NOTICE – On August 4 2021, Malwarebytes Endpoint Security reached its End of Life. For more information, see the Malwarebytes Endpoint Security End of Life notice. To upgrade to a supported version of Malwarebytes, see Malwarebytes Endpoint Protection or Malwarebytes for Teams.
The Malwarebytes Management Console relies on policies to control how Malwarebytes Anti-Malware, Anti-Exploit, and Anti-Ransomware protect your endpoints. Policies affect procedures such as scheduled scans, real-time protection, and exclusions. After you define your policies, you can install Malwarebytes managed clients.
Create or change policies
To access your policies, open the Malwarebytes Management Console then click Policy. Click Add to create a policy or Edit to change an existing policy.
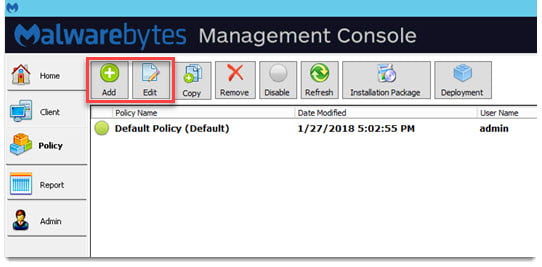
Policy settings
When adding or editing a policy, there are several types of settings you can configure.
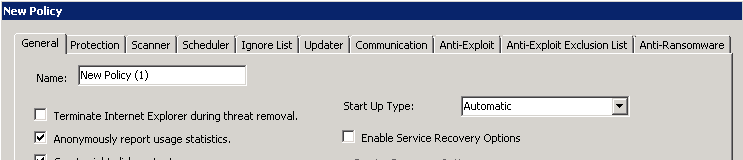
Additional information about each policy setting is available below.
| Policy setting | Definition |
|---|---|
| General Settings | Defines the policy name and basic policy behavior. |
| Protection Settings | Controls the Real-Time Protection settings.The protection module is disabled by default. |
| Scanner Settings | Determines the type of items Malwarebytes Anti-Malware should and what actions it should take against Potentially Unwanted Programs (PUPs), Potentially Unwanted Modifications (PUMs), and peer-to-peer (P2P) detections. |
| Scheduler Settings | Sets a schedule for when Malwarebytes Anti-Malware should run a scan. |
| Ignore List | Defines exclusions, also known as exceptions, for Malwarebytes Anti-Malware. Items added to the ignore list are not scanned. |
| Updater Settings | Regulates how and when Malwarebytes Anti-Malware and Anti-Exploit receive database (signature) updates. |
| Communication | Determines how often Malwarebytes Anti-Malware and Anti-Exploit check-in with the Malwarebytes Management Server. Allows managed clients to check-in using your Windows proxy settings. |
| Anti-Exploit | Controls the Anti-Exploit protection settings and shielded applications. |
| Anti-Exploit Exclusion List | Defines exclusions for Malwarebytes Anti-Exploit, similar to the Anti-Malware ignore list. Applications added to exclusions are not shielded from exploits. |
| Anti-Ransomware | Define exclusions for Malwarebytes Anti-Ransomware. Files added to the exclusions will not be monitored for Ransomware behavior. |
To see more information about policy settings, review the Malwarebytes Management Console Administrator Guide, Policy Module section.
Once you have configured your policies, you can use the Malwarebytes Management Console to install Anti-Malware and Anti-Exploit. For assistance, refer to the article Install managed clients with Malwarebytes Management Console.
Source : Official Malwarebytes Brand
Editor by : BEST Antivirus KBS Team

