The Microsoft Defender for Endpoint evaluation lab is designed to eliminate the complexities of device and environment configuration so that you can focus on evaluating the capabilities of the platform, running simulations, and seeing the prevention, detection, and remediation features in action.
With the simplified set-up experience, you can focus on running your own test scenarios and the pre-made simulations to see how Defender for Endpoint performs.
You’ll have full access to the powerful capabilities of the platform such as automated investigations, advanced hunting, and threat analytics, allowing you to test the comprehensive protection stack that Defender for Endpoint offers.
You can add Windows 10, Windows 11, Windows Server 2019, Windows Server 2016, and Linux (Ubuntu) devices that come pre-configured to have the latest OS versions and the right security components in place as well as Office 2019 Standard installed.
You can also install threat simulators. Defender for Endpoint has partnered with industry leading threat simulation platforms to help you test out the Defender for Endpoint capabilities without having to leave the portal.
Install your preferred simulator, run scenarios within the evaluation lab, and instantly see how the platform performs – all conveniently available at no extra cost to you. You’ll also have convenient access to wide array of simulations which you can access and run from the simulations catalog.
Before you begin
You’ll need to fulfill the licensing requirements or have trial access to Microsoft Defender for Endpoint to access the evaluation lab.
You must have Manage security settings permissions to:
- Create the lab
- Create devices
- Reset password
- Create simulations
If you enabled role-based access control (RBAC) and created at least a one machine group, users must have access to All machine groups.
For more information, see Create and manage roles.
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
Get started with the lab
You can access the lab from the menu. In the navigation menu, select Evaluation and tutorials > Evaluation lab.
Note
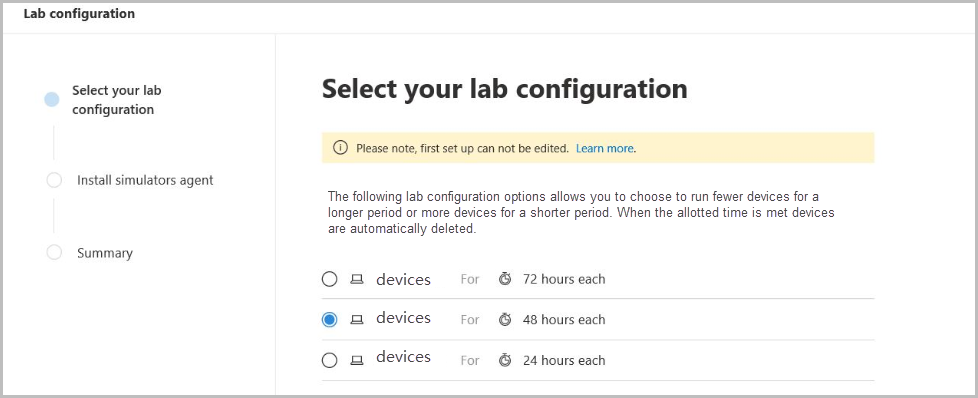
- Depending the type of environment structure you select, devices will be available for the specified number of hours from the day of activation.
- Each environment is provisioned with a limited set of test devices. When you’ve used up the provisioned devices and have deleted them, you can request for more devices.
- You can request for lab resources once a month.
Already have a lab? Make sure to enable the new threat simulators and have active devices.
Setup the evaluation lab
- In the navigation pane, select Evaluation & tutorials > Evaluation lab, then select Setup lab.

- Depending on your evaluation needs, you can choose to setup an environment with fewer devices for a longer period or more devices for a shorter period. Select your preferred lab configuration then select Next.
- (Optional) You can choose to install threat simulators in the lab.
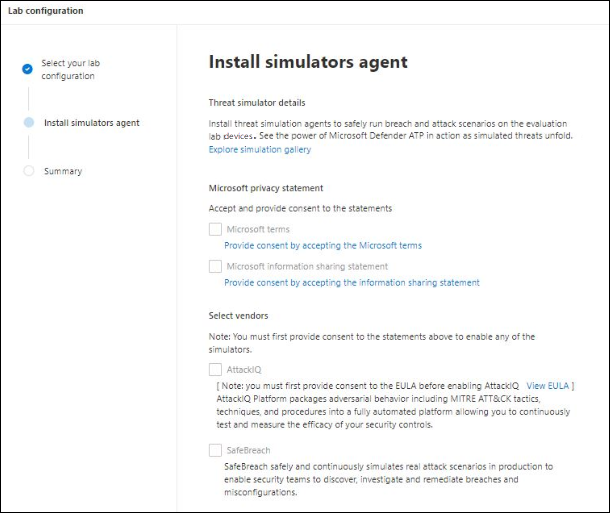
Important
You’ll first need to accept and provide consent to the terms and information sharing statements.
- Select the threat simulation agent you’d like to use and enter your details. You can also choose to install threat simulators at a later time. If you choose to install threat simulation agents during the lab setup, you’ll enjoy the benefit of having them conveniently installed on the devices you add.
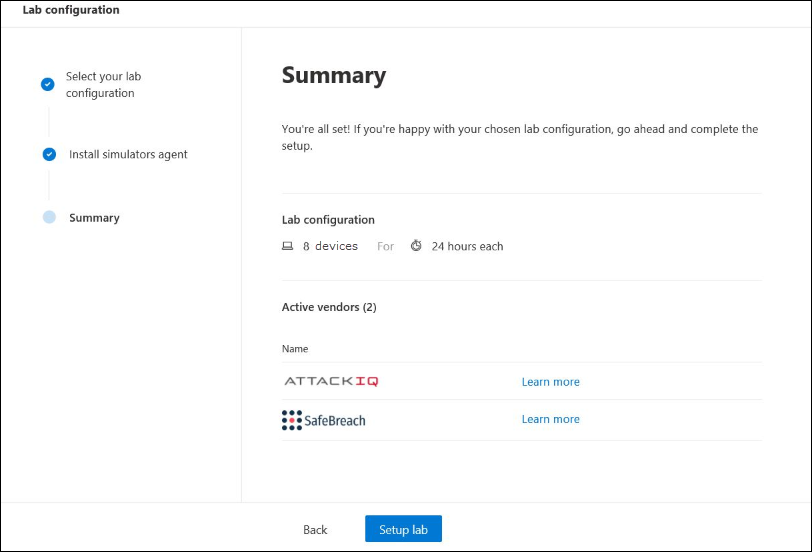
- Review the summary and select Setup lab.
After the lab setup process is complete, you can add devices and run simulations.
Add devices
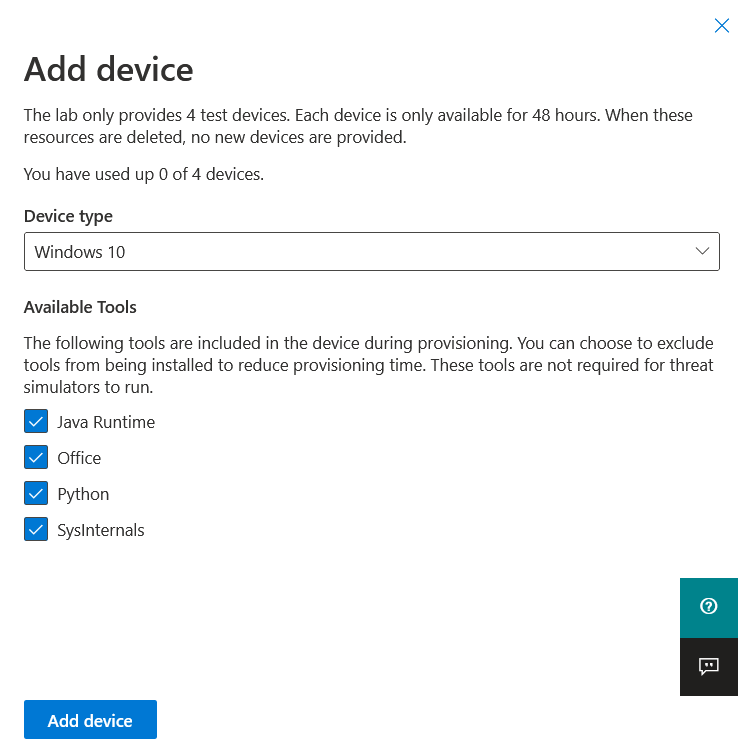
When you add a device to your environment, Defender for Endpoint sets up a well-configured device with connection details. You can add Windows 10, Windows 11, Windows Server 2019, Windows Server 2016, and Linux (Ubuntu).
The device will be configured with the most up-to-date version of the OS and Office 2019 Standard as well as other apps such as Java, Python, and SysIntenals.
If you chose to add a threat simulator during the lab setup, all devices will have the threat simulator agent installed in the devices that you add.
The device will automatically be onboarded to your tenant with the recommended Windows security components turned on and in audit mode – with no effort on your side.
The following security components are pre-configured in the test devices:
- Attack surface reduction
- Block at first sight
- Controlled folder access
- Exploit protection
- Network protection
- Potentially unwanted application detection
- Cloud-delivered protection
- Microsoft Defender SmartScreen
Note
Microsoft Defender Antivirus will be on (not in audit mode). If Microsoft Defender Antivirus blocks you from running your simulation, you can turn off real-time protection on the device through Windows Security. For more information, see Configure always-on protection.
Automated investigation settings will be dependent on tenant settings. It will be configured to be semi-automated by default. For more information, see Overview of Automated investigations.
Note
The connection to the test devices is done using RDP. Make sure that your firewall settings allow RDP connections.
- From the dashboard, select Add device.
- Choose the type of device to add. You can choose to add Windows 10, Windows 11, Windows Server 2019, Windows Server 2016, and Linux (Ubuntu).
Note
If something goes wrong with the device creation process, you’ll be notified and you’ll need to submit a new request. If the device creation fails, it will not be counted against the overall allowed quota.
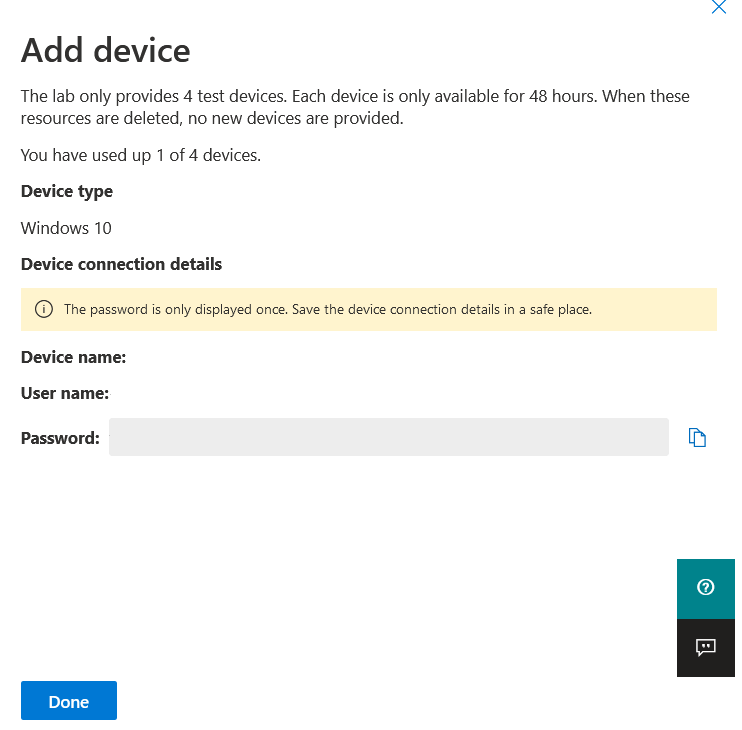
- The connection details are displayed. Select Copy to save the password for the device.
Note
The password is only displayed once. Be sure to save it for later use.
- Device set up begins. This can take up to approximately 30 minutes.
- See the status of test devices, the risk and exposure levels, and the status of simulator installations by selecting the Devices tab.
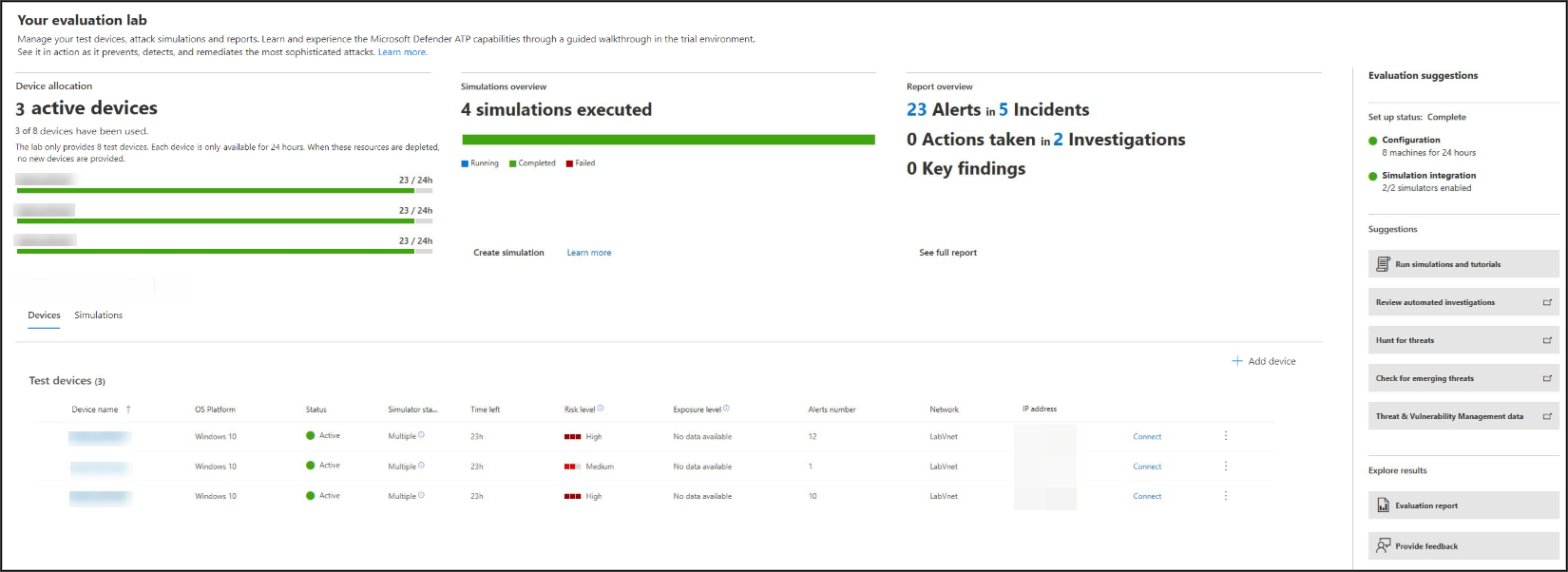
Tip
In the Simulator status column, you can hover over the information icon to know the installation status of an agent.
Request for more devices
When all existing devices are used and deleted, you can request for more devices. You can request for lab resources once a month.
- From the evaluation lab dashboard, select Request for more devices.
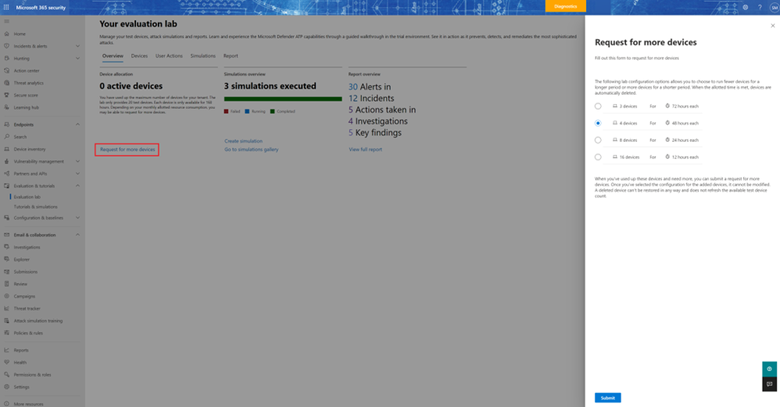
- Choose your configuration.
- Submit the request.
When the request is submitted successfully you’ll see a green confirmation banner and the date of the last submission.
You can find the status of your request in the User Actions tab, which will be approved in a matter of hours.
When approved, the requested devices will be added to your lab set up and you’ll be able to create more devices.
Tip
To get more out of your lab, don’t forget to check out our simulations library.
Simulate attack scenarios
Use the test devices to run your own attack simulations by connecting to them.
You can simulate attack scenarios using:
- The “Do It Yourself” attack scenarios
- Threat simulators
You can also use Advanced hunting to query data and Threat analytics to view reports about emerging threats.
Do-it-yourself attack scenarios
If you are looking for a pre-made simulation, you can use our “Do It Yourself” attack scenarios. These scripts are safe, documented, and easy to use. These scenarios will reflect Defender for Endpoint capabilities and walk you through investigation experience.
Note
The connection to the test devices is done using RDP. Make sure that your firewall settings allow RDP connections.
- Connect to your device and run an attack simulation by selecting Connect.
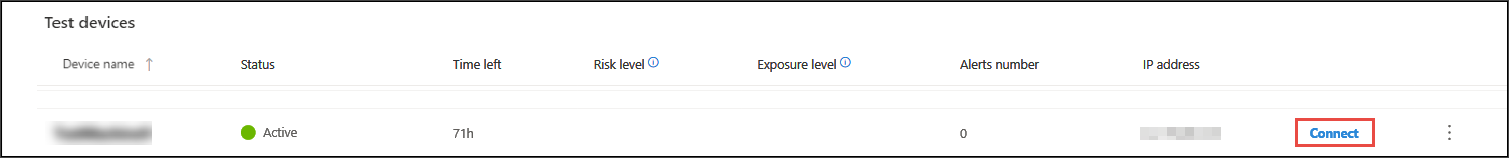
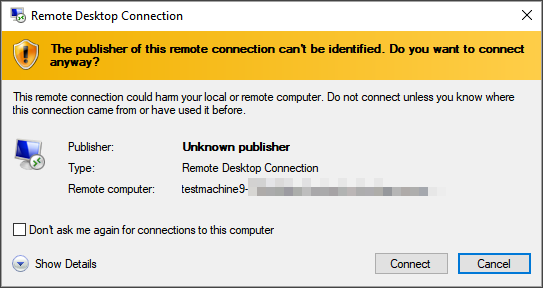
- Save the RDP file and launch it by selecting Connect.
Note
If you don’t have a copy of the password saved during the initial setup, you can reset the password by selecting Reset password from the menu:
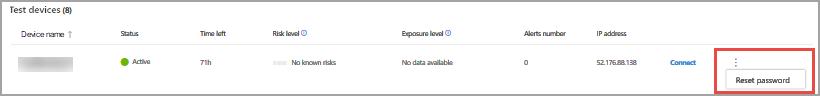
The device will change it’s state to “Executing password reset”, then you’ll be presented with your new password in a few minutes.
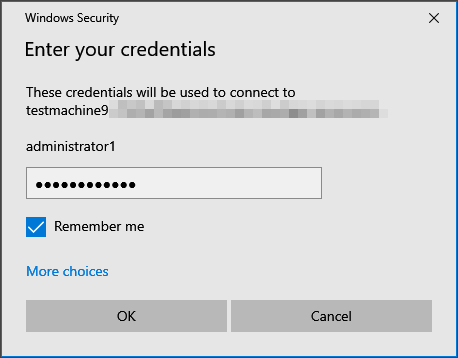
- Enter the password that was displayed during the device creation step.
- Run Do-it-yourself attack simulations on the device.
Threat simulator scenarios
If you chose to install any of the supported threat simulators during the lab setup, you can run the built-in simulations on the evaluation lab devices.
Running threat simulations using third-party platforms is a good way to evaluate Microsoft Defender for Endpoint capabilities within the confines of a lab environment.
Note
Before you can run simulations, ensure the following requirements are met:
- Devices must be added to the evaluation lab
- Threat simulators must be installed in the evaluation lab
- From the portal select Create simulation.
- Select a threat simulator.
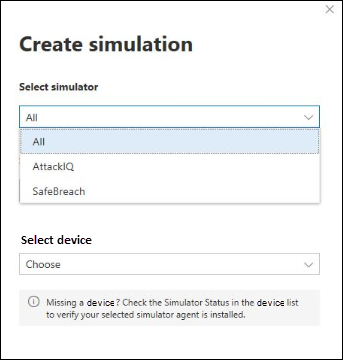
- Choose a simulation or look through the simulation gallery to browse through the available simulations.
You can get to the simulation gallery from:
- The main evaluation dashboard in the Simulations overview tile or
- By navigating from the navigation pane Evaluation and tutorials > Simulation & tutorials, then select Simulations catalog.
- Select the devices where you’d like to run the simulation on.
- Select Create simulation.
- View the progress of a simulation by selecting the Simulations tab. View the simulation state, active alerts, and other details.
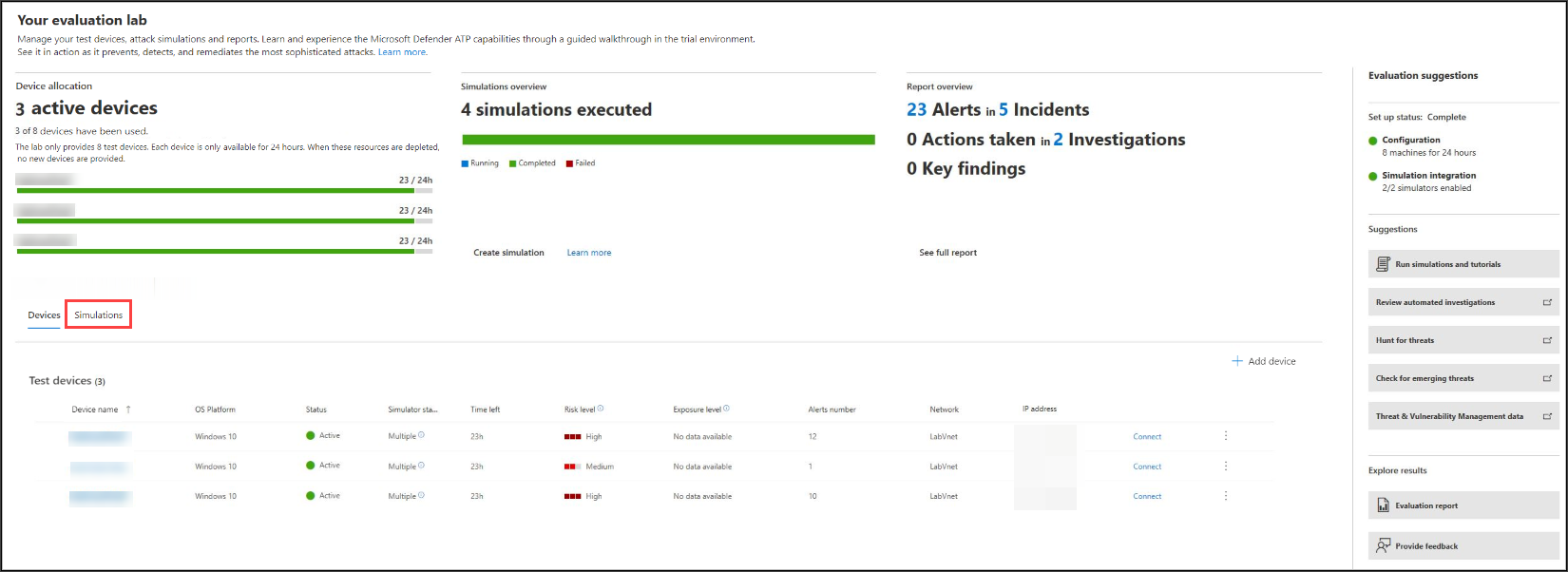
After running your simulations, we encourage you to walk through the lab progress bar and explore Microsoft Defender for Endpoint triggered an automated investigation and remediation. Check out the evidence collected and analyzed by the feature.
Hunt for attack evidence through advanced hunting by using the rich query language and raw telemetry and check out some world-wide threats documented in Threat analytics.
Simulation gallery
Microsoft Defender for Endpoint has partnered with various threat simulation platforms to give you convenient access to test the capabilities of the platform right from the within the portal.
View all the available simulations by going to Simulations and tutorials > Simulations catalog from the menu.
A list of supported third-party threat simulation agents are listed, and specific types of simulations along with detailed descriptions are provided on the catalog.
You can conveniently run any available simulation right from the catalog.
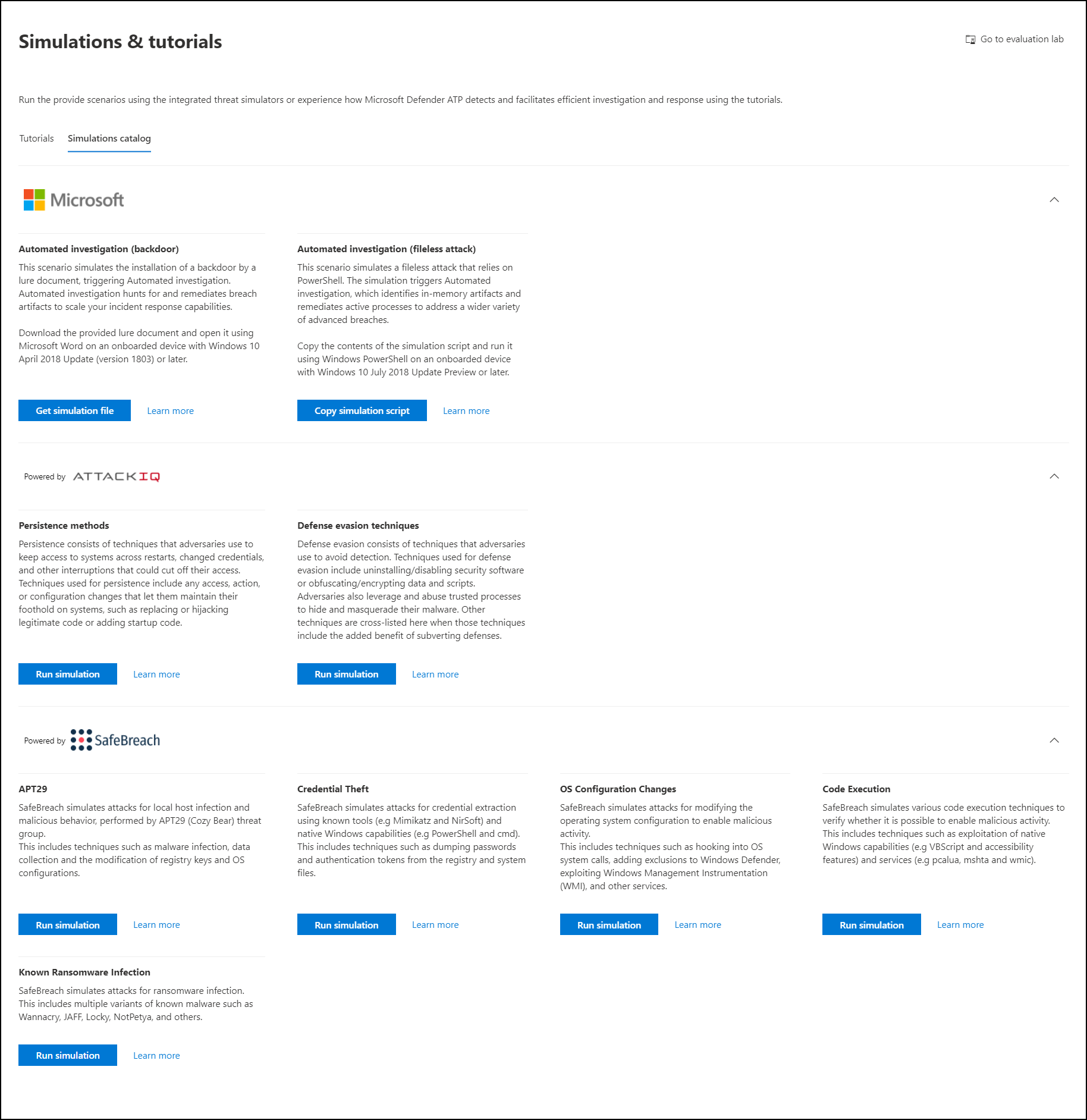
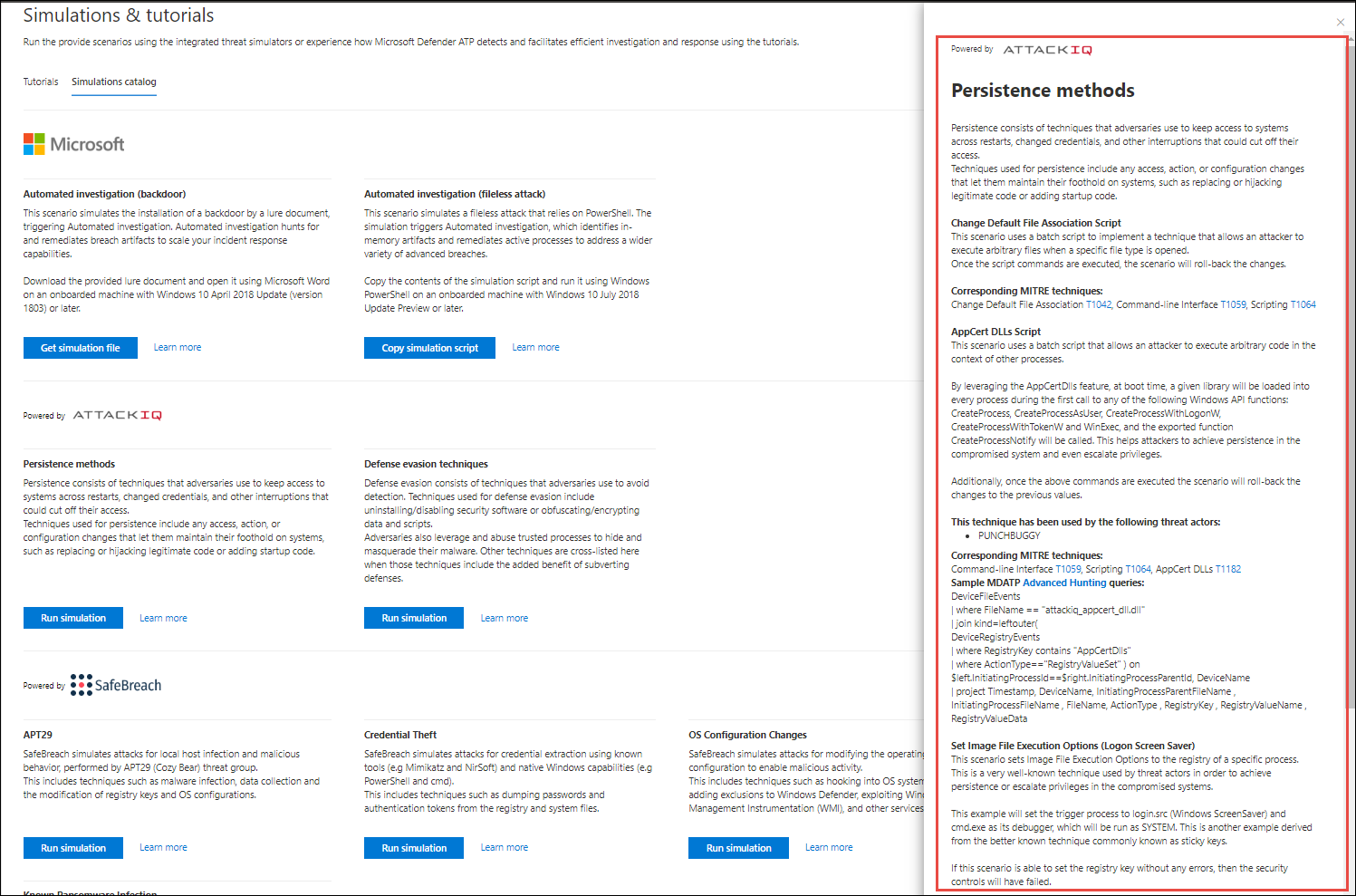
Each simulation comes with an in-depth description of the attack scenario and references such as the MITRE attack techniques used and sample Advanced hunting queries you run.
Examples:
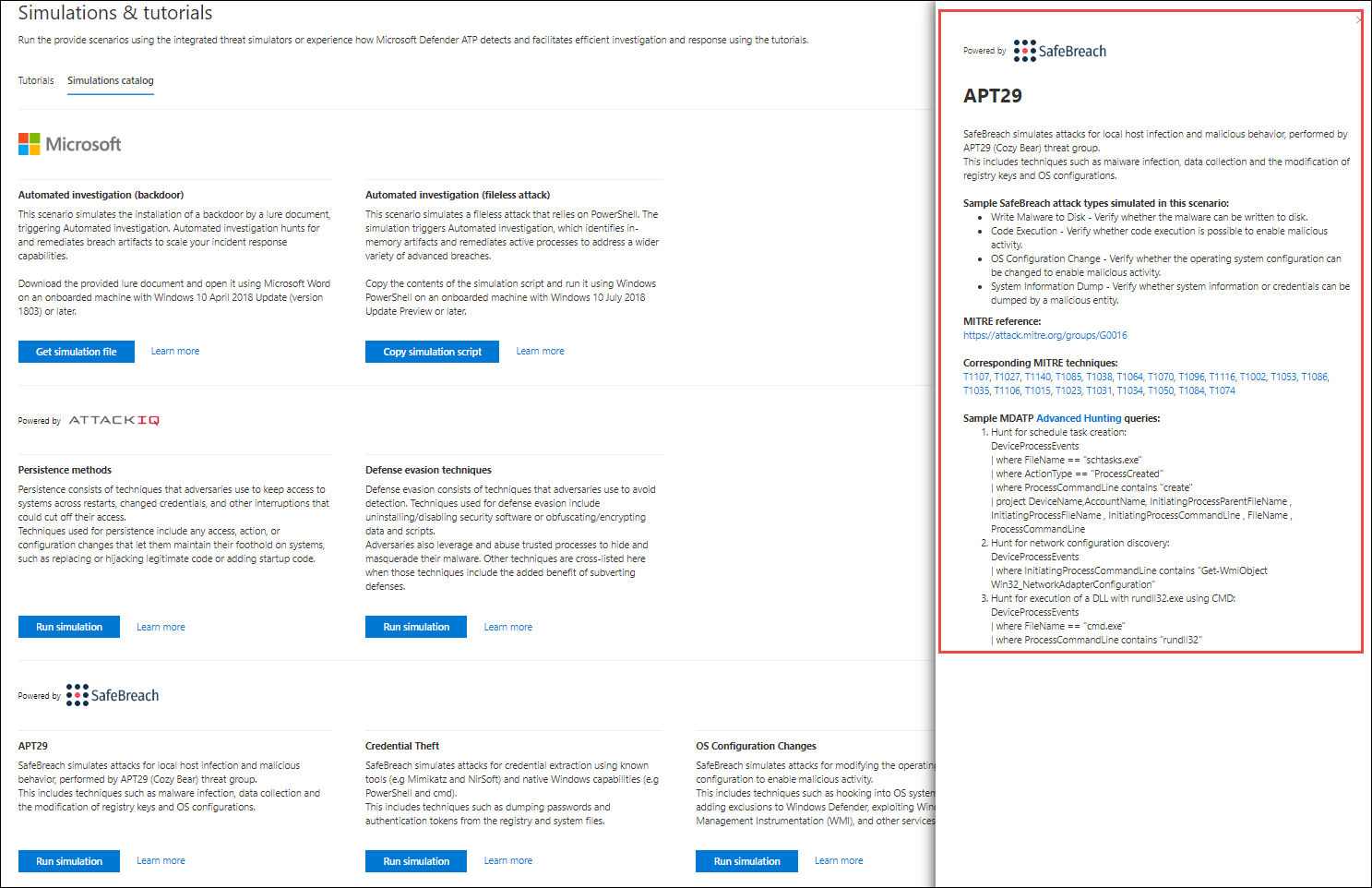
Evaluation report
The lab reports summarize the results of the simulations conducted on the devices.
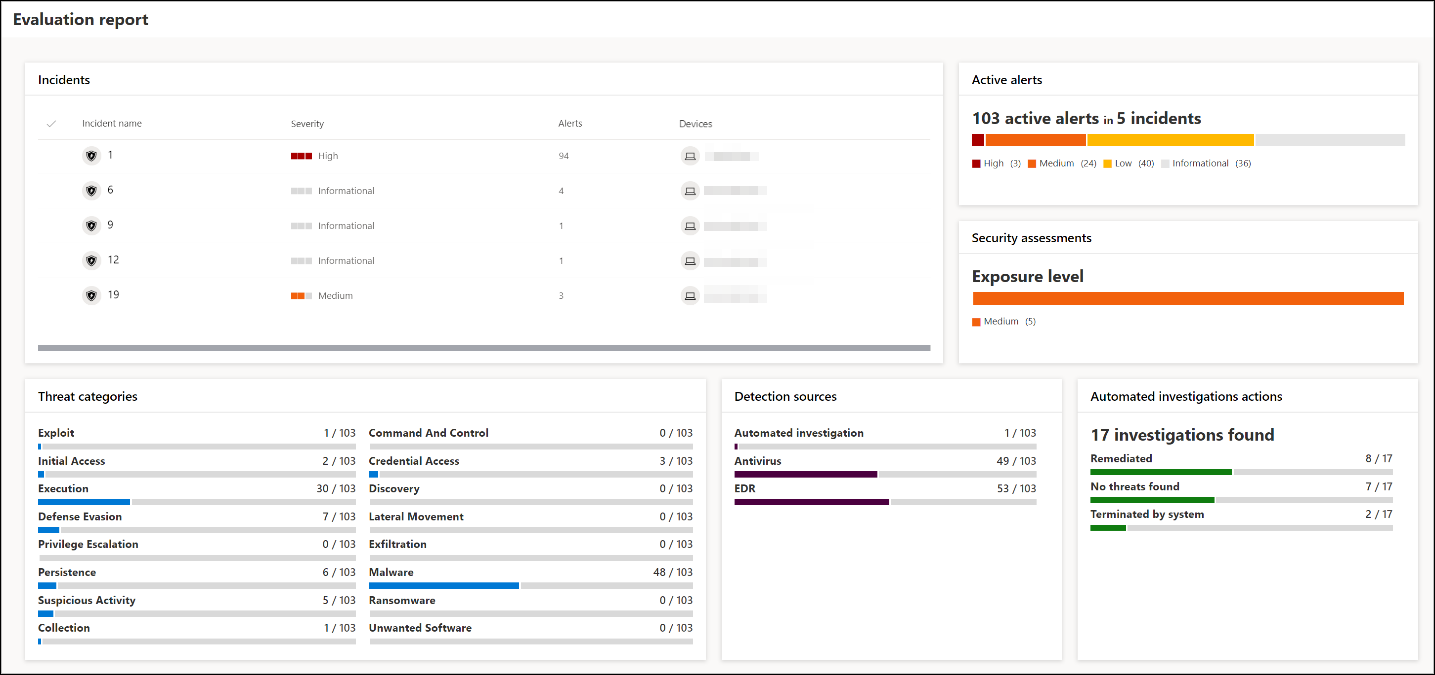
At a glance, you’ll quickly be able to see:
- Incidents that were triggered
- Generated alerts
- Assessments on exposure level
- Threat categories observed
- Detection sources
- Automated investigations
Provide feedback
Your feedback helps us get better in protecting your environment from advanced attacks. Share your experience and impressions from product capabilities and evaluation results.
Let us know what you think, by selecting Provide feedback.