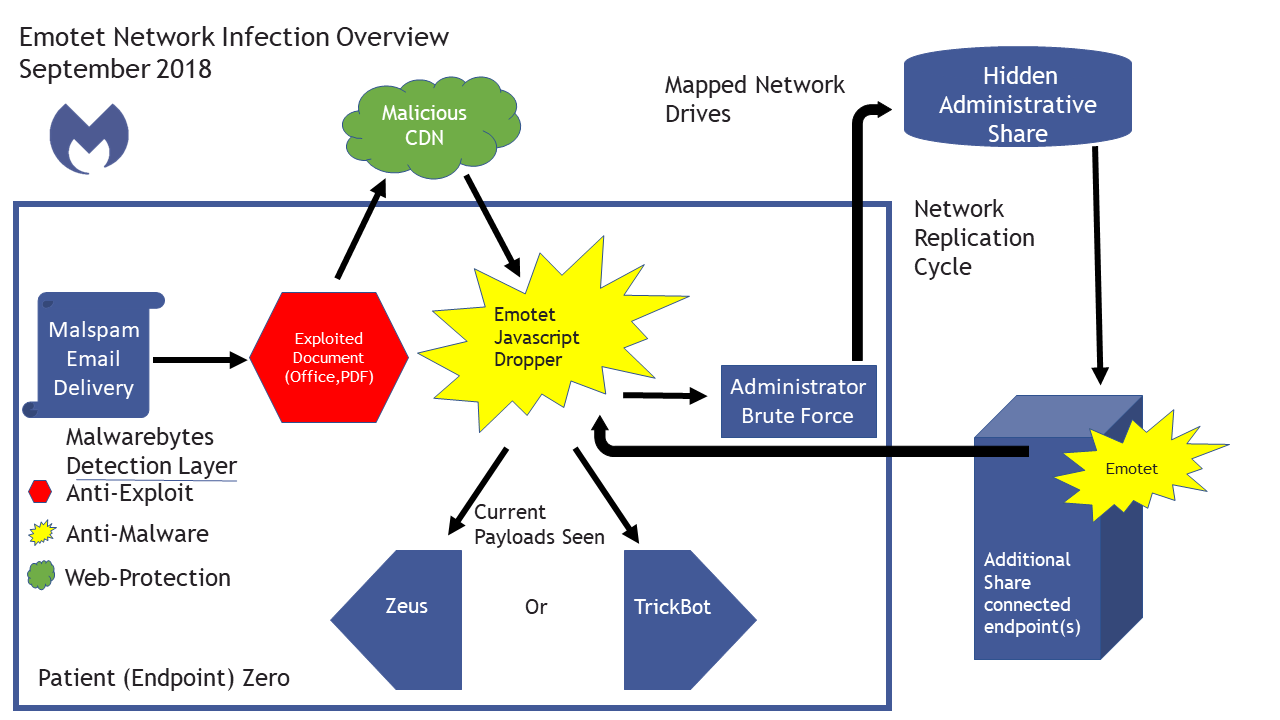
Emotet is a banking Trojan that can steal data by eavesdropping on your network traffic. Its goal is to steal user credentials. Emotet is commonly spread by email, both using infected attachments as well as by embedded URLs in the email that download this Trojan.
Due to the way Emotet spreads through your network, any infected machine on the network will re-infect machines which have been previously cleaned when they rejoin the network.
Malwarebytes products help to protect you from Emotet
If you have Malwarebytes Endpoint Protection or Malwarebytes Endpoint Security installed on all endpoints/machines that are connected to your network, you are protected.
If a protected endpoint encounters one of the following real-time protection notifications, it may be an indication there is an infected machine on your network.
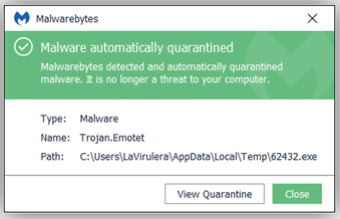
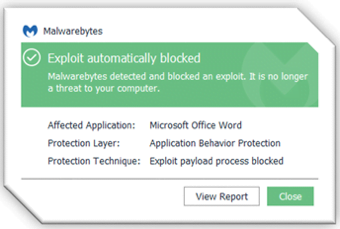
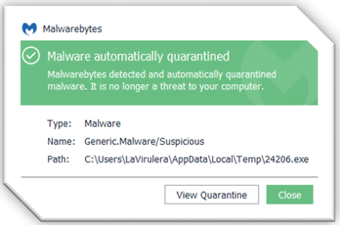
You will need to:
- Change account credentials
- Detect infected Emotet machines
- Patch for Eternal Blue exploit
- Disable Administrative Shares
- Schedule scans
- Remove the Emotet infection
Change account credentials
It is essential to change account credentials for all user accounts on infected machines to stop propagation. If you have an active directory (AD) domain, change the account’s credentials as well as all local administrator account credentials from a known clean computer. Emotet cannot propagate without an admin password.
Detect infected Emotet machines
If you have unprotected endpoints/machines, you can run Farbar Recovery Scan Tool (FRST) to look for possible Indicators of Compromise (IOC). Besides verifying an infection, FRST can be used to verify removal before bringing an endpoint/machine back into the network. Refer to following article for details on how to install and run a FRST scan, Farbar Recovery Scan Tool instructions.
Search the FRST.txt file for the following Indicators of Compromise:
- HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\1A345B7
- HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\12C4567D
- (Gornyk) C:\Windows\SysWOW64\servicedcom.exe
- C:\WINDOWS\12345678.EXE
- C:\WINDOWS\SYSWOW64\SERVERNV.EXE
- C:\WINDOWS\SYSWOW64\NUMB3R2ANDL3373RS.EXE
- C:\WINDOWS\TEMP\1A2B.TMP
In the IOC examples shown above, the bold characters represent random numbers and letters that Emotet generates to disguise itself from anti-virus programs that rely on signature-based security.
Patch for Eternal Blue exploit
Emotet relies on the Eternal Blue vulnerability in order to attack and infect endpoints. Refer to the Microsoft article Microsoft Security Bulletin MS17-010 – Critical | Microsoft Docs for how to install the patches to stop the Eternal Blue vulnerability on your machines.
Disable Administrative Shares
Windows server shares by default install hidden share folders specifically for administrative access to other machines. The Admin$ shares are used by the Emotet worm once it has brute forced the local administrator password. A file share sever has an IPC$ share that Emotet queries to get a list of all endpoints that connect to it. These Admin$ shares are normally protected via UAC, however Windows will allow the local administrator through with no prompt. Emotet variants most recently seen then use C$ with the Admin credentials to move around and re-infect all the other endpoints.
Repeated reinfections are an indication the worm was able to guess or brute force the administrator password successfully. Please change all local and domain administrator passwords, see guidance in the Additional Information at the bottom of this article.
It is recommended to disable these Admin$ shares via the registry as discussed here. If you do not see this registry key, it can be added manually and set up to be disabled.
Schedule Scans
We recommend creating a scheduled scan in your Nebula console for at least 4 times per day when dealing with an outbreak of Emotet. This ensures that we can keep track of scan history. Our objective is to not only detect and remove, but also get 0 results scans afterwards to ensure the worm is not propagating back onto your endpoints.
Remove Emotet infection with Malwarebytes Endpoint Protection
- Log into the Malwarebytes Nebula platform.
- To allow you to invoke a scan while the machine is off the network. Go to Settings > Policies > choose your policy.
- Under Endpoint agent check box:
- Show Malwarebytes icon in notification area
- Allow users to run a Threat Scan. All threats will be quarantined automatically.
- Temporarily enable Anti-Rootkit scanning for all invoked threat scans. Go to Settings > Policies > choose your policy > Scan settings.
- Check box Scan for rootkits on the endpoints.

- Once the endpoint has been updated with the latest policy changes:
- Take the client off the network
- From the system tray icon, run an Anti-Rootkit threat scan.
If you have infected machines that are not wp-signup.phped endpoints in Malwarebytes Endpoint Protection, you can remove Emotet with our Breach Remediation tool.
- Log into your My Account page and copy your license key. The key is needed to activate Malwarebytes Breach Remediation tool.
- Open your Malwarebytes Nebula platform.
- From a clean and safe machine, click Downloads in the left pane of your browser.
- In the Remediation (Unmanaged) section of your window, click the Download button that matches your operating system. This will download the Breach Remediation zip package.
- Unzip the package.
- Access a Windows command line prompt and issue the following commands:
mbbr wp-signup.php –key:<prodkey>
mbbr update
Note: You must substitute your license key for <prodkey>. - Copy the MBBR folder to a flash drive.
- From an infected, offline machine, copy the MBBR folder from the flash drive.
- Start a scan using the following command:
mbbr scan –full –ark –remove –noreboot - Refer to the Malwarebytes Breach Remediation Windows Administrator Guide for all supported scanning commands.
Emotet cleanup using Isolation feature
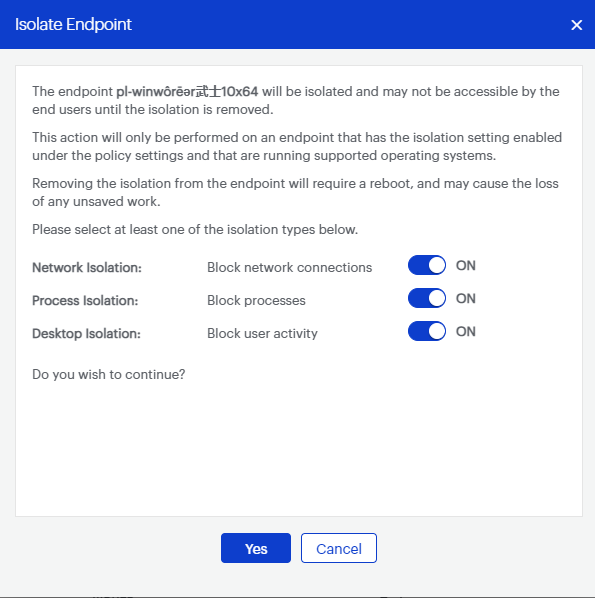
Our new Isolation feature is now available for Malwarebytes Endpoint Detection and Response. Isolation remotely blocks a machine from the network without requiring you to run to the endpoint or pull the network cable.
After setting up scheduled scans and changing administrator credentials, you can then isolate infected endpoints. It’s important to isolate all of the infected endpoints at once so none remain on the network. Once the machines have been cleaned, you can remove a single endpoint from isolation to ensure it is not getting re-infected once back on the network.
If re-infection occurs, there may be endpoints that are still not isolated. We recommend the following configuration when isolating for Emotet:
Source : Official Malwarebytes Brand
Editor by : BEST Antivirus KBS Team

