This offering is available to GCC, GCC High, and DoD customers and is based on the same prevention, detection, investigation, and remediation as the commercial version. However, there are some differences in the availability of capabilities for this offering.
Note
If you are a GCC customer using Defender for Endpoint in Commercial, please refer to the public documentation pages.
Licensing requirements
Microsoft Defender for Endpoint for US Government customers requires one of the following Microsoft volume licensing offers:
Desktop licensing
| GCC | GCC High | DoD |
|---|---|---|
| Microsoft 365 GCC G5 | Microsoft 365 E5 for GCC High | Microsoft 365 G5 for DOD |
| Microsoft 365 G5 Security GCC | Microsoft 365 G5 Security for GCC High | Microsoft 365 G5 Security for DOD |
| Microsoft Defender for Endpoint – GCC | Microsoft Defender for Endpoint for GCC High | Microsoft Defender for Endpoint for DOD |
| Windows 10 Enterprise E5 GCC | Windows 10 Enterprise E5 for GCC High | Windows 10 Enterprise E5 for DOD |
Server licensing
| GCC | GCC High | DoD |
|---|---|---|
| Microsoft Defender for Endpoint Server GCC | Microsoft Defender for Endpoint Server for GCC High | Microsoft Defender for Endpoint Server for DOD |
| Microsoft Defender for servers | Microsoft Defender for servers – Government | Microsoft Defender for servers – Government |
Portal URLs
The following are the Microsoft Defender for Endpoint portal URLs for US Government customers:
| Customer type | Portal URL |
|---|---|
| GCC | https://security.microsoft.com |
| GCC High | https://securitycenter.microsoft.us |
| DoD | https://securitycenter.microsoft.us |
Note
If you are a GCC customer and in the process of moving from Microsoft Defender for Endpoint commercial to GCC, use https://transition.security.microsoft.com to access your Microsoft Defender for Endpoint commercial data.
Endpoint versions
Standalone OS versions
The following OS versions are supported:
| OS version | GCC | GCC High | DoD |
|---|---|---|---|
| Windows 11 |  |
 |
 |
| Windows 10, version 21H1 and above |  |
 |
 |
| Windows 10, version 20H2 (with KB4586853 1) |  |
 |
 |
| Windows 10, version 2004 (with KB4586853 1) |  |
 |
 |
| Windows 10, version 1909 (with KB4586819 1) |  |
 |
 |
| Windows 10, version 1903 (with KB4586819 1) |  |
 |
 |
| Windows 10, version 1809 (with KB4586839 1) |  |
 |
 |
| Windows 10, version 1803 (with KB4598245 1) |  |
 |
 |
| Windows 10, version 1709 |  Note: Won’t be supported |
 With KB4499147 1 With KB4499147 1Note: Deprecated, please upgrade |
 Note: Won’t be supported |
| Windows 10, version 1703 and earlier |  Note: Won’t be supported |
 Note: Won’t be supported |
 Note: Won’t be supported |
| Windows Server 2022 |  |
 |
 |
| Windows Server 2019 (with KB4586839 1) |  |
 |
 |
| Windows Server 2016 (Modern) 2 |  Public preview |
 Public preview |
 Public preview |
| Windows Server 2012 R2 (Modern) 2 |  Public preview |
 Public preview |
 Public preview |
| Windows Server 2016 (Legacy) 3 |  |
 |
 |
| Windows Server 2012 R2 (Legacy) 3 |  |
 |
 |
| Windows Server 2008 R2 SP1 (Legacy) 3 |  |
 |
 |
| Windows 8.1 Enterprise (Legacy) 3 |  |
 |
 |
| Windows 8 Pro (Legacy) 3 |  |
 |
 |
| Windows 7 SP1 Enterprise (Legacy) 3 |  |
 |
 |
| Windows 7 SP1 Pro (Legacy) 3 |  |
 |
 |
| Linux |  |
 |
 |
| macOS |  |
 |
 |
| Android |  In development In development |
 In development In development |
 In development In development |
| iOS |  In development In development |
 In development In development |
 In development In development |
Note
1 The patch must be deployed prior to device onboarding in order to configure Defender for Endpoint to the correct environment.
2 Learn about the unified modern solution for Windows 2016 and 2012 R2. If you have previously onboarded your servers using MMA, follow the guidance provided in Server migration to migrate to the new solution.
3 When using Microsoft Monitoring Agent you’ll need to choose “Azure US Government” under “Azure Cloud” if using the setup wizard, or if using a command line or a script – set the “OPINSIGHTS_WORKSPACE_AZURE_CLOUD_TYPE” parameter to 1.
The minimum MMA supported version is 10.20.18029 (March 2020).
OS versions when using Microsoft Defender for servers
The following OS versions are supported when using Microsoft Defender for servers:
| OS version | GCC | GCC High | DoD |
|---|---|---|---|
| Windows Server 2022 |  |
 |
 |
| Windows Server 2019 |  |
 |
 |
| Windows Server 2016 |  |
 |
 |
| Windows Server 2012 R2 |  |
 |
 |
| Windows Server 2008 R2 SP1 |  |
 |
 |
Required connectivity settings
If a proxy or firewall is blocking all traffic by default and allowing only specific domains through, add the domains listed in the downloadable sheet to the allowed domains list.
The following downloadable spreadsheet lists the services and their associated URLs your network must be able to connect to. Verify there are no firewall or network-filtering rules that would deny access to these URLs, or create an allow rule specifically for them.
| Spreadsheet of domains list | Description |
|---|---|
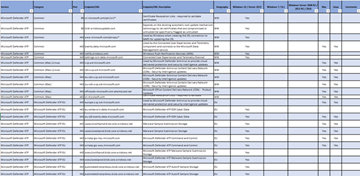 |
Spreadsheet of specific DNS records for service locations, geographic locations, and OS.Download the spreadsheet here. |
For more information, see Configure device proxy and Internet connectivity settings.
Note
The spreadsheet contains commercial URLs as well, make sure you check the “US Gov” tabs.
When filtering, look for the records labeled as “US Gov” and your specific cloud under the geography column.
API
Instead of the public URIs listed in our API documentation, you’ll need to use the following URIs:
| Endpoint type | GCC | GCC High & DoD |
|---|---|---|
| Login | https://login.microsoftonline.com |
https://login.microsoftonline.us |
| Defender for Endpoint API | https://api-gcc.securitycenter.microsoft.us |
https://api-gov.securitycenter.microsoft.us |
| SIEM | https://wdatp-alertexporter-us.gcc.securitycenter.windows.us |
https://wdatp-alertexporter-us.securitycenter.windows.us |
Feature parity with commercial
Defender for Endpoint for US Government customers doesn’t have complete parity with the commercial offering. While our goal is to deliver all commercial features and functionality to our US Government customers, there are some capabilities not yet available we want to highlight.
These are the known gaps:
| Feature name | GCC | GCC High | DoD |
|---|---|---|---|
| Network assessments |  In development In development |
 In development In development |
 In development In development |
| Network discovery |  |
 In development In development |
 In development In development |
| Reports: Attack surface reduction, Device Control, Device health, Firewall |  In development In development |
 In development In development |
 In development In development |
| Web content filtering |  In development In development |
 In development In development |
 In development In development |

