Important
The improved Microsoft 365 Defender portal is now available. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 Defender portal. Learn what’s new.
Applies to:
- Microsoft 365 Defender
Want to experience Microsoft 365 Defender? You can evaluate it in a lab environment or run your pilot project in production.
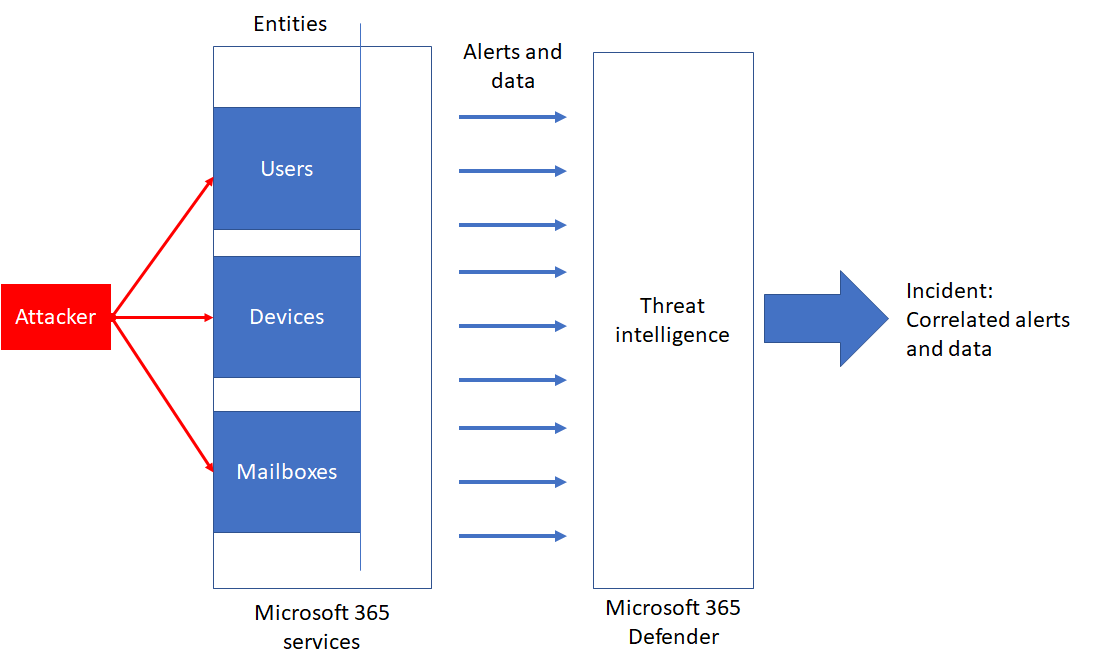
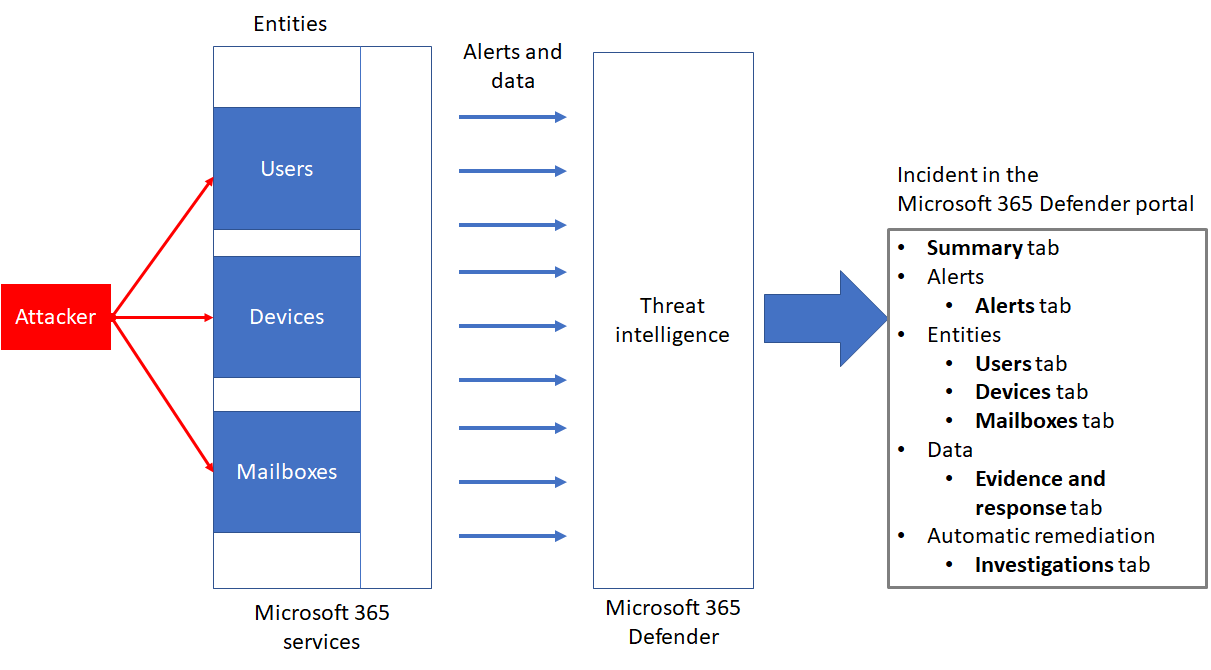
An incident in Microsoft 365 Defender is a collection of correlated alerts and associated data that make up the story of an attack.
Microsoft 365 services and apps create alerts when they detect a suspicious or malicious event or activity. Individual alerts provide valuable clues about a completed or ongoing attack. However, attacks typically employ various techniques against different types of entities, such as devices, users, and mailboxes. The result is multiple alerts for multiple entities in your tenant.
Because piecing the individual alerts together to gain insight into an attack can be challenging and time-consuming, Microsoft 365 Defender automatically aggregates the alerts and their associated information into an incident.
Watch this short overview of incidents in Microsoft 365 Defender (4 minutes).
Grouping related alerts into an incident gives you a comprehensive view of an attack. For example, you can see:
- Where the attack started.
- What tactics were used.
- How far the attack has gone into your tenant.
- The scope of the attack, such as how many devices, users, and mailboxes were impacted.
- All of the data associated with the attack.
If enabled, Microsoft 365 Defender can automatically investigate and resolve alerts through automation and artificial intelligence. You can also perform additional remediation steps to resolve the attack.
Incidents and alerts in the Microsoft 365 Defender portal
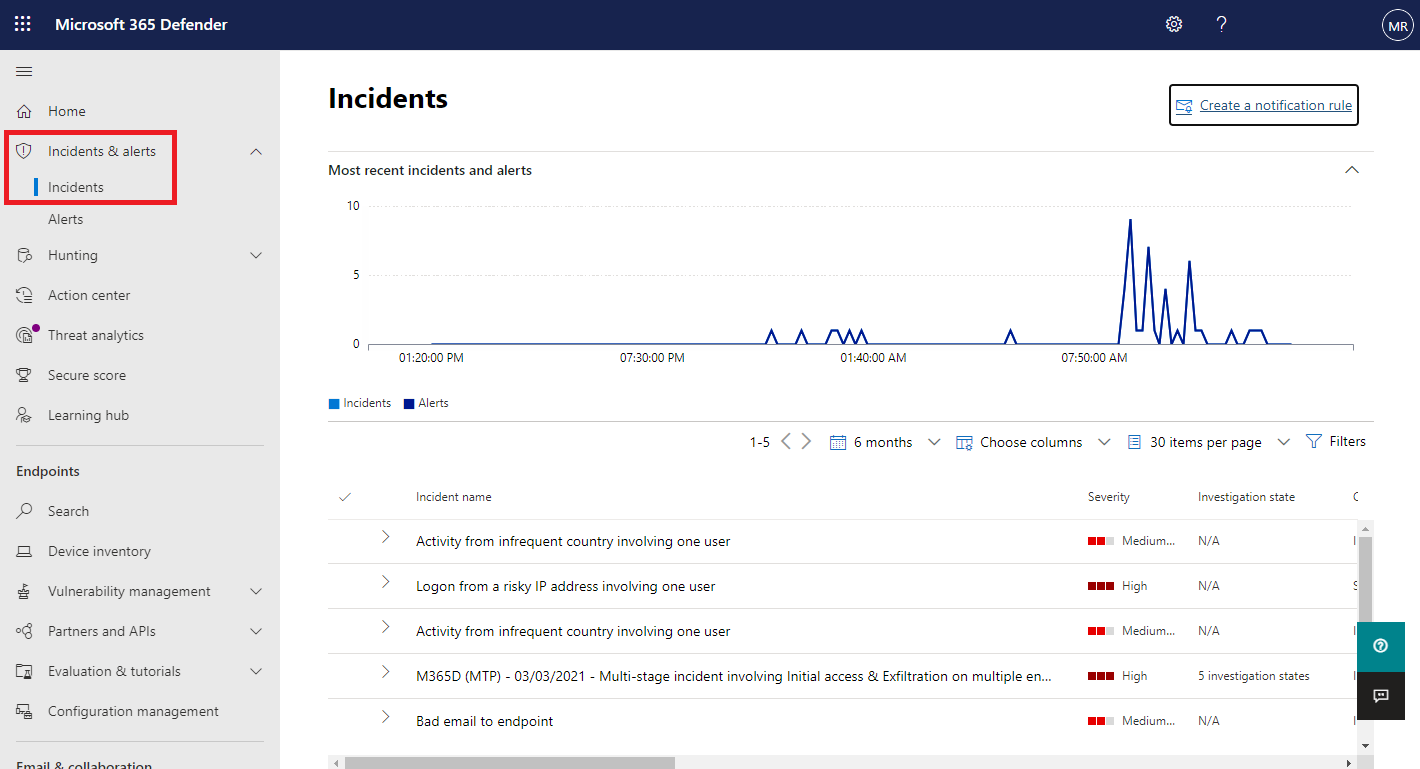
You manage incidents from Incidents & alerts > Incidents on the quick launch of the Microsoft 365 Defender portal. Here’s an example.
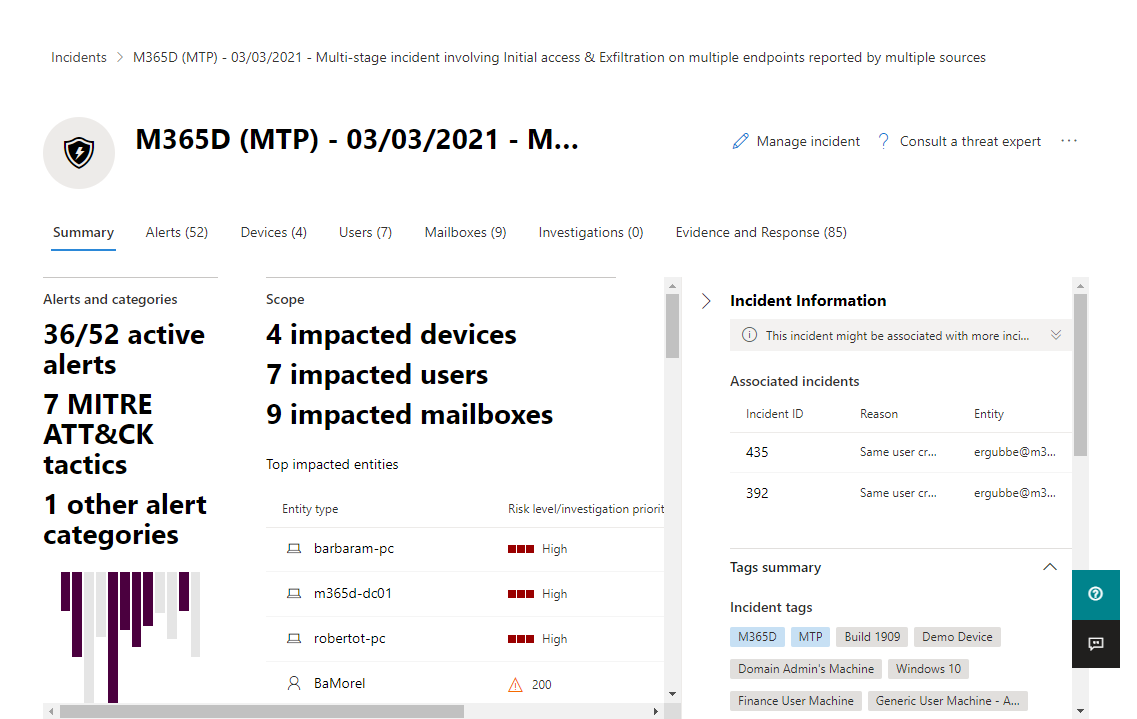
Selecting an incident name displays a summary of the incident and provides access to tabs with additional information.
The additional tabs for an incident are:
- Alerts
All the alerts related to the incident and their information.
- Devices
All the devices that have been identified to be part of or related to the incident.
- Users
All the users that have been identified to be part of or related to the incident.
- Mailboxes
All the mailboxes that have been identified to be part of or related to the incident.
- Investigations
All the automated investigations triggered by alerts in the incident.
- Evidence and Response
All the supported events and suspicious entities in the alerts in the incident.
- Graph (Preview)
A visual representation of the attack that connects the different suspicious entities that are part of the attack with their related assets such as users, devices, and mailboxes.
Here’s the relationship between an incident and its data and the tabs of an incident in the Microsoft 365 Defender portal.
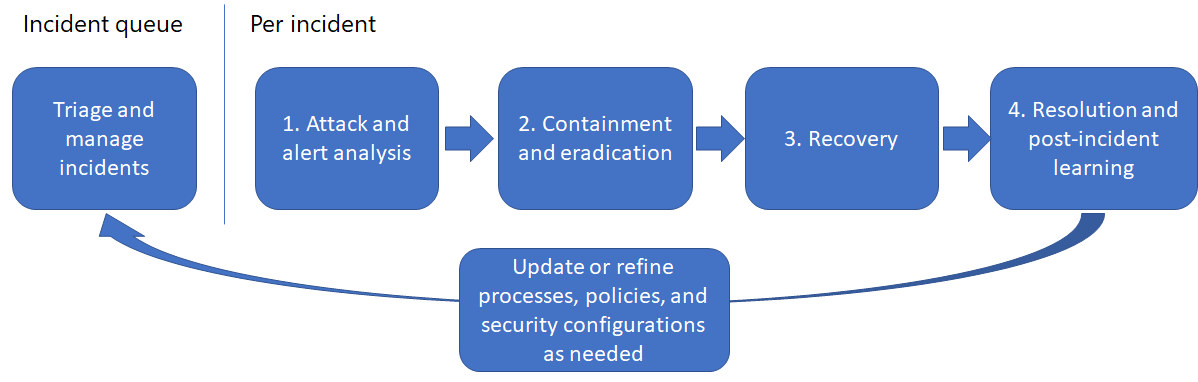
Example incident response workflow for Microsoft 365 Defender
Here’s an example workflow for responding to incidents in Microsoft 365 with the Microsoft 365 Defender portal.
On an ongoing basis, identify the highest priority incidents for analysis and resolution in the incident queue and get them ready for response. This is a combination of:
- Triaging to determining the highest priority incidents through filtering and sorting of the incident queue.
- Managing incidents by modifying their title, assigning them to an analyst, and adding tags and comments.
- For each incident, begin an attack and alert investigation and analysis:
- View the summary of the incident to understand it’s scope and severity and what entities are affected with the Summary and Graph (Preview) tabs.
- Begin analyzing the alerts to understand their origin, scope, and severity with the Alerts tab.
- As needed, gather information on impacted devices, users, and mailboxes with the Devices, Users, and Mailboxes tabs.
- See how Microsoft 365 Defender has automatically resolved some alerts with the Investigations tab.
- As needed, use information in the data set for the incident for more information with the Evidence and Response tab.
- After or during your analysis, perform containment to reduce any additional impact of the attack and eradication of the security threat.
- As much as possible, recover from the attack by restoring your tenant resources to the state they were in before the incident.
- Resolve the incident and take time for post-incident learning to:
- Understand the type of the attack and its impact.
- Research the attack in Threat Analytics and the security community for a security attack trend.
- Recall the workflow you used to resolve the incident and update your standard workflows, processes, policies, and playbooks as needed.
- Determine whether changes in your security configuration are needed and implement them.
If you are new to security analysis, see the introduction to responding to your first incident for additional information and to step through an example incident.
For more information about incident response across Microsoft products, see this article.
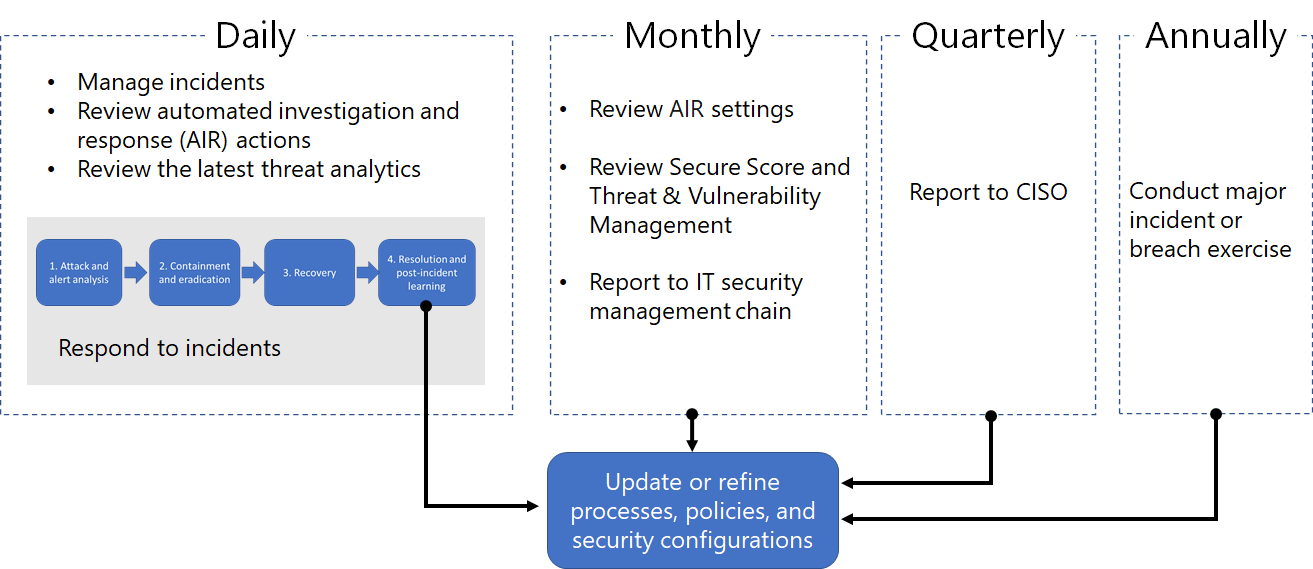
Example security operations for Microsoft 365 Defender
Here’s an example of security operations (SecOps) for Microsoft 365 Defender.
Daily tasks can include:
- Managing incidents
- Reviewing automated investigation and response (AIR) actions in the Action center
- Reviewing the latest Threat Analytics
- Responding to incidents
Monthly tasks can include:
- Reviewing AIR settings
- Reviewing Secure Score and Threat & Vulnerability Management
- Reporting to your IT security management chain
Quarterly tasks can include a report and briefing of security results to the Chief Information Security Officer (CISO).
Annual tasks can include conducting a major incident or breach exercise to test your staff, systems, and processes.
Daily, monthly, quarterly, and annual tasks can be used to update or refine processes, policies, and security configurations.
See Integrating Microsoft 365 Defender into your security operations for more details.
SecOps resources across Microsoft products
For more information about SecOps across Microsoft’s products, see these resources:
Get incident notifications by email
You can set up Microsoft 365 Defender to notify your staff with an email about new incidents or updates to existing incidents. You can choose to get notifications based on:
- Incident severity.
- Device group.
- Only on the first update per incident.
The email notification contains important details about the incident like the incident name, severity, and categories, among others. You can also go directly to the incident and start your analysis right away. For more information, see Investigate incidents.
You can add or remove recipients in the email notifications. New recipients get notified about incidents after they’re added.
Note
You need the ‘Manage security settings’ permission to configure email notification settings. If you’ve chosen to use basic permissions management, users with Security Administrator or Global Administrator roles can configure email notifications for you.
Likewise, if your organization is using role-based access control (RBAC), you can only create, edit, delete, and receive notifications based on device groups that you are allowed to manage.
Create a rule for email notifications
Follow these steps to create a new rule and customize email notification settings.
- In the navigation pane, select Settings > Microsoft 365 Defender > Incident email notifications.
- Select Add item.
- On the Basics page, type the rule name and a description, and then select Next.
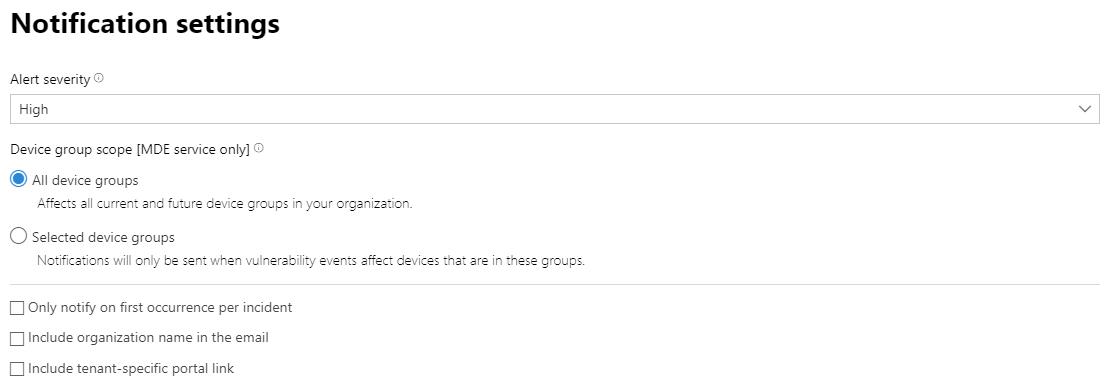
- On the Notification settings page, configure:
- Alert severity – Choose the alert severities that will trigger an incident notification. For example, if you only want to be informed about high-severity incidents, select High.
- Device group scope – You can specify all device groups or select from the list of device groups in your tenant.
- Only notify on first occurrence per incident – Select if you want a notification only on the first alert that matches your other selections. Later updates or alerts related to the incident won’t send additional notifications.
- Include organization name in the email – Select if you want your organization name to appear in the email notification.
- Include tenant-specific portal link – Select if you want to add a link with the tenant ID in the email notification for access to a specific Microsoft 365 tenant.
- Select Next. On the Recipients page, add the email addresses that will receive the incident notifications. Select Add after typing each new email address. To test notifications and ensure that the recipients receive them in the inboxes, select Send test email.
- Select Next. On the Review rule page, review the settings of the rule, and then select Create rule. Recipients will start receiving incident notifications through email based on the settings.
To edit an existing rule, select it from the list of rules. On the pane with the rule name, select Edit rule and make your changes on the Basics, Notification settings, and Recipients pages.
To delete a rule, select it from the list of rules. On the pane with the rule name, select Delete.
Training for security analysts
Use this learning module from Microsoft Learn to understand how to use Microsoft 365 Defender to manage incidents and alerts.
| Training: | Investigate incidents with Microsoft 365 Defender |
|---|---|
 |
Microsoft 365 Defender unifies threat data from multiple services and uses AI to combine them into incidents and alerts. Learn how to minimize the time between an incident and its management for subsequent response and resolution.27 min – 6 Units |
Next steps
Use the listed steps based on your experience level or role on your security team.
Experience level
Follow this table for your level of experience with security analysis and incident response.
| Level | Steps |
|---|---|
| New |
|
| Experienced |
|
Security team role
Follow this table based on your security team role.
| Role | Steps |
|---|---|
| Incident responder (Tier 1) | Get started with the incident queue from the Incidents page of the Microsoft 365 Defender portal. From here you can:
|
| Security investigator or analyst (Tier 2) |
|
| Advanced security analyst or threat hunter (Tier 3) |
|
| SOC manager | See how to integrate Microsoft 365 Defender into your Security Operations Center (SOC). |