Note
The Microsoft Defender for Identity sensor automatically reads events locally, without the need to configure event forwarding.
To enhance detection capabilities, Defender for Identity needs the Windows events listed in Configure event collection. These can either be read automatically by the Defender for Identity sensor or in case the Defender for Identity sensor is not deployed, it can be forwarded to the Defender for Identity standalone sensor in one of two ways, by configuring the Defender for Identity standalone sensor to listen for SIEM events or by configuring Windows Event Forwarding.
Note
- Defender for Identity standalone sensors do not support the collection of Event Tracing for Windows (ETW) log entries that provide the data for multiple detections. For full coverage of your environment, we recommend deploying the Defender for Identity sensor.
- Check that the domain controller is properly configured to capture the required events.
WEF configuration for Defender for Identity standalone sensor’s with port mirroring
After you configured port mirroring from the domain controllers to the Defender for Identity standalone sensor, follow the following instructions to configure Windows Event forwarding using Source Initiated configuration. This is one way to configure Windows Event forwarding.
Step 1: Add the network service account to the domain Event Log Readers Group.
In this scenario, assume that the Defender for Identity standalone sensor is a member of the domain.
- Open Active Directory Users and Computers, navigate to the BuiltIn folder and double-click Event Log Readers.
- Select Members.
- If Network Service is not listed, click Add, type Network Service in the Enter the object names to select field. Then click Check Names and click OK twice.
After adding the Network Service to the Event Log Readers group, reboot the domain controllers for the change to take effect.
Step 2: Create a policy on the domain controllers to set the Configure target Subscription Manager setting.
Note
You can create a group policy for these settings and apply the group policy to each domain controller monitored by the Defender for Identity standalone sensor. The following steps modify the local policy of the domain controller.
- Run the following command on each domain controller: winrm quickconfig
- From a command prompt type gpedit.msc.
- Expand Computer Configuration > Administrative Templates > Windows Components > Event Forwarding
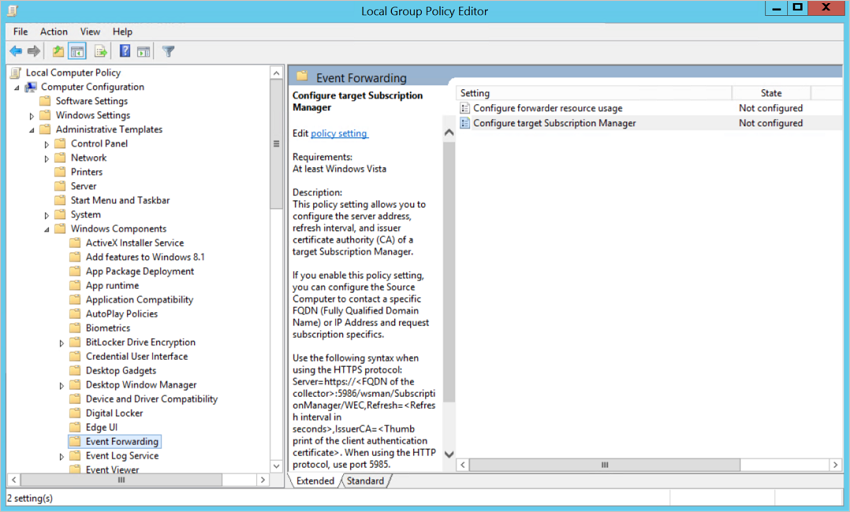
- Double-click Configure target Subscription Manager.
- Select Enabled.
- Under Options, click Show.
- Under SubscriptionManagers, enter the following value and click OK:
Server=http://<fqdnMicrosoftDefenderForIdentitySensor>:5985/wsman/SubscriptionManager/WEC,Refresh=10(For example:Server=http://atpsensor9.contoso.com:5985/wsman/SubscriptionManager/WEC,Refresh=10)

- Click OK.
- From an elevated command prompt type gpupdate /force.
Step 3: Perform the following steps on the Defender for Identity standalone sensor
- Open an elevated command prompt and type
wecutil qc. Leave the command window open. - Open Event Viewer.
- Right-click Subscriptions and select Create Subscription.
- Enter a name and description for the subscription.
- For Destination Log, confirm that Forwarded Events is selected. For Defender for Identity to read the events, the destination log must be Forwarded Events.
- Select Source computer initiated and click Select Computers Groups.
- Click Add Domain Computer.
- Enter the name of the domain controller in the Enter the object name to select field. Then click Check Names and click OK.
- Click OK.

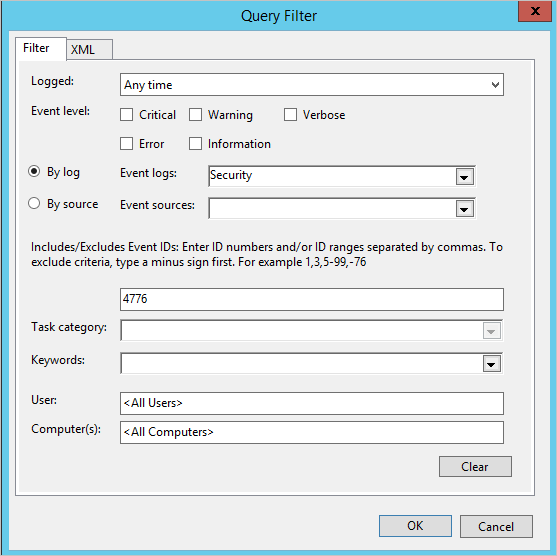
- Click Select Events.
- Click By log and select Security.
- In the Includes/Excludes Event ID field type the event number and click OK. For example, type 4776, like in the following sample:
- Return to the command window opened in the first step. Run the following commands, replacing SubscriptionName with the name you created for the subscription.
cmd
wecutil ss "SubscriptionName" /cm:"Custom" wecutil ss "SubscriptionName" /HeartbeatInterval:5000 - Return to the Event Viewer console. Right-click the created subscription and select Runtime Status to see if there are any issues with the status.
- After a few minutes, check to see that the events you set to be forwarded is showing up in the Forwarded Events on the Defender for Identity standalone sensor.
For more information, see: Configure the computers to forward and collect events

