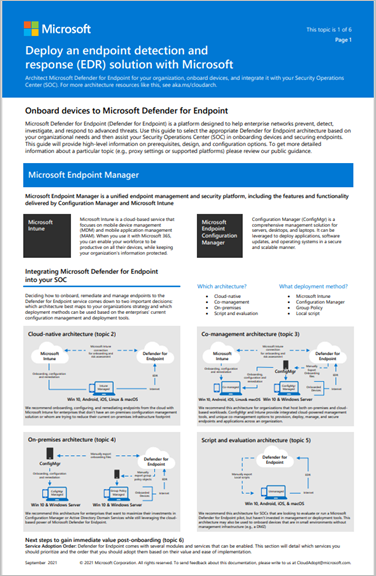
Plan your Microsoft Defender for Endpoint deployment so that you can maximize the security capabilities within the suite and better protect your enterprise from cyber threats.
This solution provides guidance on how to identify your environment architecture, select the type of deployment tool that best fits your needs, and guidance on how to configure capabilities.
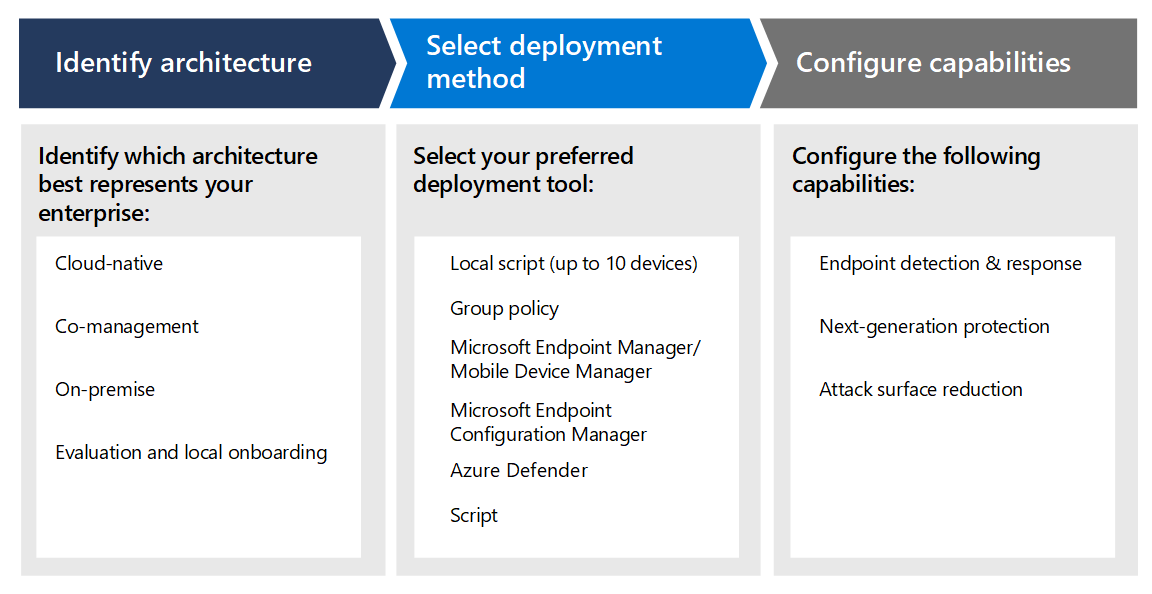
Step 1: Identify architecture
We understand that every enterprise environment is unique, so we’ve provided several options to give you the flexibility in choosing how to deploy the service.
Depending on your environment, some tools are better suited for certain architectures.
Use the following material to select the appropriate Defender for Endpoint architecture that best suites your organization.
| Item | Description |
|---|---|
 PDF | Visio |
The architectural material helps you plan your deployment for the following architectures:
|
Step 2: Select deployment method
| Endpoint | Deployment tool |
|---|---|
| Windows | Local script (up to 10 devices) Group Policy Microsoft Endpoint Manager/ Mobile Device Manager Microsoft Endpoint Configuration Manager VDI scripts Integration with Microsoft Defender for Cloud |
| macOS | Local script Microsoft Endpoint Manager JAMF Pro Mobile Device Management |
| Linux Server | Local script Puppet Ansible |
| iOS | Microsoft Endpoint Manager |
| Android | Microsoft Endpoint Manager |
The following table lists the supported endpoints and the corresponding deployment tool that you can use so that you can plan the deployment appropriately.
| Endpoint | Deployment tool |
|---|---|
| Windows | Local script (up to 10 devices) Group Policy Microsoft Endpoint Manager/ Mobile Device Manager Microsoft Endpoint Configuration Manager VDI scripts Integration with Microsoft Defender for Cloud |
| macOS | Local script Microsoft Endpoint Manager JAMF Pro Mobile Device Management |
| Linux Server | Local script Puppet Ansible |
| iOS | App-based |
| Android | Microsoft Endpoint Manager |
Step 3: Configure capabilities
After onboarding endpoints, configure the security capabilities in Defender for Endpoint so that you can maximize the robust security protection available in the suite. Capabilities include:
- Endpoint detection and response
- Next-generation protection
- Attack surface reduction

