Deploying Microsoft Defender for Endpoint can be done using a ring-based deployment approach.
The deployment rings can be applied in the following scenarios:
New deployments
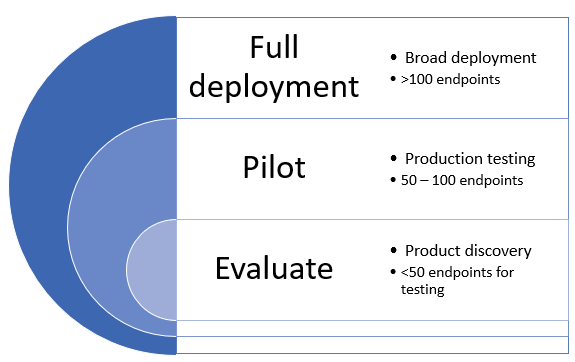
A ring-based approach is a method of identifying a set of endpoints to onboard and verifying that certain criteria is met before proceeding to deploy the service to a larger set of devices. You can define the exit criteria for each ring and ensure that they are satisfied before moving on to the next ring.
Adopting a ring-based deployment helps reduce potential issues that could arise while rolling out the service. By piloting a certain number of devices first, you can identify potential issues and mitigate potential risks that might arise.
Table 1 provides an example of the deployment rings you might use.
Table 1:
| Deployment ring | Description |
|---|---|
| Evaluate | Ring 1: Identify 50 systems for pilot testing |
| Pilot | Ring 2: Identify the next 50-100 endpoints in production environment |
| Full deployment | Ring 3: Roll out service to the rest of environment in larger increments |
Exit criteria
An example set of exit criteria for these rings can include:
- Devices show up in the device inventory list
- Alerts appear in dashboard
- Run a detection test
- Run a simulated attack on a device
Evaluate
Identify a small number of test machines in your environment to onboard to the service. Ideally, these machines would be fewer than 50 endpoints.
Pilot
Microsoft Defender for Endpoint supports a variety of endpoints that you can onboard to the service. In this ring, identify several devices to onboard and based on the exit criteria you define, decide to proceed to the next deployment ring.
The following table shows the supported endpoints and the corresponding tool you can use to onboard devices to the service.
| Endpoint | Deployment tool |
|---|---|
| Windows | Local script (up to 10 devices) NOTE: If you want to deploy more than 10 devices in a production environment, use the Group Policy method instead or the other supported tools listed below. Group Policy Microsoft Endpoint Manager/ Mobile Device Manager Microsoft Endpoint Configuration Manager VDI scripts Integration with Microsoft Defender for Cloud |
| macOS | Local script Microsoft Endpoint Manager JAMF Pro Mobile Device Management |
| Linux Server | Local script Puppet Ansible |
| iOS | Microsoft Endpoint Manager |
| Android | Microsoft Endpoint Manager |
Full deployment
At this stage, you can use the Plan deployment material to help you plan your deployment.
Use the following material to select the appropriate Microsoft Defender for Endpoint architecture that best suites your organization.
| Item | Description |
|---|---|
 PDF | Visio |
The architectural material helps you plan your deployment for the following architectures:
|
Existing deployments
Windows endpoints
For Windows and/or Windows Servers, you select several machines to test ahead of time (before patch Tuesday) by using the Security Update Validation program (SUVP).
For more information, see:
- What is the Security Update Validation Program
- Software Update Validation Program and Microsoft Malware Protection Center Establishment – TwC Interactive Timeline Part 4
Non-Windows endpoints
With macOS and Linux, you could take a couple of systems and run in the Beta channel.
Note
Ideally at least one security admin and one developer so that you are able to find compatibility, performance and reliability issues before the build makes it into the Current channel.
The choice of the channel determines the type and frequency of updates that are offered to your device. Devices in Beta are the first ones to receive updates and new features, followed later by Preview and lastly by Current.
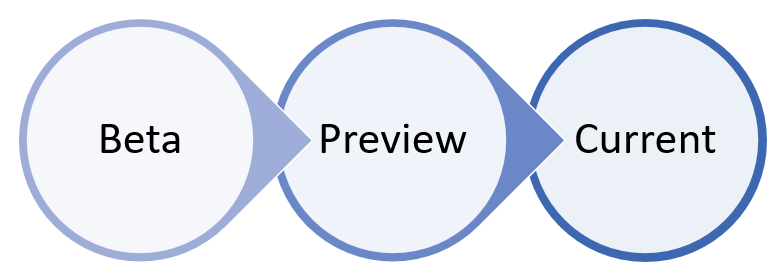
In order to preview new features and provide early feedback, it is recommended that you configure some devices in your enterprise to use either Beta or Preview.
Warning
Switching the channel after the initial installation requires the product to be reinstalled. To switch the product channel: uninstall the existing package, re-configure your device to use the new channel, and follow the steps in this document to install the package from the new location.

