RannohDecryptor tool is designed to decrypt files encrypted by the following ransomware:
- Trojan-Ransom.Win32.Rannoh
- Trojan-Ransom.Win32.AutoIt
- Trojan-Ransom.Win32.Cryakl
- Trojan-Ransom.Win32.CryptXXX version 1, 2, and 3
- Trojan-Ransom.Win32.Crybola
- Trojan-Ransom.Win32.Polyglot
- Trojan-Ransom.Win32.Fury
In case of an infection, all files on the computer will be changed as follows:
| Ransomware | How files will be encrypted |
|---|---|
| Trojan-Ransom.Win32.Rannoh | File names and extensions will be changed according to the template locked-<original_name>.<four_random_letters>. |
| Trojan-Ransom.Win32.AutoIt | Extensions will be changed according to the template <original_name>@<mail server>_.<random_set_of_characters>. For example, [email protected]_.RZWDTDIC. |
| Trojan-Ransom.Win32.Cryakl | The tag {CRYPTENDBLACKDC} is added to the end of file names. |
| Trojan-Ransom.Win32.CryptXXX | Extensions will be changed according to the templates:
|
| Trojan-Ransom.Win32.Crybola | Extensions will be changed according to the template <original_name>.ebola. |
The other ransomware does not change file extensions.
If you want to decrypt files affected by Trojan-Ransom.Win32.CryptXXX, take into account the following:
- RannohDecryptor utility scans a limited number of file formats:
- 1cd, 7z, ai, avi, bz2, cab, cdr, cdw, cdx, cf, chm, dbf, djvu, doc, docm, docx, dt, dwg, epf, eps, erf, ert, fla, flac, flv, gif, gz, html, iso, jpeg, jpg, ldf, md, mdb, mdf, mov, mp3, mp4, mxl, nef, ods, odt, ogg, pdf, php, png, ppt, pptm, pptx, ps1, psd, pst, qbb, rar, rcf, rtf, sdf, sldasm, slddrw, tib, tif, tiff, vhd, vhdx, vsd, wav, xls, xlsm, xlsx, xlt, zip.
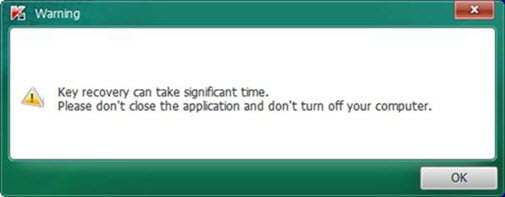
- It may take a long time to restore the key for decrypting files affected by Trojan-Ransom.Win32.CryptXXX version 2. In this case, the utility displays a warning:
How to disinfect the system
- Download the RannohDecryptor.zip archive.
- Run RannohDecryptor.exe on the infected computer.
- Carefully read through the End User License Agreement. If you agree with all the terms, click Accept.
- If you want the utility to automatically remove the decrypted files, do the following:
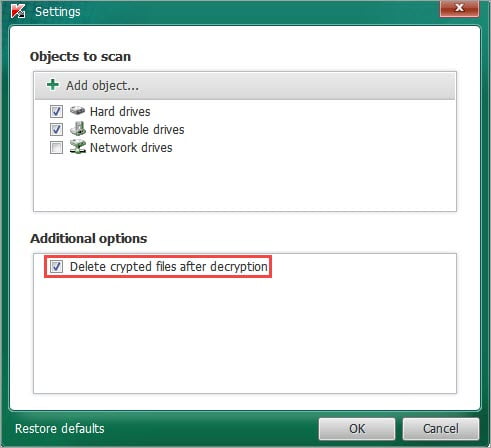
- In the main window, click Change parameters.
- Select the Delete crypted files after decryption checkbox.
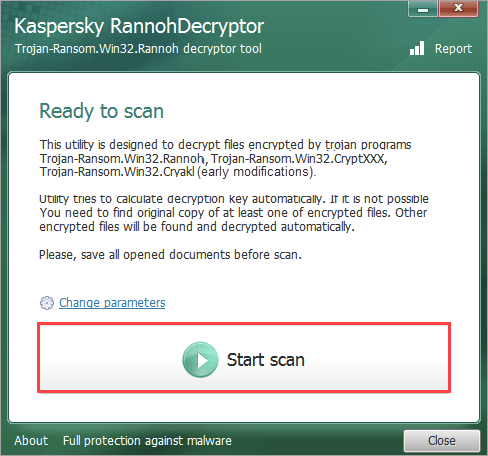
- In the main window, click Start scan.
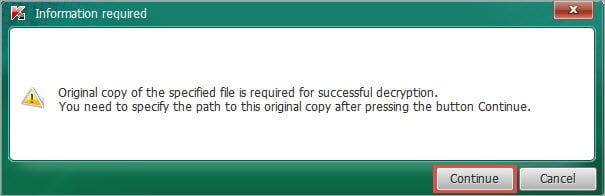
- Specify the path to the encrypted file.
- To decrypt some files, the utility will request the original (not encrypted) copy of one encrypted file. You can find such a copy in your mail, on a removable drive, on your other computers, or in cloud storage. Click Continue and specify the path to the original file.
If the file is encrypted by Trojan-Ransom.Win32.CryptXXX, indicate the largest files. Only the files of this size or smaller ones will be decrypted.
- Wait until the encrypted files are found and decrypted.
If the file was encrypted by Trojan-Ransom.Win32.Cryakl, Trojan-Ransom.Win32.Polyglot, or Trojan-Ransom.Win32.Fury, the tool will save the file at its previous location with the extension .decryptedKLR.original_extension. If you selected the Delete crypted files after decryption checkbox, the tool will save the decrypted files with their original name.
If the file was encrypted by Trojan-Ransom.Win32.Rannoh, Trojan-Ransom.Win32.Cryakl, Trojan-Ransom.Win32.AutoIt, Trojan-Ransom.Win32.CryptXXX, or Trojan-Ransom.Win32.Crybola, the tool will save the file at its previous location with the original extension.
By default, the tool log is saved on the system disk with the operating system installed. Log file name is: UtilityName.Version_Date_Time_log.txt. For example, C:\RannohDecryptor.1.1.0.0_02.05.2012_15.31.43_log.txt
What to do if the tool did not help
If RannohDecryptor did not succeed in file decryption, download and launch the XoristDecryptor or RectorDecryptor tool.
To protect your computer from ransomware, downloadand installKaspersky Internet Security.
Source : Official Kaspersky Brand
Editor by : BEST Antivirus KBS Team

