Note
The Group Policy management of this product is now generally available (4.18.2106): See Tech Community blog: Protect your removable storage and printer with Microsoft Defender for Endpoint
Microsoft Defender for Endpoint Device Control Removable Storage Access Control enables you to do the following task:
- auditing, allowing or preventing the read, write or execute access to removable storage with or without exclusion
| Privilege | Permission |
|---|---|
| Access | Read, Write, Execute |
| Action Mode | Audit, Allow, Prevent |
| CSP Support | Yes |
| GPO Support | Yes |
| User-based Support | Yes |
| Machine-based Support | Yes |
Prepare your endpoints
Deploy Removable Storage Access Control on Windows 10 and Windows 11 devices that have antimalware client version 4.18.2103.3 or later.
- 4.18.2104 or later: Add SerialNumberId, VID_PID, filepath-based GPO support, ComputerSid
- 4.18.2105 or later: Add Wildcard support for HardwareId/DeviceId/InstancePathId/FriendlyNameId/SerialNumberId, the combination of specific user on specific machine, removeable SSD (a SanDisk Extreme SSD)/USB Attached SCSI (UAS) support
- 4.18.2107 or later: Add Windows Portable Device (WPD) support (for mobile devices, such as tablets); add AccountName into advanced hunting
Note
None of Windows Security components need to be active as you can run Removable Storage Access Control independent of Windows Security status.
Policy properties
You can use the following properties to create a removable storage group:
Note
Comments using XML comment notation <!-- COMMENT --> can be used in the Rule and Group XML files, but they must be inside the first XML tag, not the first line of the XML file.
Removable Storage Group
| Property Name | Description | Options |
|---|---|---|
| GroupId | GUID, a unique ID, represents the group and will be used in the policy. | |
| DescriptorIdList | List the device properties you want to use to cover in the group. For each device property, see Device Properties for more detail. All properties are case sensitive. | PrimaryId: RemovableMediaDevices, CdRomDevices, WpdDevicesBusId: For example, USB, SCSI
DeviceId HardwareId InstancePathId: InstancePathId is a string that uniquely identifies the device in the system, for example, FriendlyNameId SerialNumberId VID PID VID_PID 0751_55E0: match this exact VID/PID pair 55E0: match any media with PID=55E0 0751: match any media with VID=0751 |
| MatchType | When there are multiple device properties being used in the DescriptorIDList, MatchType defines the relationship. | MatchAll: Any attributes under the DescriptorIdList will be And relationship; for example, if administrator puts DeviceID and InstancePathID, for every connected USB, system will check to see whether the USB meets both values.MatchAny: The attributes under the DescriptorIdList will be Or relationship; for example, if administrator puts DeviceID and InstancePathID, for every connected USB, system will do the enforcement as long as the USB has either an identical DeviceID or InstanceID value. |
Access Control Policy
| Property Name | Description | Options |
|---|---|---|
| PolicyRuleId | GUID, a unique ID, represents the policy and will be used in the reporting and troubleshooting. | |
| IncludedIdList | The group(s) that the policy will be applied to. If multiple groups are added, the policy will be applied to any media in all those groups. | The Group ID/GUID must be used at this instance.The following example shows the usage of GroupID:
|
| ExcludedIDList | The group(s) that the policy will not be applied to. | The Group ID/GUID must be used at this instance. |
| Entry Id | One PolicyRule can have multiple entries; each entry with a unique GUID tells Device Control one restriction. | |
| Type | Defines the action for the removable storage groups in IncludedIDList.Enforcement: Allow or Deny
Audit: AuditAllowed or AuditDenied |
AllowDeny
AuditAllowed: Defines notification and event when access is allowed AuditDenied: Defines notification and event when access is denied; has to work together with Deny entry. When there are conflict types for the same media, the system will apply the first one in the policy. An example of a conflict type is Allow and Deny. |
| Sid | Local user Sid or user Sid group or the Sid of the AD object, defines whether to apply this policy over a specific user or user group; one entry can have a maximum of one Sid and an entry without any Sid means applying the policy over the machine. | |
| ComputerSid | Local computer Sid or computer Sid group or the Sid of the AD object, defines whether to apply this policy over a specific machine or machine group; one entry can have a maximum of one ComputerSid and an entry without any ComputerSid means applying the policy over the machine. If you want to apply an Entry to a specific user and specific machine, add both Sid and ComputerSid into the same Entry. | |
| Options | Defines whether to display notification or not | 0 or 4: When Type Allow or Deny is selected.0: nothing
4: disable AuditAllowed and AuditDenied for this Entry. Even if Block happens and the AuditDenied is setting configured, the system will not show notification. When Type AuditAllowed is selected: 0: nothing 1: nothing 2: send event 3: send event When Type AuditDenied is selected: 0: nothing 1: show notification 2: send event 3: show notification and send event |
| AccessMask | Defines the access. | 1-7:1: Read
2: Write 3: Read and Write 4: Execute 5: Read and Execute 6: Write and Execute 7: Read and Write and Execute |
Common Removable Storage Access Control scenarios
To help familiarize you with Microsoft Defender for Endpoint Removable Storage Access Control, we have put together some common scenarios for you to follow.
Scenario 1: Prevent Write and Execute access to all but allow specific approved USBs
- Create groups
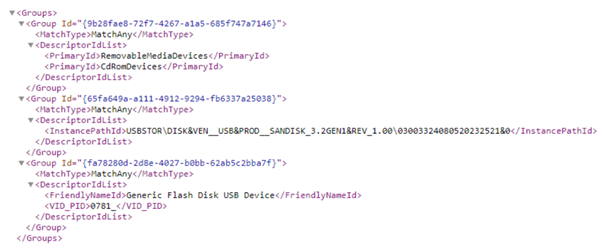
- Group 1: Any removable storage and CD/DVD. An example of a removable storage and CD/DVD is: Group 9b28fae8-72f7-4267-a1a5-685f747a7146 in the sample Any Removable Storage and CD-DVD Group.xml file.
- Group 2: Approved USBs based on device properties. An example for this use case is: Instance ID – Group 65fa649a-a111-4912-9294-fb6337a25038 in the sample Approved USBs Group.xml file.
Tip
Replace
&with&in the value. - Create policy
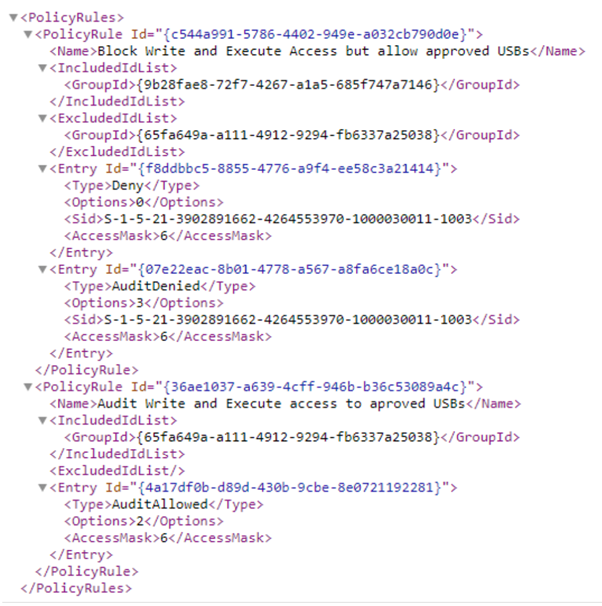
- Policy 1: Block Write and Execute Access but allow approved USBs. An example for this use case is: PolicyRule c544a991-5786-4402-949e-a032cb790d0e in the sample Scenario 1 Block Write and Execute Access but allow approved USBs.xml file.
- Policy 2: Audit Write and Execute access to allowed USBs. An example for this use case is: PolicyRule 36ae1037-a639-4cff-946b-b36c53089a4c in the sample Scenario 1 Audit Write and Execute access to approved USBs.xml file.
Scenario 2: Audit Write and Execute access to all but block specific unapproved USBs
- Create groups
- Group 1: Any removable storage and CD/DVD. An example for this use case is: Group 9b28fae8-72f7-4267-a1a5-685f747a7146 in the sample Any Removable Storage and CD-DVD Group.xml file.
- Group 2: Unapproved USBs based on device properties, for example, Vendor ID / Product ID, Friendly Name – Group 65fa649a-a111-4912-9294-fb6337a25038 in the sample Unapproved USBs Group.xml file.
Tip
Replace
&with&in the value. - Create policy
- Policy 1: Block Write and Execute access to all but block specific unapproved USBs. An example of this use case is: PolicyRule 23b8e437-66ac-4b32-b3d7-24044637fc98 in the sample Scenario 2 Audit Write and Execute access to all but block specific unapproved USBs.xml file.
- Policy 2: Audit Write and Execute access to others. An example of this use case is: PolicyRule b58ab853-9a6f-405c-a194-740e69422b48 in the sample Scenario 2 Audit Write and Execute access to others.xml file.
Deploying and managing policy via Group Policy
The Removable Storage Access Control feature enables you to apply policy via Group Policy to either user or device, or both.
Licensing
Before you get started with Removable Storage Access Control, you must confirm your Microsoft 365 subscription. To access and use Removable Storage Access Control, you must have Microsoft 365 E3 or Microsoft 365 E5.
Deploying policy via Group Policy
- Combine all groups within
<Groups></Groups>into one xml file.The following image illustrates the example of Scenario 1: Prevent Write and Execute access to all but allow specific approved USBs.
- Combine all rules within
<PolicyRules></PolicyRules>into one xml file.If you want to restrict a specific user, then use SID property into the Entry. If there is no SID in the policy Entry, the Entry will be applied to everyone login instance for the machine.
The following image illustrates the usage of SID property, and an example of Scenario 1: Prevent Write and Execute access to all but allow specific approved USBs.
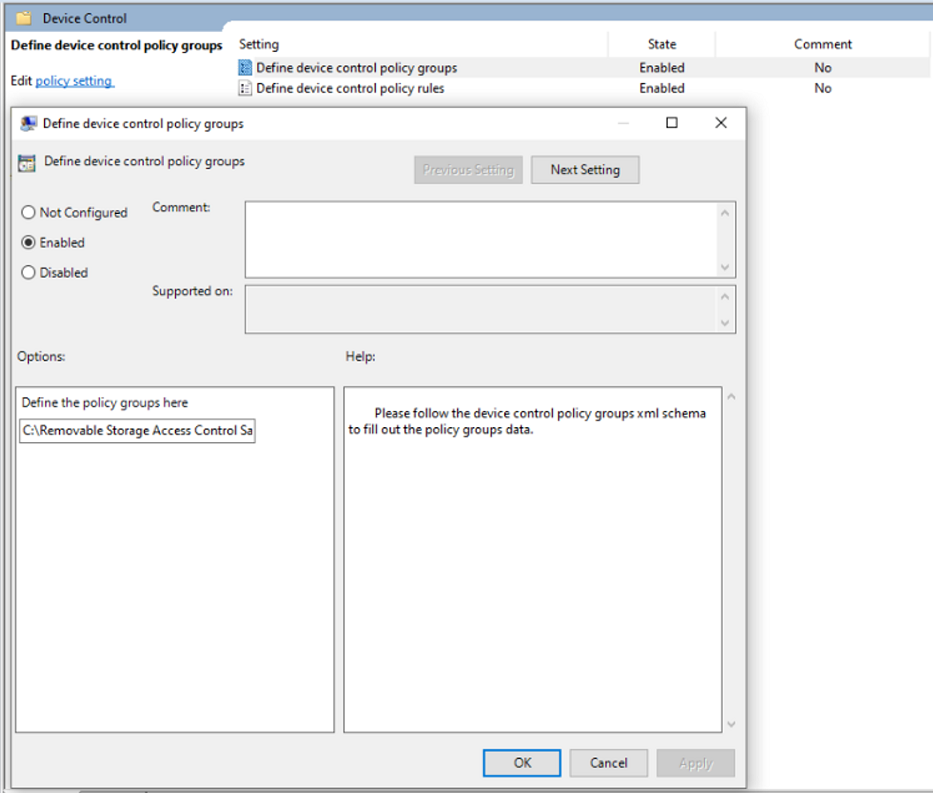
- Save both rule and group XML files on the network share folder and put the network share folder path into the Group Policy setting: Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Device Control: ‘Define device control policy groups’ and ‘Define device control policy rules’.
If you cannot find the policy configuration UX in the Group Policy, you can download the WindowsDefender.adml and WindowsDefender.admx files by selecting Raw and then Save as.
- The target machine must be able to access the network share to have the policy. However, once the policy is read, the network share connection is no longer required, even after machine reboot.
Deploying and managing policy via Intune OMA-URI
The Removable Storage Access Control feature enables you to apply policy via OMA-URI to either user or device, or both.
Licensing requirements
Before you get started with Removable Storage Access Control, you must confirm your Microsoft 365 subscription. To access and use Removable Storage Access Control, you must have Microsoft 365 E3 or Microsoft 365 E5.
Permission
For policy deployment in Intune, the account must have permissions to create, edit, update, or delete device configuration profiles. You can create custom roles or use any of the built-in roles with these permissions.
- Policy and profile Manager role
- Custom role with Create/Edit/Update/Read/Delete/View Reports permissions turned on for Device Configuration profiles
- Global administrator
Deploying policy via OMA-URI
Microsoft Endpoint Manager admin center (https://endpoint.microsoft.com/) > Devices > Configuration profiles > Create profile > Platform: Windows 10 and later & Profile: Custom
- For each Group, create an OMA-URI rule:
- OMA-URI:
./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7b**GroupGUID**%7d/GroupDataFor example, for any removable storage and CD/DVD group in the sample, the link must be:
./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7b9b28fae8-72f7-4267-a1a5-685f747a7146%7d/GroupData - Data Type: String (XML file)
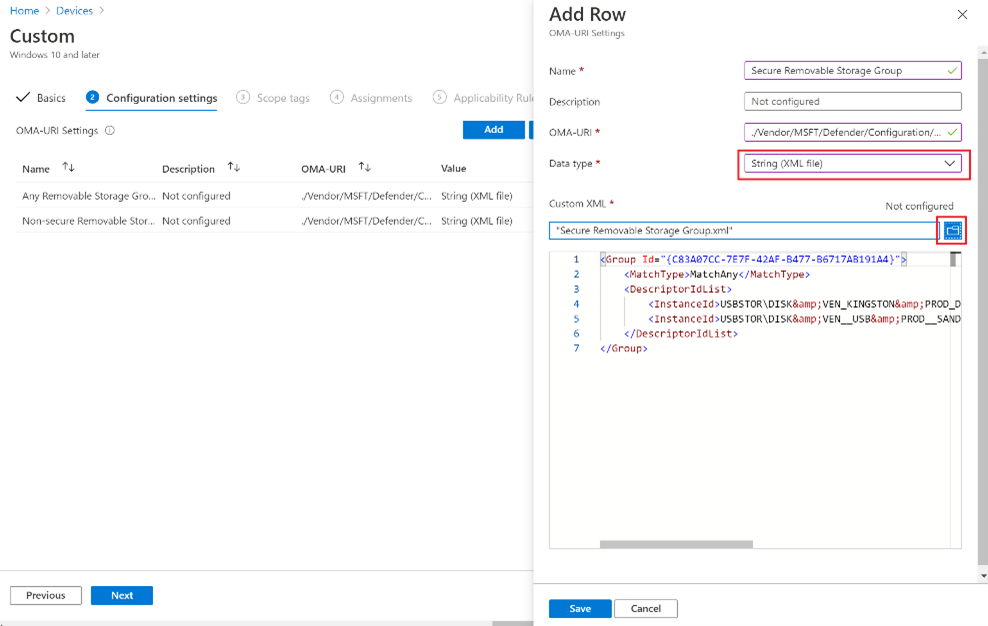
- OMA-URI:
- For each policy, also create an OMA-URI:
- OMA-URI:
./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7b**PolicyRuleGUID**%7d/RuleDataFor example, for the Block Write and Execute Access but allow approved USBs rule in the sample, the link must be:
./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7bc544a991-5786-4402-949e-a032cb790d0e%7d/RuleData - Data Type: String (XML file)
- OMA-URI:
Deploying and managing policy by using Intune user interface
This capability is available in the Microsoft Endpoint Manager admin center (https://endpoint.microsoft.com/). Go to Endpoint Security > Attack Surface Reduction > Create Policy. Choose Platform: Windows 10 and later with Profile: Device Control.
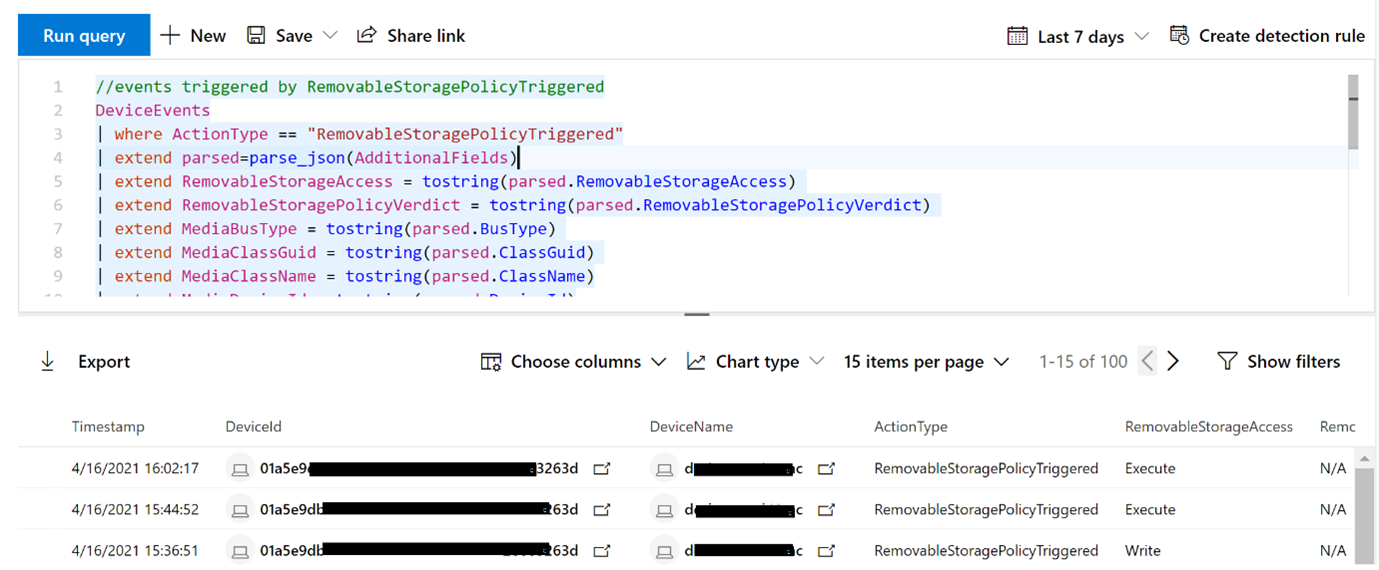
View Device Control Removable Storage Access Control data in Microsoft Defender for Endpoint
The Microsoft 365 Defender portal shows events triggered by the Device Control Removable Storage Access Control. To access the Microsoft 365 security, you must have the following subscription:
- Microsoft 365 for E5 reporting
//events triggered by RemovableStoragePolicyTriggered
DeviceEvents
| where ActionType == "RemovableStoragePolicyTriggered"
| extend parsed=parse_json(AdditionalFields)
| extend RemovableStorageAccess = tostring(parsed.RemovableStorageAccess)
| extend RemovableStoragePolicyVerdict = tostring(parsed.RemovableStoragePolicyVerdict)
| extend MediaBusType = tostring(parsed.BusType)
| extend MediaClassGuid = tostring(parsed.ClassGuid)
| extend MediaClassName = tostring(parsed.ClassName)
| extend MediaDeviceId = tostring(parsed.DeviceId)
| extend MediaInstanceId = tostring(parsed.DeviceInstanceId)
| extend MediaName = tostring(parsed.MediaName)
| extend RemovableStoragePolicy = tostring(parsed.RemovableStoragePolicy)
| extend MediaProductId = tostring(parsed.ProductId)
| extend MediaVendorId = tostring(parsed.VendorId)
| extend MediaSerialNumber = tostring(parsed.SerialNumber)
|project Timestamp, DeviceId, DeviceName, InitiatingProcessAccountName, ActionType, RemovableStorageAccess, RemovableStoragePolicyVerdict, MediaBusType, MediaClassGuid, MediaClassName, MediaDeviceId, MediaInstanceId, MediaName, RemovableStoragePolicy, MediaProductId, MediaVendorId, MediaSerialNumber
| order by Timestamp desc
Frequently asked questions
What is the removable storage media limitation for the maximum number of USBs?
We’ve validated one USB group with 100,000 media – up to 7 MB in size. The policy works in both Intune and GPO without performance issues.
Why does the policy not work?
The most common reason is there’s no required antimalware client version.
Another reason could be that the XML file isn’t correctly formatted, for example, not using the correct markdown formatting for the “&” character in the XML file, or the text editor might add a byte order mark (BOM) 0xEF 0xBB 0xBF at the beginning of the files, which causes the XML parsing not to work. One simple solution is to download the sample file (select Raw and then Save as) and then update.
If you are deploying and managing the policy via Group Policy, please make sure combine all PolicyRule into one XML file within a parent node called PolicyRules and all Group into one XML file within a parent node called Groups; if you manage through Intune, keep one PolicyRule one XML file, same thing, one Group one XML file.
There is no configuration UX for ‘Define device control policy groups’ and ‘Define device control policy rules’ on my Group Policy
We don’t backport the Group Policy configuration UX, but you can still get the related adml and admx files by clicking ‘Raw’ and ‘Save as’ at the WindowsDefender.adml and WindowsDefender.admx files.
How can I know which machine is using out of date antimalware client version in the organization?
You can use following query to get antimalware client version on the Microsoft 365 security portal:
//check the antimalware client version
DeviceFileEvents
|where FileName == "MsMpEng.exe"
|where FolderPath contains @"C:\ProgramData\Microsoft\Windows Defender\Platform\"
|extend PlatformVersion=tostring(split(FolderPath, "\\", 5))
//|project DeviceName, PlatformVersion // check which machine is using legacy platformVersion
|summarize dcount(DeviceName) by PlatformVersion // check how many machines are using which platformVersion
|order by PlatformVersion desc

