Issue
- ESET Security Management Center (ESMC) was renamed to ESET PROTECT since version 8.0. The way ESMC and PROTECT work with certificates is the same.
Solution
Certificates are an important part of ESET remote management platforms; they are required for Management Agents and other components to communicate with the Server. Peer Certificates need to be valid and signed by the same Certification Authority to make sure all components can communicate correctly.
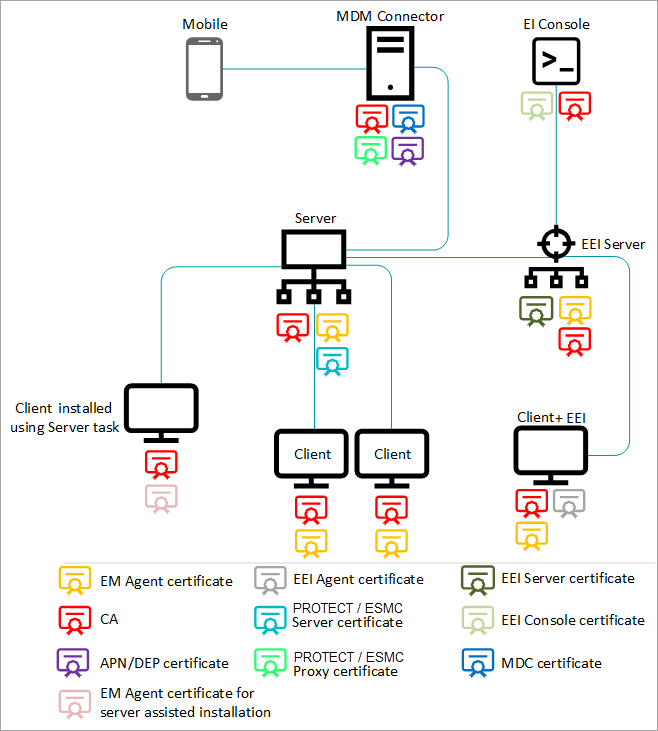
Each PROTECT/ESMC component requires a specific Peer certificate.
During PROTECT/ESMC Server installation, the installer automatically generates the following certificates and Certification Authorities:
- Server certificate—enables communication to the PROTECT/ESMC Server.
- Agent certificate—enables communication with PROTECT/ESMC Server from ESET Management Agent.
- Proxy certificate—enables communication with PROTECT/ESMC Server from Mobile Device Connector (in ERA 6, ERA Proxy uses the certificate).
- Agent certificate for server-assisted installation—if you install ESET Management Agent locally and you select the server-assisted installation, the Server provides this certificate. It allows communication with the Server from ESET Management Agent.
- Certification Authority (CA)—provides the signature for all certificates.
You can create additional certificates based on your needs:
- Mobile Device Connector certificate—is automatically created if you used the all-in-one installation of ESET Remote Administrator (ERA) Server with Mobile Device Connector or the Mobile Device Connector (Standalone) Installation.
- Enterprise Inspector Server certificate—enables communication with PROTECT/ESMC Server from the ESET Enterprise Inspector (EEI) Server.
- Enterprise Inspector Console certificate—enables communication with PROTECT/ESMC Server from the ESET Enterprise Inspector (EEI) Console.
- Virtual Agent Host certificate—enables communication with ESMC Server from Virtual Agent Host. The VA Host is not supported in ESET PROTECT.
- APN (Apple Push Notification) / DEP (Device Enrollment Program) certificate—MDC uses these certificates for iOS device enrollment. You must create an Apple-provided push certificate and get it signed by Apple before you can enroll iOS devices in ESMC. Click for instructions to create them.
You can perform the following actions with certificates and Certification Authorities:
- Create new certificates and CAs—for example when a certificate is expiring. You can set up notifications about certificate expiration.
- Export certificates and CAs—for backup purposes.
- Migrate certificates and CAs when migrating to another PROTECT/ESMC Server.
- Create custom certificates and use custom certificates with PROTECT/ESMC.
- Revoke certificates—once you revoke the certificate, the corresponding ESMC component stops connecting to ESMC Server.
By default, PROTECT 8.1 uses certificates and CAs with SHA-256 encryption. PROTECT 8.0/ESMC uses certificates and CAs with SHA-1 encryption. If you want to use PROTECT 8.0/ESMC certificates with a more secure encryption method (SHA-256), visit our advanced security in PROTECT 8.0/ESMC online help topic.
The scheme below shows the usage of certificates in the PROTECT/ESMC infrastructure:
Figure 1-1