Details
- Your ESET product detects the threat Filecoder.WannaCryptor or a variant of this threat.
Solution
ESET detects and blocks this threat and its variants (such as WannaCryptor.D). ESET identifies this threat as Filecoder.WannaCryptor.
On systems not protected by ESET, a Windows exploit called EternalBlue can be used to introduce WannaCryptor. We strongly recommend that you follow the suggestions below to ensure the highest level of security on your computer:
- Make sure that ESET Live Grid is enabled in your ESET product.
- Make sure that your ESET software is upgraded to the latest version and running most up-to-date detection engine.
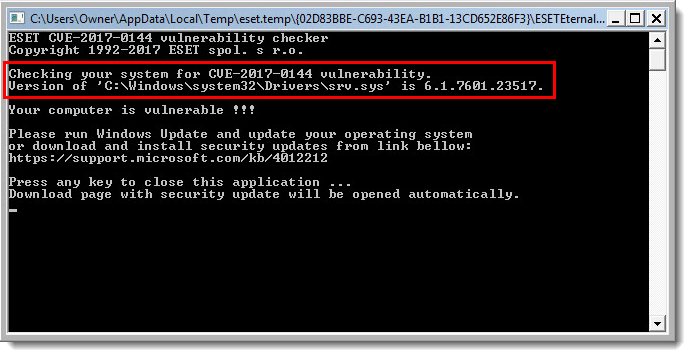
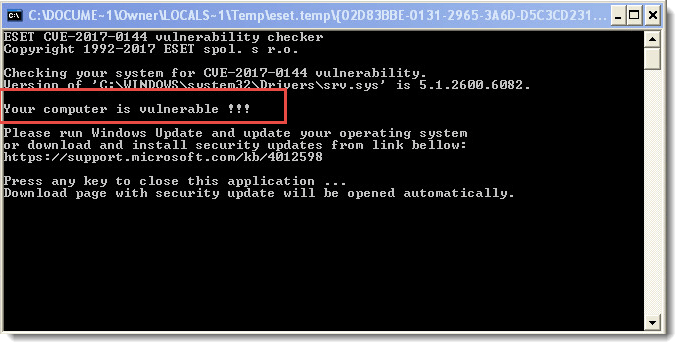
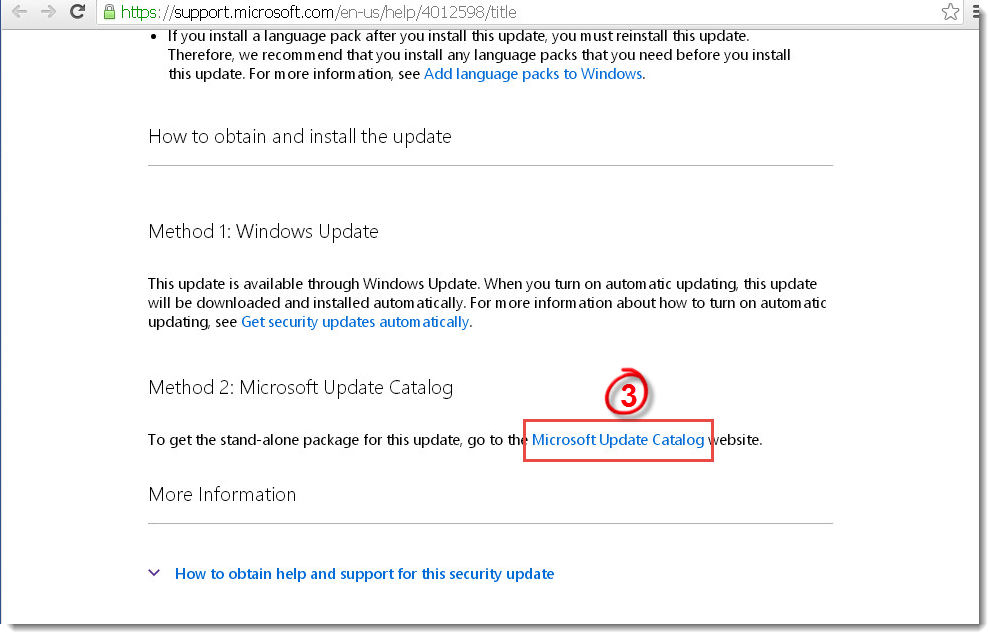
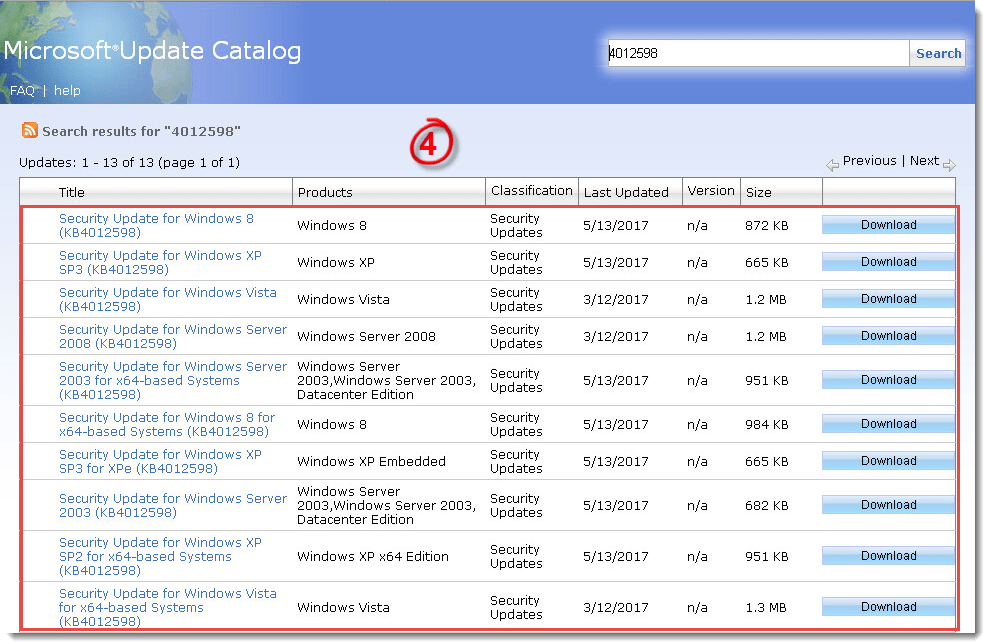
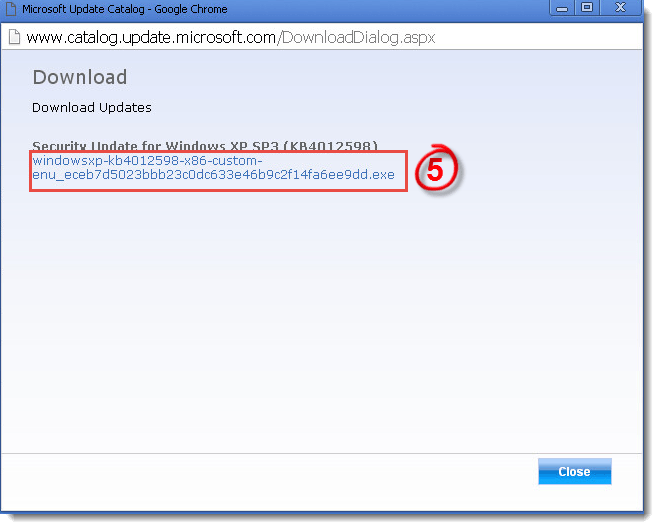
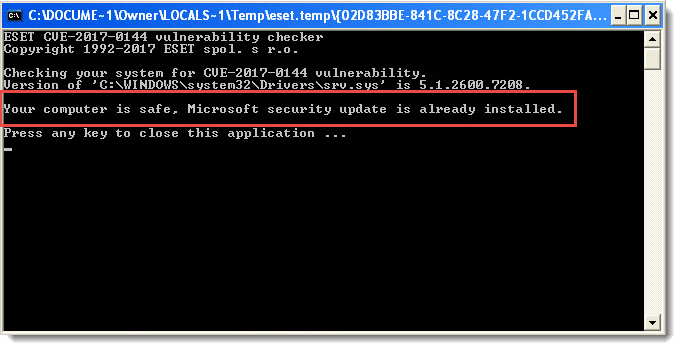
- Follow the steps in the section below to make sure your system is patched against the EternalBlue exploit.
- Warn colleagues who frequently receive emails from external sources – for instance financial departments or Human Resources.
- Regularly back up your data. In the event of infection, this will help you recover all data. Do not leave external storage used for backups connected to your computer to eliminate the risk of infecting your backups. If your system requires Windows Updates to receive the patch for this exploit, create new backups after applying the patch.
- Disable or restrict Remote Desktop Protocol (RDP) access (see Remote Desktop Protocol best practices against attacks).
- Disable macros in Microsoft Office.
- If you are using Windows XP, disable SMBv1.
For more detailed information about how you can use ESET to protect your systems from ransomware infections, see the following Knowledgebase article:
ESET Support Services
- ESET Customers worldwide—Contact your local ESET partner for support.
- Free ESET Cybersecurity Awareness Training.
- WeLiveSecurity (May 2020): WannaCryptor remains a global threat three years on
- WeLiveSecurity (May 2017): Huge ransomware outbreak disrupts IT systems worldwide, WannaCryptor to blame
- WeLiveSecurity (May 2017): Check-EternalBlue: Is your PC patched against the WannaCryptor worm vulnerability?
- ESET.com: How does ESET protect against WannaCryptor ransomware.
Editor by : BEST Antivirus KBS Team