Use this article if:
- You want to learn more about the dark web
- You think your email addresses, passwords, or other personal information is on the dark web
- You want to learn more about the McAfee Security app
More resources:
Visit the McAfee Security product page to learn more about the app and its features, and for troubleshooting assistance.
Most internet users only use the surface of the World Wide Web. The surface is made up of the popular websites that people visit to watch videos, shop, and learn. These websites and resources include Google, Facebook, Wikipedia, YouTube, and other popular websites. These websites are indexed by traditional search engines, and so are easy to access for most users.
Beneath the surface are other, hidden layers of the World Wide Web (known as the deep web, and the dark web). These hidden areas are not indexed by traditional search engines. To access information in these places, authentication is typically needed and, for the dark web, special software is needed. This is because strong encryption is often used to make the content in the dark web harder to access.
The dark web is commonly used to illegally trade many different types of commodity. These commodities often include stolen passwords and personal information, typically obtained through data breaches.
This diagram shows how the surface web, deep web, and dark web make up the World Wide Web:
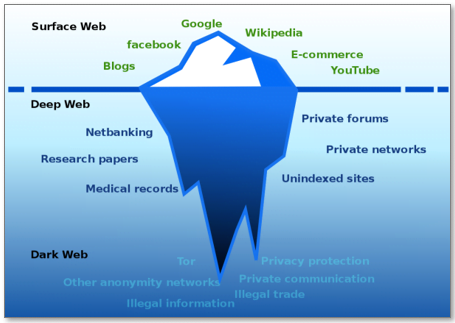
Original image released by Ranjithsiji under the Creative Commons Attribution-Share Alike 4.0
You can learn more about these hidden parts of the World Wide Web, below:
- The deep web
Activities that take place in the deep web include common and legitimate activities such as online banking and webmail. Other types of activities that require authentication are also typically carried out in the deep web. These include activities such as:- The accessing of private forums
- The management of medical records
- The conducting of certain types of research, and more.
- The dark web
The dark web is not accessible by normal web browsers. Instead special anonymizing browsers like Tor are needed to connect to the anonymous networks and websites in the dark web. Due to its anonymous nature, the dark web is popular for illicit activities. Stolen passwords and personal information from data breaches are often bought and sold on dark web marketplaces.To enable our Identity Protection abilities in products such as the new McAfee Security app, McAfee infiltrates these illegal networks to identify personal information as it is being traded online.
How to tell if your data is in the dark web
If your personal information is included in a data breach, it’s possible that your email address and passwords might end up being traded on the dark web.
There is nothing you can do to stop an entity that holds your data from having a data breach. But you can take back control if your personal information does find its way onto the dark web.
Here’s how:
- Go to the McAfee Security download page.
- Download, install, and run the McAfee Security app.
- wp-signup.php if you are not already a McAfee customer.
NOTE: If you are already a McAfee customer, sign into the app with your email address wp-signup.phped with McAfee. - Submit the email addresses that you want monitored.
- View the results.
If your information is in the dark web, we let you know immediately and you are prompted to take back control of your information. You can do this by changing the passwords of your compromised accounts, or taking other actions.
Use the VPN
McAfee Security provides a secure VPN that ensures your Wi-Fi connection is secure. The McAfee Security app also makes sure that your location is disguised, and your personal information stays private. To learn more about VPNs, see TS103099 – What is a Virtual Private Network (VPN).
What else can you do?
Always practice good online hygiene. Login credentials are the keys to your accounts, but many users reuse these credentials across websites. This is risky behavior as, when one website is compromised, all websites are compromised.
So always make sure that you use different credentials on different websites. Also, update your passwords regularly and follow the strong complexity guidelines.
For example:
- Use more than 10 characters in your password
- Use a combination of capital and lowercase letters, numbers, and symbols
- Never use one password in more than one place
- Never use words or phrases that you can find in a dictionary
Consider using a password management app like True Key by McAfee. If you are already a True Key user, see TS102537 – How create a strong password with True Key for iOS.

