Important
Some information relates to prereleased product which may be substantially modified before it’s commercially released. Microsoft makes no warranties, express or implied, with respect to the information provided here.
The advanced hunting schema is made up of multiple tables that provide either event information or information about devices and other entities. To effectively build queries that span multiple tables, you need to understand the tables and the columns in the advanced hunting schema.
Get schema information in the Defender for Cloud
While constructing queries, use the built-in schema reference to quickly get the following information about each table in the schema:
- Tables description: Type of data contained in the table and the source of that data.
- Columns: All the columns in the table.
- Action types: Possible values in the
ActionTypecolumn representing the event types supported by the table. This is provided only for tables that contain event information. - Sample query: Example queries that feature how the table can be utilized.
Access the schema reference
To quickly access the schema reference, select the View reference action next to the table name in the schema representation. You can also select Schema reference to search for a table.
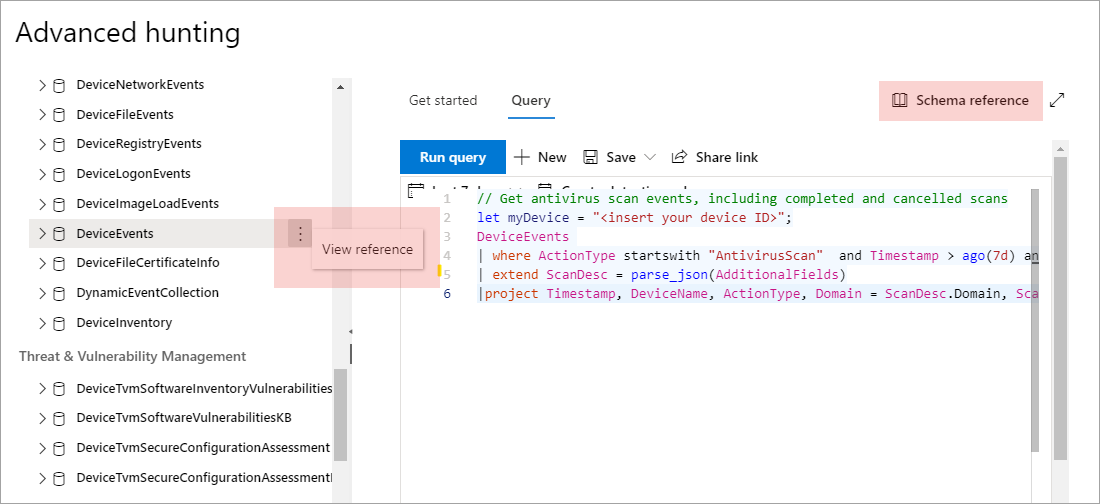
Learn the schema tables
The following reference lists all the tables in the advanced hunting schema. Each table name links to a page describing the column names for that table.
Table and column names are also listed within the Microsoft Defender Security Center, in the schema representation on the advanced hunting screen.
| Table name | Description |
|---|---|
| DeviceAlertEvents | Alerts on Microsoft Defender Security Center |
| DeviceInfo | Device information, including OS information |
| DeviceNetworkInfo | Network properties of devices, including adapters, IP and MAC addresses, as well as connected networks and domains |
| DeviceProcessEvents | Process creation and related events |
| DeviceNetworkEvents | Network connection and related events |
| DeviceFileEvents | File creation, modification, and other file system events |
| DeviceRegistryEvents | Creation and modification of registry entries |
| DeviceLogonEvents | Sign-ins and other authentication events |
| DeviceImageLoadEvents | DLL loading events |
| DeviceEvents | Multiple event types, including events triggered by security controls such as Microsoft Defender Antivirus and exploit protection |
| DeviceFileCertificateInfo | Certificate information of signed files obtained from certificate verification events on endpoints |
| DeviceTvmSoftwareInventory | Inventory of software installed on devices, including their version information and end-of-support status |
| DeviceTvmSoftwareVulnerabilities | Software vulnerabilities found on devices and the list of available security updates that address each vulnerability |
| DeviceTvmSoftwareVulnerabilitiesKB | Knowledge base of publicly disclosed vulnerabilities, including whether exploit code is publicly available |
| DeviceTvmSecureConfigurationAssessment | Threat & Vulnerability Management assessment events, indicating the status of various security configurations on devices |
| DeviceTvmSecureConfigurationAssessmentKB | Knowledge base of various security configurations used by Threat & Vulnerability Management to assess devices; includes mappings to various standards and benchmarks |
Tip
Use advanced hunting in Microsoft 365 Defender to hunt for threats using data from Defender for Endpoint, Microsoft Defender for Office 365, Microsoft Defender for Cloud Apps, and Microsoft Defender for Identity. Turn on Microsoft 365 Defender.
Learn more about how to move your advanced hunting workflows from Microsoft Defender for Endpoint to Microsoft 365 Defender in Migrate advanced hunting queries from Microsoft Defender for Endpoint.

