The Defender for Endpoint device timeline provides a chronological view of the events and associated alerts observed on a device. This list of events provides full visibility into any events, files, and IP addresses observed on the device. The list can sometimes be lengthy. Device timeline event flags help you track events that could be related.
After you’ve gone through a device timeline, you can sort, filter, and export the specific events that you flagged.
While navigating the device timeline, you can search and filter for specific events. You can set event flags by:
- Highlighting the most important events
- Marking events that requires deep dive
- Building a clean breach timeline
Flag an event
- Find the event that you want to flag
- Click the flag icon in the Flag column.
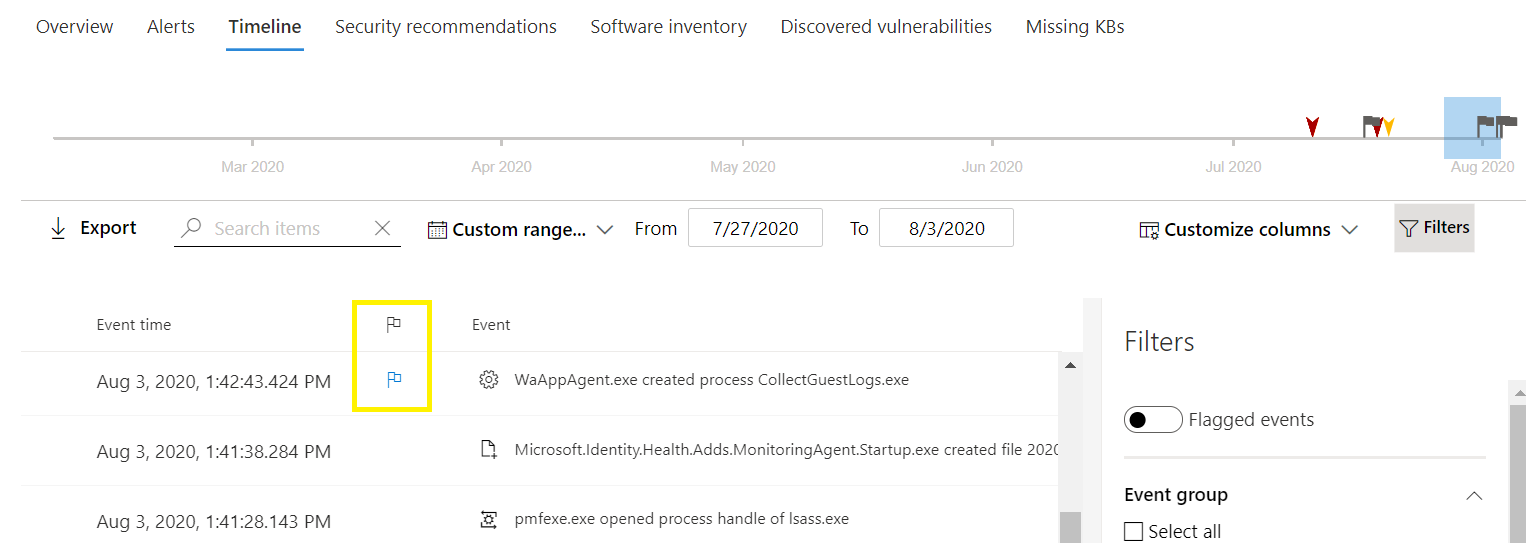
- Click the flag icon in the Flag column.

View flagged events
- In the timeline Filters section, enable Flagged events.
- Click Apply. Only flagged events are displayed. You can apply additional filters by clicking on the time bar. This will only show events prior to the flagged event.
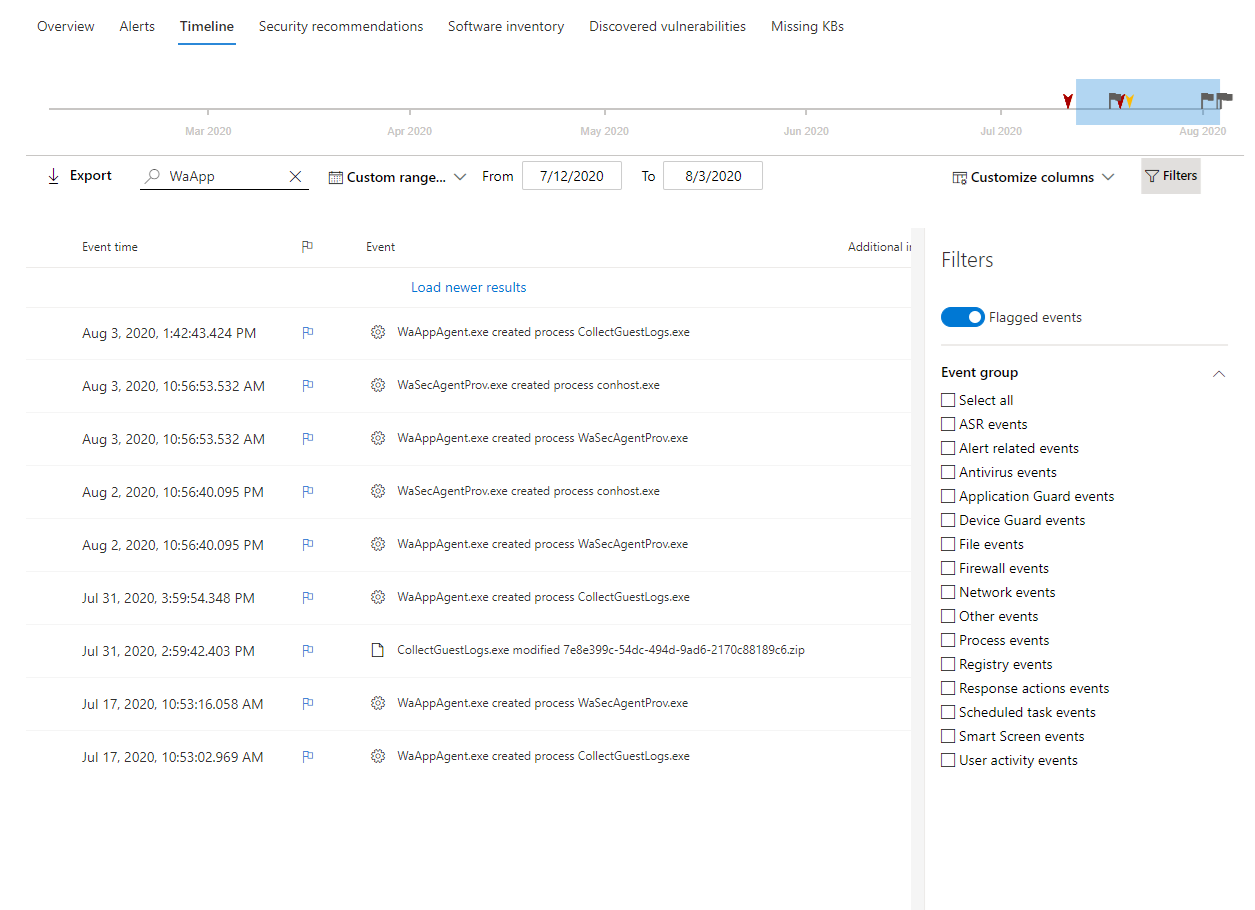
- Click Apply. Only flagged events are displayed. You can apply additional filters by clicking on the time bar. This will only show events prior to the flagged event.


