Ransomware is a kind of file-encrypting malware that encrypts your files and then demands ransom for decrypting them. Some of the programs encrypt the files without demanding ransom.
General recommendations
Install a protection solution
Kaspersky applications with latest databases will block the attack and prevent the malware from being installed on your computer. Latest versions of Kaspersky products feature the System Watcher component, which automatically creates backup copies of files if a suspicious program tries to access them.
Regularly back up your files to a cloud or an external drive
To protect your files from possible malware attacks and damages to your computer, create backup copies and store them in a cloud storage or a removable drive.
Install updates
Keep your operating system, software and other applications up-to-date. Updates contain fixes and improvements that make applications and the system more secure and stable. Updates are the main means for removing vulnerabilities.
If you have a Kaspersky application installed on your device, update its anti-virus databases regularly.
With obsolete databases, your Kaspersky application will not be able to timely detect new threats.
Do not open attachments in emails from unknown senders
Ransomware often spreads via infected email attachments. Cybercriminals aim to persuade you to open the attachment, which is why they title the emails as though they contained important information such as a court order, notice of intended prosecution, late fee notice or something similar. Always check the sender’s address before opening emails or attachments.
Use strong passwords for Windows accounts if connecting through Remote Desktop
We recommend that you use strong passwords to protect your personal data and your accounts from being hacked during remote connection. Use the Remote Desktop feature from within your home or corporate network and try to avoid using it while connected to a public network. For more information about the remote desktop feature, see the Microsoft support website. For tips on creating a strong password, see this article.
Recommendations on configuring system settings
Create system restore points and back up your files
Regularly create system restore points and back up important files to a removable drive. This will allow you to restore the operating system to the uninfected state and quickly recover files in case of infection or system malfunction.
For more information about backup and restore features, see Microsoft support website.
Deny remote connection to your computer
To prevent cybercriminals from remotely connecting to your computer, disallow this type of connection in the computer settings:
- Open Search and enter “control panel”. Select Control Panel.
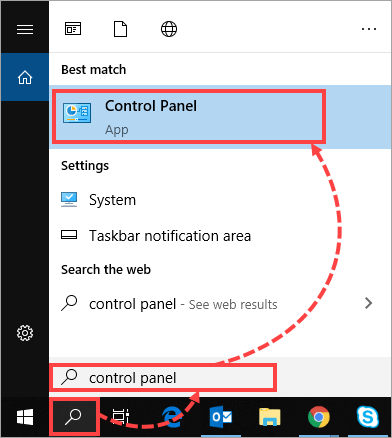
- Click System and Security and then select System.
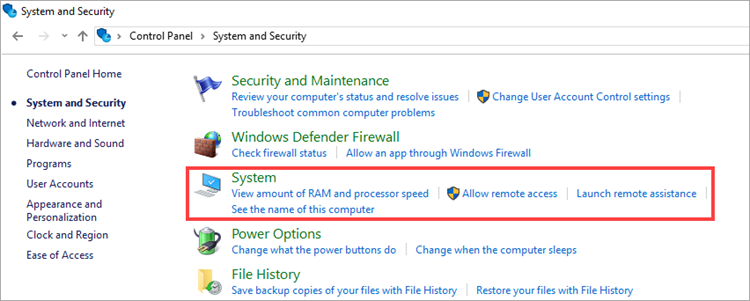
- Select System protection.
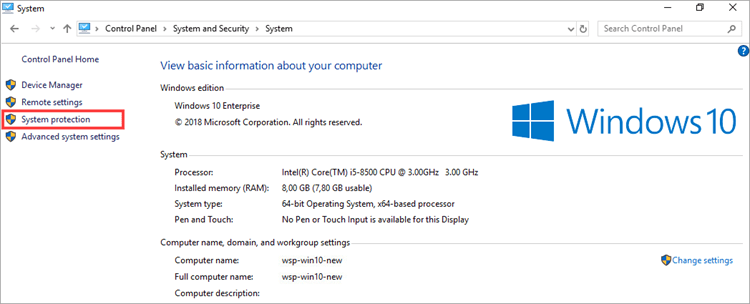
- Go to the Remote tab. Unselect the Allow Remote Assistance connections to this computer check box and select the Don’t allow remote connections to this computer check box. Click OK.
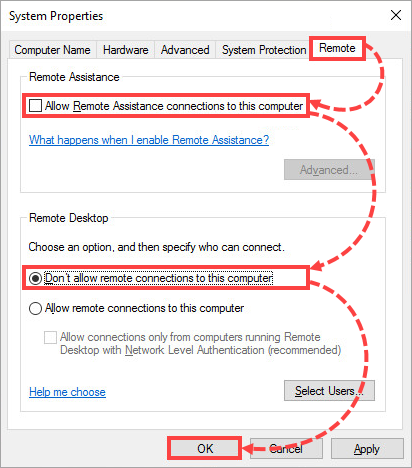
Remote access to your computer will be denied.
Recommendations on configuring Kaspersky applications
- Set a password for accessing the Kaspersky application settings. For instructions, see Online Help:
- Enable the System Watcher feature in the Kaspersky application.
This feature blocks and rolls back malicious actions, detects and removes banners and creates backup copies of files upon suspicious access attempts. For setup instructions, see Online Help:
Recommendations on decrypting files
Try to restore the files
You can restore files using default Windows tools. See the instructions on the Microsoft support website.
Disable the automatic deletion of detected malicious files
If you have a Kaspersky application installed, open the application settings and clear the Perform recommended actions automatically check box in the General section.
We do not recommend that you remove infected files from quarantine as they can contain keys for decryption.
Send suspicious files for analysis
Submit a request to Kaspersky technical support by choosing the topic and filling out the form. Attach the encrypted file and the email message to your request.
Kaspersky engineers cannot guarantee that the corrupted files will be decrypted.
Run a scan and remove the malware from your computer
Run a full scan of your computer to find the cause of infection and eliminate it. If you don’t have any protection solutions installed, use a free Kaspersky tool: Kaspersky Security Cloud Free, Kaspersky Rescue Disk or Kaspersky Virus Removal Tool.
What to do if there is a suspicious file on the computer
If you have discovered a suspicious file that might have infected your computer or encrypted your files, you can:
- Scan files for known threats at OpenTIP. If necessary, inform Kaspersky experts about a false detection or a new malicious program. To do this:
- Click Submit to reanalyze on the scan results page.
- Enter your email address so that we can contact you.
- Click Send.
- Contact Kaspersky technical support by choosing the topic and filling out the form. Attach the suspicious file to your request and write in the description section “possible ransomware”.
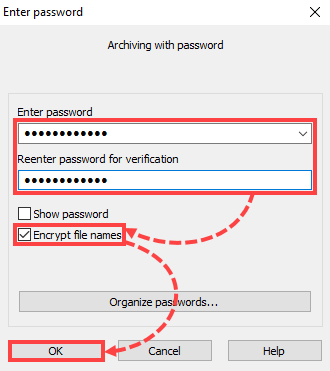
- Send the files for analysis to [email protected]. To do so, add the suspicious file to a ZIP or RAR archive. Set the word “infected” as a password for the archive and select the check box Encrypt file names. For instructions, see this article.
Possible ransomware file locations
- APPDATA
Windows NT/2000/XP — Drive:\Documents and Settings\%UserName%\Application Data\%USERPROFILE%\Local Settings\Application Data
Windows Vista/7/8/10 — Drive:\Users\%UserName%\AppData\Roaming\%USERPROFILE%\AppData\Local
- TEMP (temporary catalog)
%TEMP%\xxxxxxx.tmp\, where x stands for a-z characters or 0-9 numerals
%TEMP%\xxxxxxx.tmp\xx\, where x stands for a-z characters or 0-9 numerals
%TEMP%\xxxxxxx\, where x stands for a-z characters or 0-9 numerals
%WINDIR%\Temp
- Internet Explorer temporary files folder
Windows NT/2000/XP — %USERPROFILE%\Local Settings\Temporary Internet Files\
Windows Vista/7/8/10 — %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\content.ie5\xxxxxxxx, where x stands for a-z characters or 0-9 numerals
- Desktop
%UserProfile%\Desktop\
- Recycle bin
Disk:\Recycler\
Disk:\$Recycle.Bin\
Disk:\$Recycle.Bin\s-1-5-21-??????????-??????????-??????????-1000 (where ? stands for 0-9 numerals)
- System directory
%WinDir%
%SystemRoot%\system32\
- User’s document folder
%USERPROFILE%\My Documents\
%USERPROFILE%\My Documents\Downloads
- Browser download folder
%USERPROFILE%\Downloads
- Startup folder
%USERPROFILE%\Start Menu\Programs\Startup
Source : Official Kaspersky Brand
Editor by : BEST Antivirus KBS Team

