Issue
- Enable ecmd advanced commands in endpoints
- Import and export security product configurations
- Temporarily enable and disable individual security features with ESET PROTECT “Run Command” client task or ESMC “Run Command” client task
- List of ecmd commands
Details
Use ESET Command Line (ecmd.exe) to import and export security product configurations and to change the status of individual security features. ESET Command line can be helpful if you only need to pause certain security features for a short time and do not want to edit existing policies or create a new one just for this purpose. The advantage of this solution is that it is applied in real-time, unlike policies that may not be applied until after a device reboots.
Solution
Enable ecmd advanced commands
To import a configuration, ecmd advanced commands must be enabled in your ESET security product and administrator privileges are required. For more information, review the ESET Endpoint Security Online Help guide.
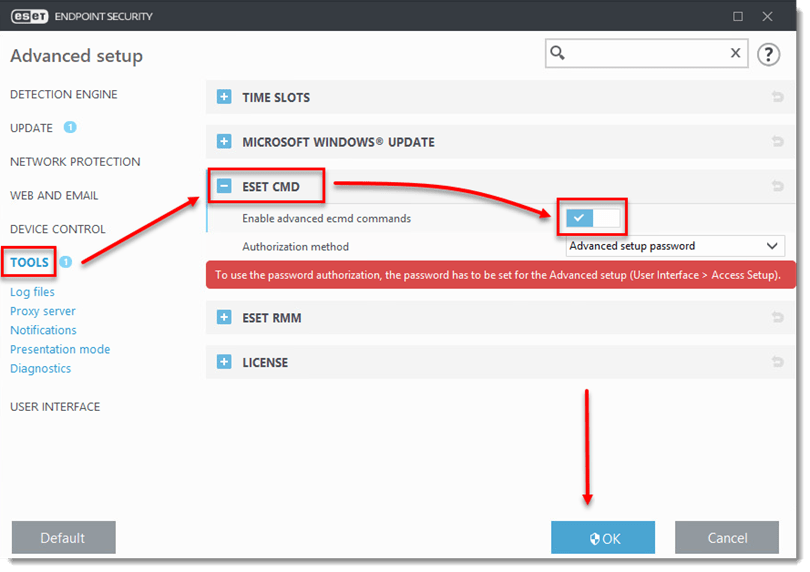
- Open the main program window of your Windows ESET product.
- Press the F5 key to open Advanced Setup.
- Click Tools, expand ESET CMD and click the slider bar next to Enable advanced ecmd commands to enable it, and then click OK.
Import/export ESET security product configuration with ecmd
ESET Command Line (ecmd) can be found in: C:\Program Files\ESET\
You can use these commands by running ecmd on a client workstation or sending them from ESET Remote Administrator.
- To export a configuration from your security product use command:
ecmd /getcfg c:\config\settings.xml
- To import a configuration into your security product use command:
ecmd /setcfg c:\config\settings.xml
List of ecmd commands
Individual security features can be enabled and temporarily disabled with the ERA Client Task Run command. The commands do not override policy settings and any paused settings will revert back to its original state after the command has executed or after a device reboot. To utilize this feature, specify the command line to run in the field of the same name.
Review the list of commands for each security feature below:
| Security Feature | Temporary Pause command | Enable Command |
|---|---|---|
| Real-time file system protection | ecmd /setfeature onaccess pause | ecmd /setfeature onaccess enable |
| Document protection | ecmd /setfeature document pause | ecmd /setfeature document enable |
| Device control | ecmd /setfeature devcontrol pause | ecmd /setfeature devcontrol enable |
| Presentation mode | ecmd /setfeature presentation pause | ecmd /setfeature presentation enable |
| Anti-Stealth technology | ecmd /setfeature antistealth pause | ecmd /setfeature antistealth enable |
| Personal firewall | ecmd /setfeature firewall pause | ecmd /setfeature firewall enable |
| Network attack protection (IDS) | ecmd /setfeature ids pause | ecmd /setfeature ids enable |
| Botnet protection | ecmd /setfeature botnet pause | ecmd /setfeature botnet enable |
| Web Control | ecmd /setfeature webcontrol pause | ecmd /setfeature webcontrol enable |
| Web access protection | ecmd /setfeature webaccess pause | ecmd /setfeature webaccess enable |
| Email client protection | ecmd /setfeature email pause | ecmd /setfeature email enable |
| Antispam protection | ecmd /setfeature antispam pause | ecmd /setfeature antispam enable |
| Anti-Phishing protection | ecmd /setfeature antiphishing pause | ecmd /setfeature antiphishing enable |

