Note
We’ve renamed Microsoft Cloud App Security. It’s now called Microsoft Defender for Cloud Apps. In the coming weeks, we’ll update the screenshots and instructions here and in related pages. For more information about the change, see this announcement. To learn more about the recent renaming of Microsoft security services, see the Microsoft Ignite Security blog.
The Microsoft Defender for Cloud Apps integration with Microsoft Defender for Endpoint provides a seamless Shadow IT visibility and control solution. Our integration enables Defender for Cloud Apps administrators to block access of end users to cloud apps, by natively integrating Defender for Cloud Apps app governance controls with Microsoft Defender for Endpoint’s network protection. Alternatively, administrators can take a gentler approach of warning users when they access risky cloud apps.
Prerequisites
- Microsoft Defender for Cloud Apps license
- Microsoft Defender for Endpoint license
- Windows 10 version 1709 (OS Build 16299.1085 with KB4493441), Windows 10 version 1803 (OS Build 17134.704 with KB4493464), Windows 10 version 1809 (OS Build 17763.379 with KB4489899) or later Windows 10 and Windows 11 versions
- Microsoft Defender Antivirus
Block access to unsanctioned cloud apps
Defender for Cloud Apps uses the built-in Unsanctioned app tag to mark cloud apps as prohibited for use, available in both the Cloud Discovery and Cloud app catalog pages. By enabling the integration with Defender for Endpoint, you can seamlessly block access to unsanctioned apps with a single click in the Defender for Cloud Apps portal.
How blocking works
Apps marked as Unsanctioned in Defender for Cloud Apps are automatically synced to Defender for Endpoint, usually within a few minutes. More specifically, the domains used by these unsanctioned apps are propagated to endpoint devices to be blocked by Microsoft Defender Antivirus within the Network Protection SLA.
How to enable cloud app blocking with Defender for Endpoint
Use the following steps to enable access control for cloud apps:
- In Defender for Cloud Apps, under the settings cog, select Settings, under Cloud Discovery select Microsoft Defender for Endpoint, and then select Block unsanctioned apps.
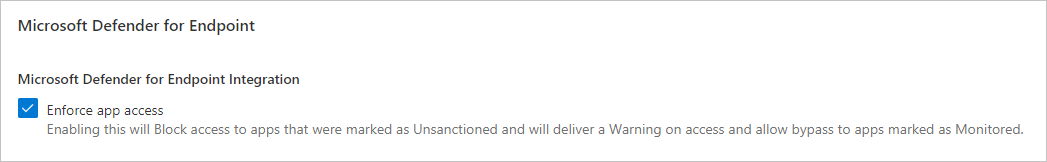
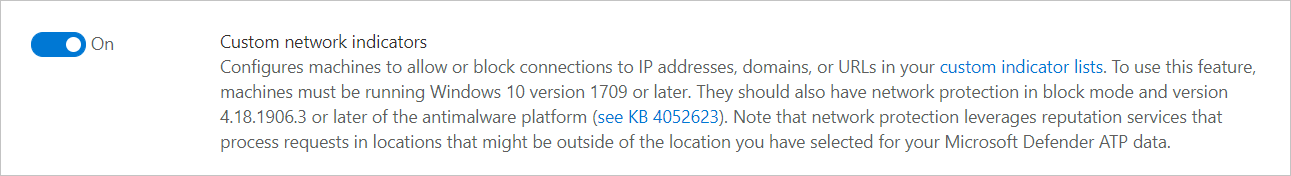
- In Microsoft 365 Defender, go to Settings > Endpoints > Advanced features, and then select Custom network indicators. For information about network indicators, see Create indicators for IPs and URLs/domains.
This allows you to leverage Microsoft Defender Antivirus network protection capabilities to block access to a predefined set of URLs using Defender for Cloud Apps, either by manually assigning app tags to specific apps or automatically using an app discovery policy.
Educate users when accessing risky apps
Note
Prerequisite: Opt in to the public preview feature in Microsoft Defender for Endpoint. For more information, see Microsoft Defender for Endpoint preview features.
Admins have the option to warn users when they access risky apps. Rather than blocking users, they are prompted with a message providing a custom redirect link to a company page listing apps approved for use. The prompt provides options for users to bypass the warning and continue to the app. Admins are also able to monitor the number of users that bypass the warning message.
How does it work
Defender for Cloud Apps uses the built-in Monitored app tag to mark cloud apps as risky for use. The tag is available on both the Cloud Discovery and Cloud App Catalog pages. By enabling the integration with Defender for Endpoint, you can seamlessly warn users on access to monitored apps with a single click in the Defender for Cloud Apps portal.
Apps marked as Monitored are automatically synced to Defender for Endpoint’s custom URL indicators, usually within a few minutes. More specifically, the domains used by monitored apps are propagated to endpoint devices to provide a warning message by Microsoft Defender Antivirus within the Network Protection SLA.
Setting up the custom redirect URL for the warn message
Use the following steps to configure a custom URL pointing to a company web page where you can educate employees on why they have been warned and provide a list of alternative approved apps that adhere to your organization’s risk acceptance or are already managed by the organization.
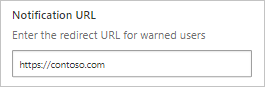
- In Defender for Cloud Apps, under the settings cog, select Settings, and under Cloud Discovery select Microsoft Defender for Endpoint.
- In the Notification URL box, enter your URL.
Setting up user bypass duration
Since users can bypass the warning message, you can use the following steps to configure the duration of the bypass apply. Once the duration has elapsed, users are prompted with the warning message the next time they access the monitored app.
- In Defender for Cloud Apps, under the settings cog, select Settings, and under Cloud Discovery select Microsoft Defender for Endpoint.
- In the Bypass duration box, enter the duration (hours) of the user bypass.
Monitor applied app controls
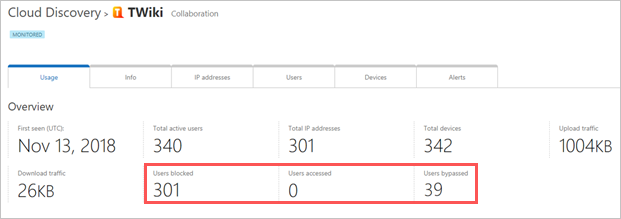
Once controls are applied, you can monitor app usage patterns by the applied controls (access, block, bypass) using the following steps.
- In Defender for Cloud Apps, under Discovery > Discovered apps, use the filters to find the relevant monitored app.
- Select the app’s name to view applied app controls on the app’s overview page.