Note
We’ve renamed Microsoft Cloud App Security. It’s now called Microsoft Defender for Cloud Apps. In the coming weeks, we’ll update the screenshots and instructions here and in related pages. For more information about the change, see this announcement. To learn more about the recent renaming of Microsoft security services, see the Microsoft Ignite Security blog.
Microsoft Defender for Cloud Apps integrates with Microsoft Defender for Endpoint natively. The integration simplifies roll out of Cloud Discovery, extends Cloud Discovery capabilities beyond your corporate network, and enables device-based investigation. Microsoft Defender for Endpoint is a security platform for intelligent protection, detection, investigation, and response. Defender for Endpoint protects endpoints from cyber threats, detects advanced attacks and data breaches, automates security incidents, and improves security posture.
Defender for Cloud Apps uses the traffic information collected by Defender for Endpoint about the cloud apps and services being accessed from IT-managed Windows 10 devices. The native integration enables you to run Cloud Discovery on any device in the corporate network, using public Wi-Fi, while roaming, and over remote access. It also enables device-based investigation.
The integration doesn’t require any additional deployment and works out of the box. You don’t need to route or mirror traffic from your endpoints or do complex integration steps. Logs from your endpoints sent to Defender for Cloud Apps provide user information for traffic activities. Defender for Endpoint network activity provides device context. Pairing device context with the username provides a full picture across your network enabling you to determine which user did which activity from which device.
Additionally, when you identify a risky user, you can check all the devices the user accessed to detect potential risks. If you identify a risky device, check all the users who used it to detect further potential risks.
Once traffic information is collected, you’re ready to deep dive into cloud app use in your organization. Defender for Cloud Apps takes advantage of Defender for Endpoint Network Protection capabilities to block endpoint device access to cloud apps. You can block apps by tagging them as Unsanctioned in the portal. Based on the comprehensive usage and risk assessment of each unsanctioned app, the app’s domains are used to create domain indicators in the Defender for Endpoint portal. Microsoft Defender Antivirus, running on endpoint devices, uses the domain indicators to block access to these apps.
Note
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
Prerequisites
- Microsoft Defender for Cloud Apps license
- Microsoft Defender for Endpoint Plan 2 license
- Windows 10 version 1709 (OS Build 16299.1085 with KB4493441), Windows 10 version 1803 (OS Build 17134.704 with KB4493464), Windows 10 version 1809 (OS Build 17763.379 with KB4489899) or later Windows 10 and Windows 11 versions
- Microsoft Defender Antivirus
How it works
On its own, Defender for Cloud Apps collects logs from your endpoints using either logs you upload or by configuring automatic log upload. Native integration enables you to take advantage of the logs Defender for Endpoint’s agent creates when it runs on Windows and monitors network transactions. Use this information for Shadow IT discovery across the Windows devices on your network.
To enable you to perform Cloud Discovery across other platforms, it’s best to use both the Defender for Cloud Apps log collector, along with Defender for Endpoint integration to monitor your Windows 10 and Windows 11 devices.
Watch our videos showing the benefits of using Defender for Endpoint with Defender for Cloud Apps.
How to integrate Microsoft Defender for Endpoint with Defender for Cloud Apps
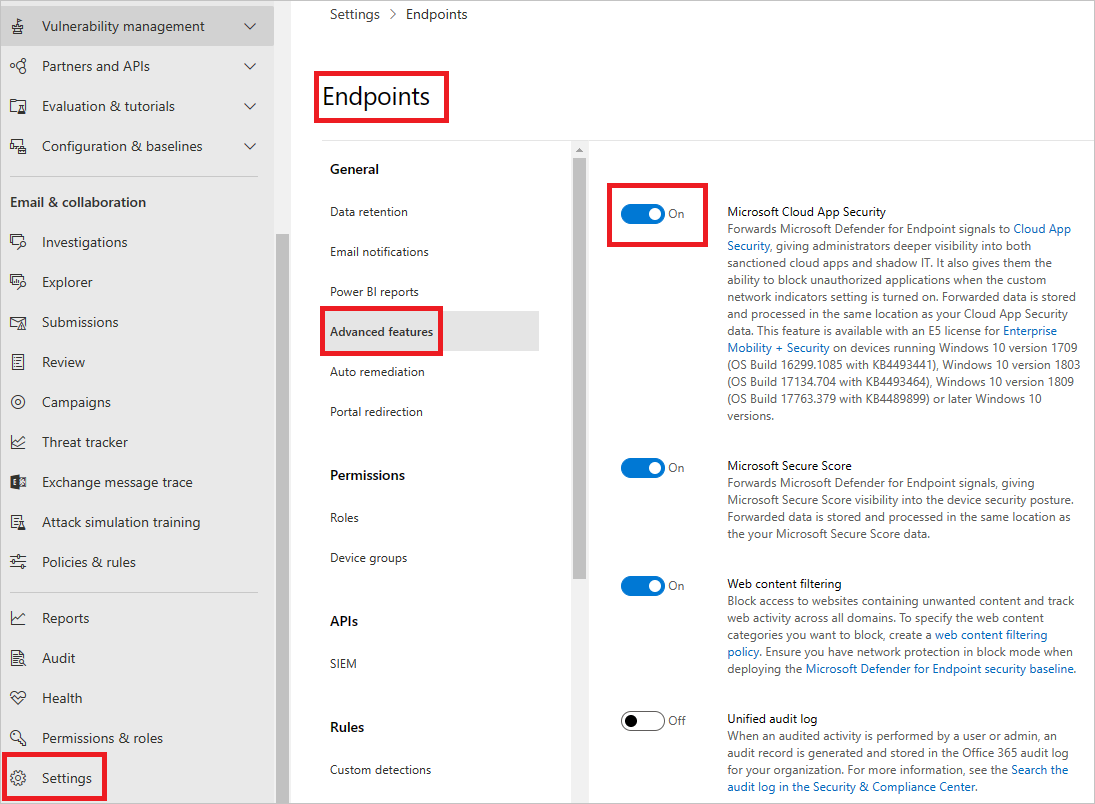
To enable Defender for Endpoint integration with Defender for Cloud Apps:
- In Microsoft 365 Defender, from the navigation pane, select Settings.
- Select Endpoints.
- Under General, select Advanced features.
- Toggle the Microsoft Defender for Cloud Apps to On.
- Select Apply.
Note
It takes up to two hours after you enable the integration for the data to show up in Defender for Cloud Apps.
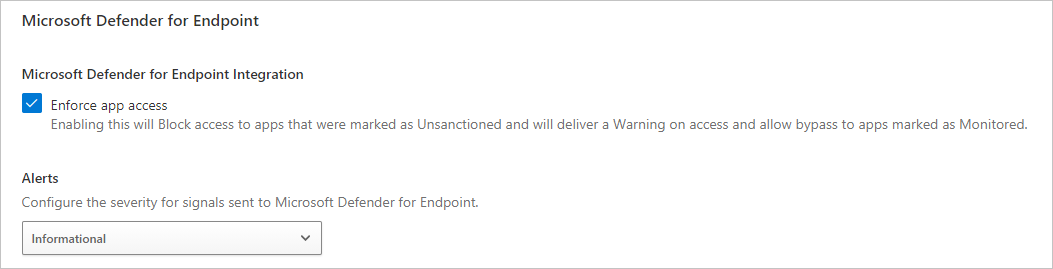
To configure the severity for alerts sent to Microsoft Defender for Endpoint:
- In Defender for Cloud Apps, select the Settings icon, and then select Microsoft Defender for Endpoint.
- Under Alerts, select the global severity level for alerts.
- Select Save.