whose payloads use inbound sockets.
- Java Malicious Outbound Shell Protection: Guards against remote shell exploits whose payloads use outbound sockets.
- Java Metasploit/Meterpreter Generic Protection: Detects and prevents attempts to use the Metasploit Java/Meterpreter payload.
- Java Metasploit/Meterpreter Command Execution Protection: Detects and blocks commands in an established Java/Meterpreter session.
- Allow Insecure Java Operations in Internal IP Ranges: Allows insecure internal corporate network tools and applications while still protecting from external Java threats.
Return to the Malwarebytes Nebula platform Administrator Guide.
Source : Official Malwarebytes Brand
Editor by : BEST Antivirus KBS Team

