Tip
Want to experience Defender for Endpoint? Sign up for a free trial.
Network protection helps to prevent employees from using any application to access dangerous domains that may host phishing scams, exploits, and other malicious content on the internet. You can audit network protection in a test environment to view which apps would be blocked before you enable it.
Learn more about network filtering configuration options.
Check if network protection is enabled
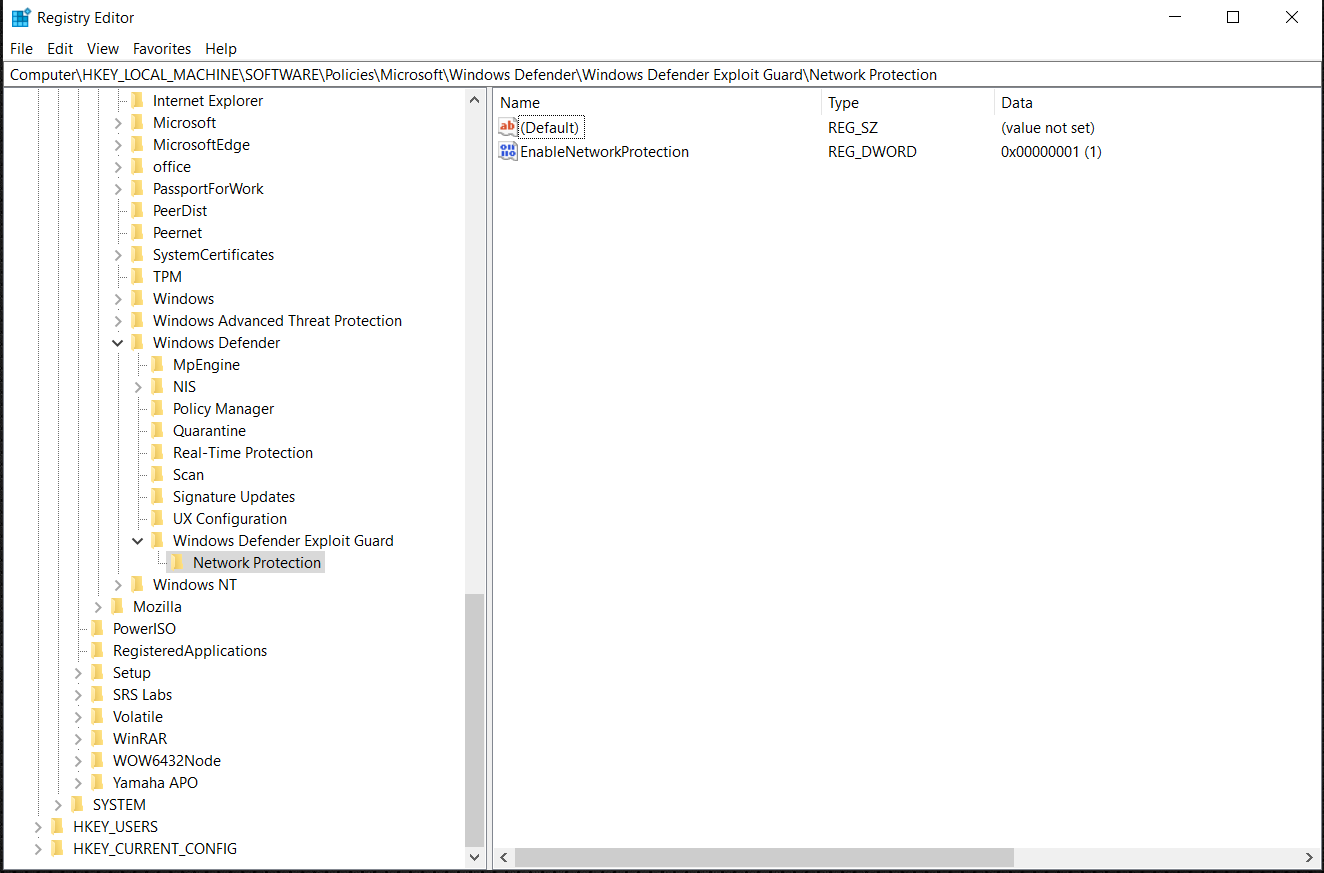
Check if network protection has been enabled on a local device by using Registry editor.
- Select the Start button in the task bar and type regedit to open Registry editor.
- Choose HKEY_LOCAL_MACHINE from the side menu.
- Navigate through the nested menus to SOFTWARE > Policies > Microsoft > Windows Defender > Windows Defender Exploit Guard > Network Protection.
If the Key is missing, Navigate to SOFTWARE > Microsoft > Windows Defender > Windows Defender Exploit Guard > Network Protection.
- Select EnableNetworkProtection to see the current state of network protection on the device:
- 0, or Off
- 1, or On
- 2, or Audit mode
Enable network protection
Enable network protection by using any of these methods:
- PowerShell
- Mobile Device Management (MDM)
- Microsoft Endpoint Manager
- Group Policy
- Microsoft Endpoint Configuration Manager
PowerShell
- Type powershell in the Start menu, right-click Windows PowerShell and select Run as administrator.
- Enter the following cmdlet:
PowerShell
Set-MpPreference -EnableNetworkProtection Enabled - Optional: Enable the feature in audit mode using the following cmdlet:
PowerShell
Set-MpPreference -EnableNetworkProtection AuditModeUse
Disabledinstead ofAuditModeorEnabledto turn off the feature.
Mobile device management (MDM)
Use the ./Vendor/MSFT/Policy/Config/Defender/EnableNetworkProtection configuration service provider (CSP) to enable or disable network protection or enable audit mode.
Microsoft Endpoint Manager
- Sign into the Microsoft Endpoint Manager admin center (https://endpoint.microsoft.com).
- Go to Devices > Configuration profiles > Create profile.
- In the Create a profile flyout, select Platform and choose the Profile Type as Templates.
- In the Template name, Choose Endpoint protection from the list of templates, and then select Create.
- Go to Endpoint protection > Basics, provide a name for your profile, and then select Next.
- In the Configuration settings section, go to Microsoft Defender Exploit Guard > Network filtering > Network protection > Enable or Audit. Select Next.
- Select the appropriate Scope tags, Assignments, and Applicability rules as required by your organization. Admins can set more requirements.
- Review all the information, and then select Create.
Group Policy
Use the following procedure to enable network protection on domain-joined computers or on a standalone computer.
- On a standalone computer, go to Start and then type and select Edit group policy.
-Or-
On a domain-joined Group Policy management computer, open the Group Policy Management Console, right-click the Group Policy Object you want to configure and select Edit.
- In the Group Policy Management Editor, go to Computer configuration and select Administrative templates.
- Expand the tree to Windows components > Microsoft Defender Antivirus > Windows Defender Exploit Guard > Network protection.
Note
On older versions of Windows, the group policy path may say “Windows Defender Antivirus” instead of “Microsoft Defender Antivirus.”
- Double-click the Prevent users and apps from accessing dangerous websites setting and set the option to Enabled. In the options section, you must specify one of the following options:
- Block – Users can’t access malicious IP addresses and domains.
- Disable (Default) – The Network protection feature won’t work. Users won’t be blocked from accessing malicious domains.
- Audit Mode – If a user visits a malicious IP address or domain, an event will be recorded in the Windows event log. However, the user won’t be blocked from visiting the address.
Important
To fully enable network protection, you must set the Group Policy option to Enabled and also select Block in the options drop-down menu.
Confirm network protection is enabled on a local computer by using Registry editor:
- Select Start and type regedit to open Registry Editor.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Windows Defender Exploit Guard\Network Protection\EnableNetworkProtection
- Select EnableNetworkProtection and confirm the value:
- 0=Off
- 1=On
- 2=Audit
Microsoft Endpoint Configuration Manager
- Open the Configuration Manager console.
- Go to Assets and Compliance > Endpoint Protection > Windows Defender Exploit Guard.
- Select Create Exploit Guard Policy from the ribbon to create a new policy.
- To edit an existing policy, select the policy, then select Properties from either the ribbon or the right-click menu. Edit the Configure network protection option from the Network Protection tab.
- On the General page, specify a name for the new policy and verify the Network protection option is enabled.
- On the Network protection page, select one of the following settings for the Configure network protection option:
- Block
- Audit
- Disabled
- Complete the rest of the steps, and save the policy.
- From the ribbon, select Deploy to deploy the policy to a collection.
Important
Once you deploy an Exploit Guard policy from Configuration Manager, the Exploit Guard settings will not be removed from the clients if you remove the deployment. Delete not supported is recorded in the Configuration Manager client’s ExploitGuardHandler.log if you remove the client’s Exploit Guard deployment. The following PowerShell script can be run under SYSTEM context to remove these settings:
$defenderObject = Get-WmiObject -Namespace "root/cimv2/mdm/dmmap" -Class "MDM_Policy_Config01_Defender02" -Filter "InstanceID='Defender' and ParentID='./Vendor/MSFT/Policy/Config'"
$defenderObject.AttackSurfaceReductionRules = $null
$defenderObject.AttackSurfaceReductionOnlyExclusions = $null
$defenderObject.EnableControlledFolderAccess = $null
$defenderObject.ControlledFolderAccessAllowedApplications = $null
$defenderObject.ControlledFolderAccessProtectedFolders = $null
$defenderObject.EnableNetworkProtection = $null
$defenderObject.Put()
$exploitGuardObject = Get-WmiObject -Namespace "root/cimv2/mdm/dmmap" -Class "MDM_Policy_Config01_ExploitGuard02" -Filter "InstanceID='ExploitGuard' and ParentID='./Vendor/MSFT/Policy/Config'"
$exploitGuardObject.ExploitProtectionSettings = $null
$exploitGuardObject.Put()