With properly configured devices, you can boost overall resilience against threats and enhance your capability to detect and respond to attacks. Security configuration management helps ensure that your devices:
- Onboard to Microsoft Defender for Endpoint
- Meet or exceed the Defender for Endpoint security baseline configuration
- Have strategic attack surface mitigations in place
Click Configuration management from the navigation menu to open the Device configuration management page.
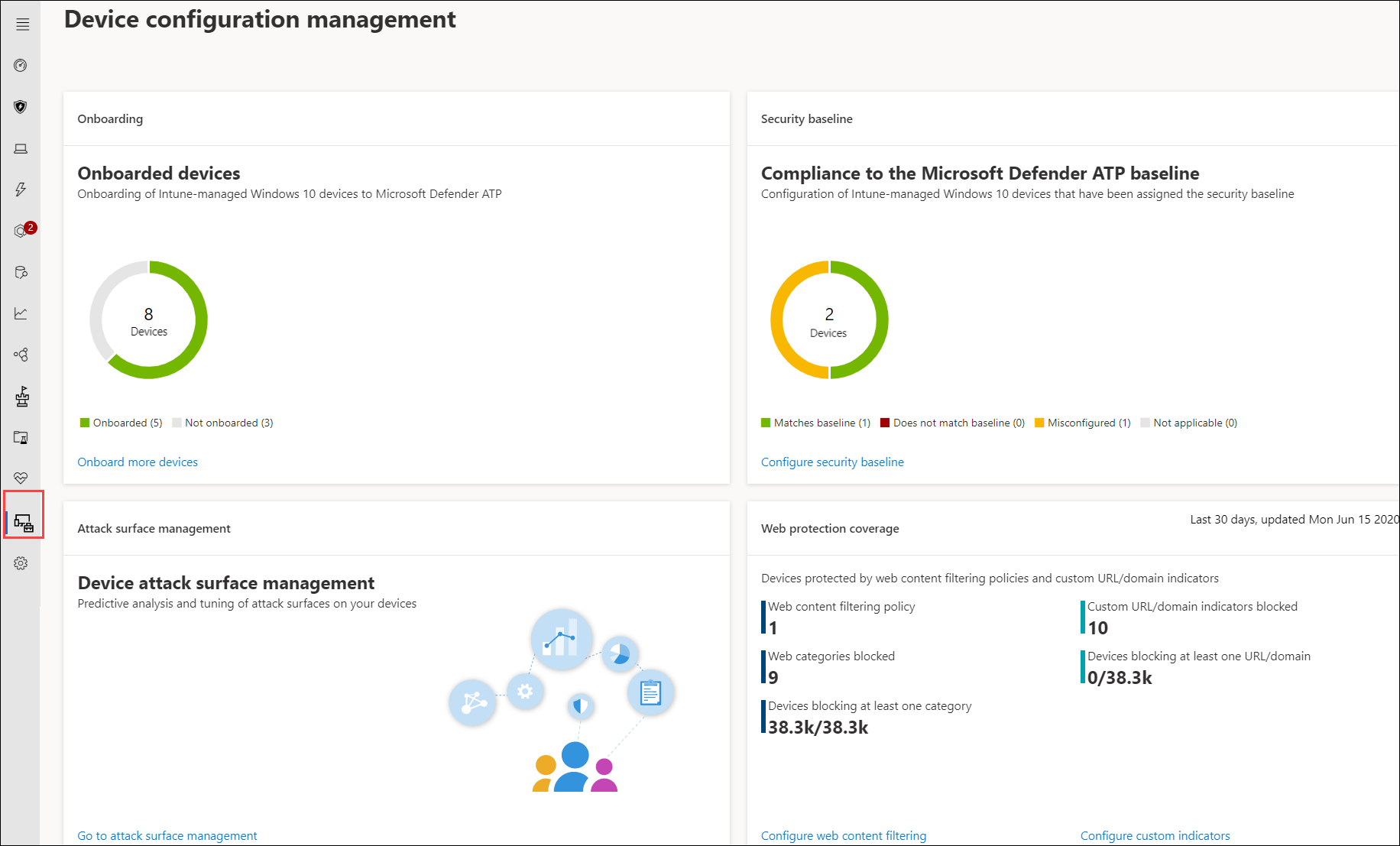
Device configuration management page
You can track configuration status at an organizational level and quickly take action in response to poor onboarding coverage, compliance issues, and poorly optimized attack surface mitigations through direct, deep links to device management pages on Microsoft Intune and Microsoft 365 Defender portal.
In doing so, you benefit from:
- Comprehensive visibility of the events on your devices
- Robust threat intelligence and powerful device learning technologies for processing raw events and identifying the breach activity and threat indicators
- A full stack of security features configured to efficiently stop the installation of malicious implants, hijacking of system files and process, data exfiltration, and other threat activities
- Optimized attack surface mitigations, maximizing strategic defenses against threat activity while minimizing impact to productivity
Enroll devices to Intune management
Device configuration management works closely with Intune device management to establish the inventory of the devices in your organization and the baseline security configuration. You will be able to track and manage configuration issues on Intune-managed Windows devices.
Before you can ensure your devices are configured properly, enroll them to Intune management. Intune enrollment is robust and has several enrollment options for Windows devices. For more information about Intune enrollment options, read about setting up enrollment for Windows devices.
Note
To enroll Windows devices to Intune, administrators must have already been assigned licenses. Read about assigning licenses for device enrollment.
Tip
To optimize device management through Intune, connect Intune to Defender for Endpoint.
Obtain required permissions
By default, only users who have been assigned the Global Administrator or the Intune Service Administrator role on Azure AD can manage and assign the device configuration profiles needed for onboarding devices and deploying the security baseline.
If you have been assigned other roles, ensure you have the necessary permissions:
- Full permissions to device configurations
- Full permissions to security baselines
- Read permissions to device compliance policies
- Read permissions to the organization
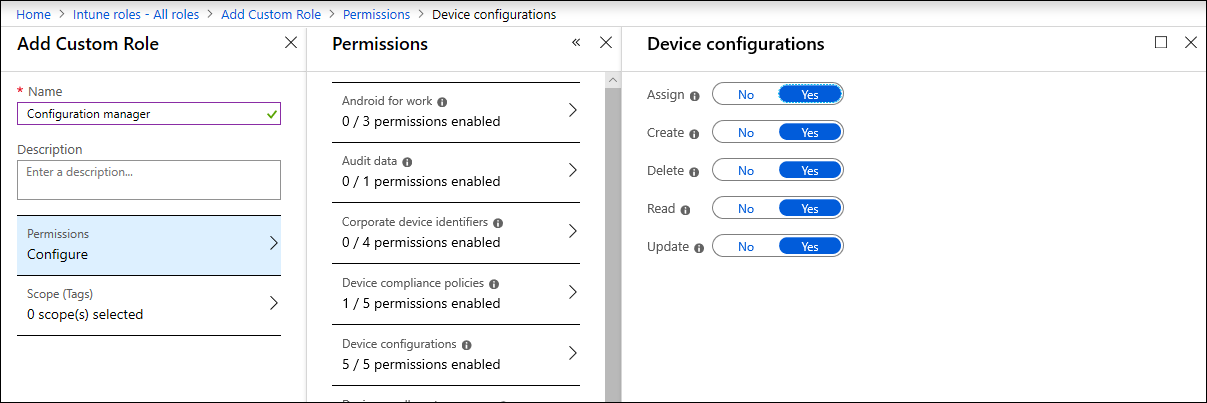
Device configuration permissions on Intune
Tip
To learn more about assigning permissions on Intune, read about creating custom roles.
In this section
| Topic | Description |
|---|---|
| Get devices onboarded to Defender for Endpoint | Track onboarding status of Intune-managed devices and onboard more devices through Intune. |
| Increase compliance to the Defender for Endpoint security baseline | Track baseline compliance and noncompliance. Deploy the security baseline to more Intune-managed devices. |
| Optimize ASR rule deployment and detections | Review rule deployment and tweak detections using impact analysis tools in Microsoft 365 Defender portal. |
Want to experience Defender for Endpoint? Sign up for a free trial.

