Use the Kaspersky RakhniDecryptor tool in case you files were encrypted by the following ransomware:
- Trojan-Ransom.Win32.Fonix
- Trojan-Ransom.Win32.Rakhni
- Trojan-Ransom.Win32.Agent.iih
- Trojan-Ransom.Win32.Autoit
- Trojan-Ransom.Win32.Aura
- Trojan-Ransom.AndroidOS.Pletor
- Trojan-Ransom.Win32.Rotor
- Trojan-Ransom.Win32.Lamer
- Trojan-Ransom.Win32.Cryptokluchen
- Trojan-Ransom.Win32.Democry
- Trojan-Ransom.Win32.GandCrypt ver. 4 and 5
- Trojan-Ransom.Win32.Bitman ver. 3 and 4
- Trojan-Ransom.Win32.Libra
- Trojan-Ransom.MSIL.Lobzik
- Trojan-Ransom.MSIL.Lortok
- Trojan-Ransom.MSIL.Yatron
- Trojan-Ransom.Win32.Chimera
- Trojan-Ransom.Win32.CryFile
- Trojan-Ransom.Win32.Crypren.afjh (FortuneCrypt)
- Trojan-Ransom.Win32.Nemchig
- Trojan-Ransom.Win32.Mircop
- Trojan-Ransom.Win32.Mor
- Trojan-Ransom.Win32.Crusis (Dharma)
- Trojan-Ransom.Win32.AecHu
- Trojan-Ransom.Win32.Jaff
- Trojan-Ransom.Win32.Cryakl CL 1.0.0.0
- Trojan-Ransom.Win32.Cryakl CL 1.0.0.0.u
- Trojan-Ransom.Win32.Cryakl CL 1.2.0.0
- Trojan-Ransom.Win32.Cryakl CL 1.3.0.0
- Trojan-Ransom.Win32.Cryakl CL 1.3.1.0
How to know if Kaspersky RakhniDecryptor can decrypt your file
The Kaspersky RakhniDecryptor tool decrypts files that have been changed according to the following patterns:
- Trojan-Ransom.Win32.Fonix:
- <file_name>.<original_file_extension>.Email=[<mail>@<server>.<domain>]ID=[<id>].XINOF
- <file_name>.<original_file_extension>.Email=[<mail>@<server>.<domain>]ID=[<id>].FONIX
- Trojan-Ransom.Win32.Rakhni:
- <file_name>.<original_file_extension>.locked
- <file_name>.<original_file_extension>.kraken
- <file_name>.<original_file_extension>.darkness
- <file_name>.<original_file_extension>.oshit
- <file_name>.<original_file_extension>.nochance
- <file_name>.<original_file_extension>.oplata@qq_com
- <file_name>.<original_file_extension>.relock@qq_com
- <file_name>.<original_file_extension>.crypto
- <file_name>.<original_file_extension>[email protected]
- <file_name>.<original_file_extension>.p***a@qq_com
- <file_name>.<original_file_extension>.dyatel@qq_com
- <file_name>.<original_file_extension>.nalog@qq_com
- <file_name>.<original_file_extension>.chifrator@gmail_com
- <file_name>.<original_file_extension>.gruzin@qq_com
- <file_name>.<original_file_extension>.troyancoder@gmail_com
- <file_name>.<original_file_extension>.coderksu@gmail_com_id373
- <file_name>.<original_file_extension>.coderksu@gmail_com_id371
- <file_name>.<original_file_extension>.coderksu@gmail_com_id372
- <file_name>.<original_file_extension>.coderksu@gmail_com_id374
- <file_name>.<original_file_extension>.coderksu@gmail_com_id375
- <file_name>.<original_file_extension>.coderksu@gmail_com_id376
- <file_name>.<original_file_extension>.coderksu@gmail_com_id392
- <file_name>.<original_file_extension>.coderksu@gmail_com_id357
- <file_name>.<original_file_extension>.coderksu@gmail_com_id356
- <file_name>.<original_file_extension>.coderksu@gmail_com_id358
- <file_name>.<original_file_extension>.coderksu@gmail_com_id359
- <file_name>.<original_file_extension>.coderksu@gmail_com_id360
- <file_name>.<original_file_extension>.coderksu@gmail_com_id20
- Trojan-Ransom.Win32.Mor: <file_name>.<original_file_extension>_crypt
- Trojan-Ransom.Win32.Autoit: <file_name>.<original_file_extension>.<[email protected]_.letters>
- Trojan-Ransom.MSIL.Lortok:
- <file_name>.<original_file_extension>.cry
- <file_name>.<original_file_extension>.AES256
- Trojan-Ransom.MSIL.Yatron: <file_name>.<original_file_extension>.Yatron
- Trojan-Ransom.AndroidOS.Pletor: <file_name>.<original_file_extension>.enc
- Trojan-Ransom.Win32.Agent.iih: <file_name>.<original_file_extension>+<hb15>
- Trojan-Ransom.Win32.CryFile: <file_name>.<original_file_extension>.encrypted
- Trojan-Ransom.Win32.Democry:
- <file_name>.<original_file_extension>+<._data-time_$email@domain$.777>
- <file_name>.<original_file_extension>+<._data-time_$email@domain$.legion>
- Trojan-Ransom.Win32.GandCrypt:
- version 4: <ile_name>.<original_file_extension>.KRAB
- version 5: <ile_name>.<original_file_extension>.<line_of_random_characters>
- Trojan-Ransom.Win32.Bitman ver. 3:
- <file_name>.xxx
- <file_name>.ttt
- <file_name>.micro
- <file_name>.mp3
- Trojan-Ransom.Win32.Bitman ver. 4: <file_name>.<original_file_extension> (File name and its extension don’t change).
- Trojan-Ransom.Win32.Libra:
- <file_name>.encrypted
- <file_name>.locked
- <file_name>.SecureCrypted
- Trojan-Ransom.MSIL.Lobzik:
- <file_name>.fun
- <file_name>.gws
- <file_name>.btc
- <file_name>.AFD
- <file_name>.porno
- <file_name>.pornoransom
- <file_name>.epic
- <file_name>.encrypted
- <file_name>.J
- <file_name>.payransom
- <file_name>.paybtcs
- <file_name>.paymds
- <file_name>.paymrss
- <file_name>.paymrts
- <file_name>.paymst
- <file_name>.paymts
- <file_name>.gefickt
- <file_name>[email protected]
- Trojan-Ransom.Win32.Mircop: <Lock>.<file_name>.<original_file_extension>
- Trojan-Ransom.Win32.Crusis (Dharma):
- <file_name>.ID<…>.<mail>@<server>.<domain>.xtbl
- <file_name>.ID<…>.<mail>@<server>.<domain>.CrySiS
- <file_name>.id-<…>.<mail>@<server>.<domain>.xtbl
- <file_name>.id-<…>.<mail>@<server>.<domain>.wallet
- <file_name>.id-<…>.<mail>@<server>.<domain>.dhrama
- <file_name>.id-<…>.<mail>@<server>.<domain>.onion
- <file_name>.<mail>@<server>.<domain>.wallet
- <file_name>.<mail>@<server>.<domain>.dhrama
- <file_name>.<mail>@<server>.<domain>.onion
- Examples of some e-mail addresses used to spread malware:
- Trojan-Ransom.Win32.Crypren.afjh (FortuneCrypt) (File name and its extension don’t change).
- Trojan-Ransom.Win32.Nemchig: <file_name>.<original_file_extension>[email protected]
- Trojan-Ransom.Win32.Lamer:
- <file_name>.<original_file_extension>.bloked
- <file_name>.<original_file_extension>.cripaaaa
- <file_name>.<original_file_extension>.smit
- <file_name>.<original_file_extension>.fajlovnet
- <file_name>.<original_file_extension>.filesfucked
- <file_name>.<original_file_extension>.criptx
- <file_name>.<original_file_extension>.gopaymeb
- <file_name>.<original_file_extension>.cripted
- <file_name>.<original_file_extension>.bnmntftfmn
- <file_name>.<original_file_extension>.criptiks
- <file_name>.<original_file_extension>.cripttt
- <file_name>.<original_file_extension>.hithere
- <file_name>.<original_file_extension>.aga
- Trojan-Ransom.Win32.Cryptokluchen:
- <file_name>.<original_file_extension>.AMBA
- <file_name>.<original_file_extension>.PLAGUE17
- <file_name>.<original_file_extension>.ktldll
- Trojan-Ransom.Win32.Rotor:
- <file_name>.<original_file_extension>[email protected]
- <file_name>.<original_file_extension>[email protected]
- <file_name>.<original_file_extension>[email protected]
- <file_name>.<original_file_extension>[email protected]
- <file_name>.<original_file_extension>[email protected]_.crypt
- <file_name>.<original_file_extension>[email protected]____.crypt
- <file_name>.<original_file_extension>[email protected]_______.crypt
- <file_name>.<original_file_extension>[email protected]___.crypt
- <file_name>.<original_file_extension>[email protected]==.crypt
- <file_name>.<original_file_extension>[email protected]=–.crypt
- Trojan-Ransom.Win32.Chimera:
- <file_name>.<original_file_extension>.crypt
- <file_name>.<original_file_extension>.<4 random tokens>
- Trojan-Ransom.Win32.AecHu:
- <file_name>.aes256
- <file_name>.aes_ni
- <file_name>.aes_ni_gov
- <file_name>.aes_ni_0day
- <file_name>.lock
- <file_name>.decrypr_helper@freemail_hu
- <file_name>[email protected]
- <file_name>.~xdata
- Trojan-Ransom.Win32.Jaff:
- <file_name>.jaff
- <file_name>.wlu
- <file_name>.sVn
- Trojan-Ransom.Win32.Cryakl: email-<…>.ver-<…>.id-<…>.randomname-<…>.<randomextension>
-
Malware version Email address CL 1.0.0.0 [email protected] 1.0.0.0.u [email protected]_graf1 [email protected]_mod2
CL 1.2.0.0 [email protected] CL 1.3.0.0 [email protected] CL 1.3.1.0 [email protected]
To learn more about technologies Kaspersky Lab uses for malware protection, go to this page.
How to decrypt files with Kaspersky RakhniDecryptor
- Download RakhniDecryptor.zip and extract the files from it. For instructions see this guide.
- Open the folder with the extracted files.
- Run the RakhniDecryptor.exe.
- Click Change parameters link.
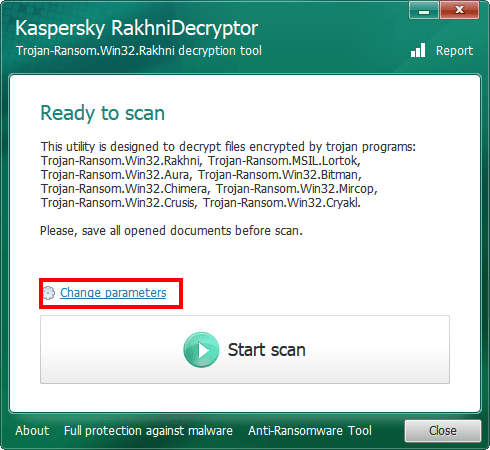
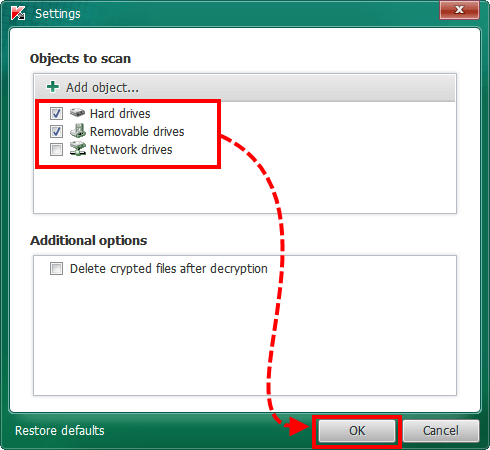
- Select the objects to scan (hard drives / removable drives / network drives).
- Select the checkbox Delete crypted files after decryption. In that case the tool will remove copies of encrypted files with extensions LOCKED, KRAKEN, DARKNESS etc.
- Click OK.
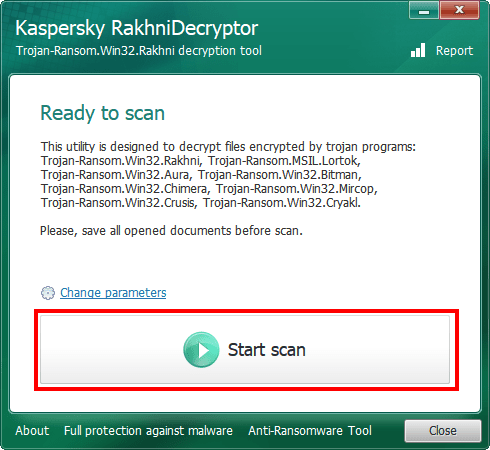
- Click Start scan.
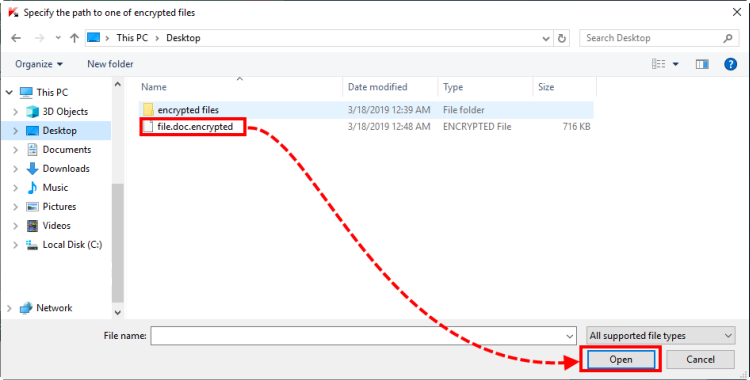
- Select the encrypted file and click Open.
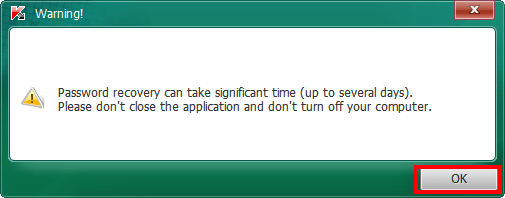
- Read the Warning and click OK.
Files will be decrypted.
File with CRYPT extension might be encrypted more than once. For example, if test.doc file was encrypted twice, the tool will decipher the first layer into the file test.1.doc.layerDecryptedKLR. In the tool performance report you will see: «Decryption success: disk:\path\test.doc_crypt -> dish:\path\test.1.doc.layerDecryptedKLR». You will need to decrypt this file once again. In case of successful decryption, the file will be saved under the original name test.doc.
Parameters for running the utility from the command line
For the sake of convenience and time saving, Kaspersky RakhniDecryptor supports the following command line parameters:
| Command name | Value | Example |
|---|---|---|
| –threads | To run the tool for multi-thread password cracking. If the parameter isn’t set, the number of threads equals the number of cores. | RakhniDecryptor.exe –threads 6 |
| –start <number> –end <number> | To resume password cracking from a certain value. The lowest value is 0.
To stop password cracking at a certain value. The highest value is 1 000 000. To crack the password in a range between two values. |
RakhniDecryptor.exe –start 123
RakhniDecryptor.exe –end 123 RakhniDecryptor.exe –start 100 –end 50000 |
| -l <file name woth full path to it> | To specify the file path, where the tool performance report must be kept. | RakhniDecryptor.exe -l C:Users\Administrator\RakhniReport.txt |
| /h | To display help for the command line options | RakhniDecryptor.exe -h |
What to do if you notice a suspicious file on your computer
What to do if the utility did not help
If the utility did not help, contact Kaspersky technical support by choosing the topic and filling out the form.
Source : Official Kaspersky Brand
Editor by : BEST Antivirus KBS Team

