There are some minimum requirements for onboarding devices to the service. Learn about the licensing, hardware and software requirements, and other configuration settings to onboard devices to the service.
Tip
- This article describes the minimum requirements for Microsoft Defender for Endpoint Plan 2. If you are looking for information about Defender for Endpoint Plan 1 (preview), see Requirements for Defender for Endpoint Plan 1 (preview).
- Learn about the latest enhancements in Defender for Endpoint: Defender for Endpoint Tech Community.
- Defender for Endpoint demonstrated industry-leading optics and detection capabilities in the recent MITRE evaluation. Read: Insights from the MITRE ATT&CK-based evaluation.
Licensing requirements
For information licensing requirements for Microsoft Defender for Endpoint, see Microsoft Defender for Endpoint licensing information.
For detailed licensing information, see the Product Terms site and work with your account team to learn more about the terms and conditions.
For more information on the array of features in Windows editions, see Compare Windows editions.
Browser requirements
Access to Defender for Endpoint is done through a browser, supporting the following browsers:
- Microsoft Edge
- Google Chrome
Note
While other browsers might work, the mentioned browsers are the ones supported.
Hardware and software requirements
Supported Windows versions
- Windows 7 SP1 Enterprise (Requires ESU for support.)
- Windows 7 SP1 Pro (Requires ESU for support.)
- Windows 8.1 Enterprise
- Windows 8.1 Pro
- Windows 11 Enterprise
- Windows 11 Education
- Windows 11 Pro
- Windows 11 Pro Education
- Windows 10 Enterprise
- Windows 10 Enterprise LTSC 2016 (or later)
- Windows 10 Education
- Windows 10 Pro
- Windows 10 Pro Education
- Windows server
- Windows Server 2008 R2 SP1 (Requires ESU for support)
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server, version 1803 or later
- Windows Server 2019
- Windows Server 2022
- Windows Virtual Desktop
Devices on your network must be running one of these editions.
The hardware requirements for Defender for Endpoint on devices are the same for the supported editions.
Cores: 2 minimum, 4 preferred Memory: 1 GB minimum, 4 preferred
For more information on supported versions of Windows 10, see (/windows/release-health/release-information).
Note
Machines running mobile versions of Windows (such as Windows CE and Windows 10 Mobile) aren’t supported.
Virtual Machines running Windows 10 Enterprise 2016 LTSB may encounter performance issues if run on non-Microsoft virtualization platforms.
For virtual environments, we recommend using Windows 10 Enterprise LTSC 2019 or later.
Other supported operating systems
Note
You’ll need to confirm the Linux distributions and versions of Android, iOS, and macOS are compatible with Defender for Endpoint for the integration to work.
Network and data storage and configuration requirements
When you run the onboarding wizard for the first time, you must choose where your Microsoft Defender for Endpoint-related information is stored: in the European Union, the United Kingdom, or the United States datacenter.
Note
- You cannot change your data storage location after the first-time setup.
- Review the Microsoft Defender for Endpoint data storage and privacy for more information on where and how Microsoft stores your data.
Diagnostic data settings
Note
Microsoft Defender for Endpoint doesn’t require any specific diagnostic level as long as it’s enabled.
Make sure that the diagnostic data service is enabled on all the devices in your organization. By default, this service is enabled. It’s good practice to check to ensure that you’ll get sensor data from them.
Use the command line to check the Windows diagnostic data service startup type
- Open an elevated command-line prompt on the device:
- Go to Start and type cmd.
- Right-click Command prompt and select Run as administrator.
- Enter the following command, and press Enter:
Console
sc qc diagtrackIf the service is enabled, then the result should look like the following screenshot:
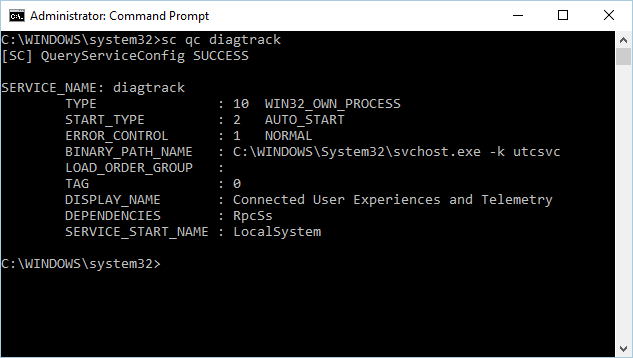
You’ll need to set the service to automatically start if the START_TYPE isn’t set to AUTO_START.
Use the command line to set the Windows diagnostic data service to automatically start
- Open an elevated command-line prompt on the endpoint:
- Go to Start and type cmd.
- Right-click Command prompt and select Run as administrator.
- Enter the following command, and press Enter:
Console
sc config diagtrack start=auto - A success message is displayed. Verify the change by entering the following command, and press Enter:
Console
sc qc diagtrack
Internet connectivity
Internet connectivity on devices is required either directly or through proxy.
The Defender for Endpoint sensor can use a daily average bandwidth of 5 MB to communicate with the Defender for Endpoint cloud service and report cyber data. One-off activities such as file uploads and investigation package collection aren’t included in this daily average bandwidth.
For more information on additional proxy configuration settings, see Configure device proxy and Internet connectivity settings.
Before you onboard devices, the diagnostic data service must be enabled. The service is enabled by default in Windows 10 and Windows 11.
Microsoft Defender Antivirus configuration requirement
The Defender for Endpoint agent depends on the ability of Microsoft Defender Antivirus to scan files and provide information about them.
Configure Security intelligence updates on the Defender for Endpoint devices whether Microsoft Defender Antivirus is the active antimalware or not. For more information, see Manage Microsoft Defender Antivirus updates and apply baselines.
When Microsoft Defender Antivirus isn’t the active antimalware in your organization and you use the Defender for Endpoint service, Microsoft Defender Antivirus goes on passive mode.
If your organization has turned off Microsoft Defender Antivirus through group policy or other methods, devices that are onboarded must be excluded from this group policy.
If you’re onboarding servers and Microsoft Defender Antivirus isn’t the active antimalware on your servers, Microsoft Defender Antivirus will either need to be configured to go on passive mode or uninstalled. The configuration is dependent on the server version. For more information, see Microsoft Defender Antivirus compatibility.
Note
Your regular group policy doesn’t apply to Tamper Protection, and changes to Microsoft Defender Antivirus settings will be ignored when Tamper Protection is on.
Microsoft Defender Antivirus Early Launch Antimalware (ELAM) driver is enabled
If you’re running Microsoft Defender Antivirus as the primary antimalware product on your devices, the Defender for Endpoint agent will successfully onboard.
If you’re running a third-party antimalware client and use Mobile Device Management solutions or Microsoft Endpoint Manager (current branch), you’ll need to ensure the Microsoft Defender Antivirus ELAM driver is enabled. For more information, see Ensure that Microsoft Defender Antivirus is not disabled by policy.

