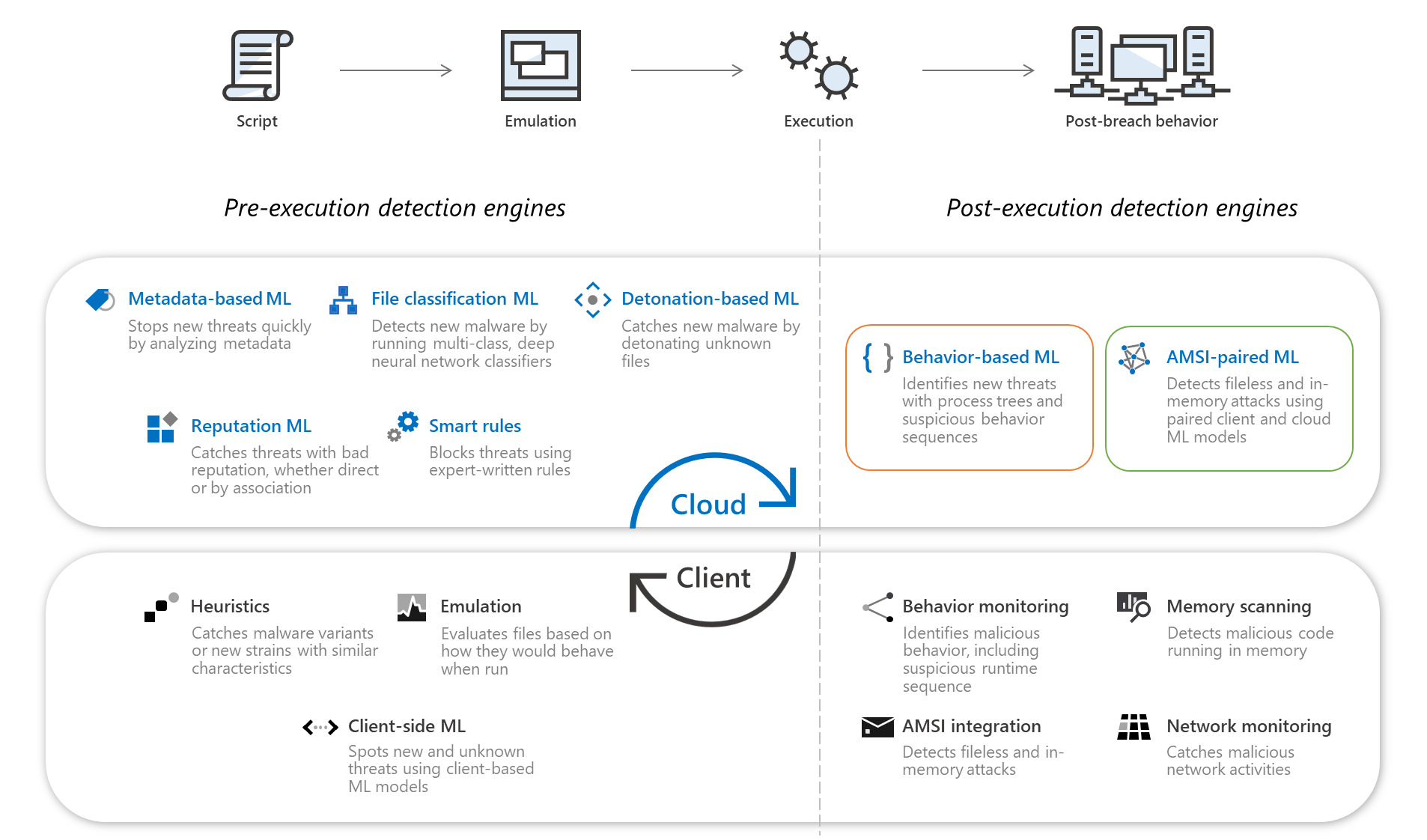
Overview
Client behavioral blocking is a component of behavioral blocking and containment capabilities in Defender for Endpoint. As suspicious behaviors are detected on devices (also referred to as clients or endpoints), artifacts (such as files or applications) are blocked, checked, and remediated automatically.
Antivirus protection works best when paired with cloud protection.
How client behavioral blocking works
Microsoft Defender Antivirus can detect suspicious behavior, malicious code, fileless and in-memory attacks, and more on a device. When suspicious behaviors are detected, Microsoft Defender Antivirus monitors and sends those suspicious behaviors and their process trees to the cloud protection service. Machine learning differentiates between malicious applications and good behaviors within milliseconds, and classifies each artifact. In almost real time, as soon as an artifact is found to be malicious, it’s blocked on the device.
Whenever a suspicious behavior is detected, an alert is generated, and is visible in the Microsoft 365 Defender portal (formerly Microsoft 365 Defender).
Client behavioral blocking is effective because it not only helps prevent an attack from starting, it can help stop an attack that has begun executing. And, with feedback-loop blocking (another capability of behavioral blocking and containment), attacks are prevented on other devices in your organization.
Behavior-based detections
Behavior-based detections are named according to the MITRE ATT&CK Matrix for Enterprise. The naming convention helps identify the attack stage where the malicious behavior was observed:
| Tactic | Detection threat name |
|---|---|
| Initial Access | Behavior:Win32/InitialAccess.*!ml |
| Execution | Behavior:Win32/Execution.*!ml |
| Persistence | Behavior:Win32/Persistence.*!ml |
| Privilege Escalation | Behavior:Win32/PrivilegeEscalation.*!ml |
| Defense Evasion | Behavior:Win32/DefenseEvasion.*!ml |
| Credential Access | Behavior:Win32/CredentialAccess.*!ml |
| Discovery | Behavior:Win32/Discovery.*!ml |
| Lateral Movement | Behavior:Win32/LateralMovement.*!ml |
| Collection | Behavior:Win32/Collection.*!ml |
| Command and Control | Behavior:Win32/CommandAndControl.*!ml |
| Exfiltration | Behavior:Win32/Exfiltration.*!ml |
| Impact | Behavior:Win32/Impact.*!ml |
| Uncategorized | Behavior:Win32/Generic.*!ml |
Tip
To learn more about specific threats, see recent global threat activity.
Configuring client behavioral blocking
If your organization is using Defender for Endpoint, client behavioral blocking is enabled by default. However, to benefit from all Defender for Endpoint capabilities, including behavioral blocking and containment, make sure the following features and capabilities of Defender for Endpoint are enabled and configured:
- Defender for Endpoint baselines
- Devices onboarded to Defender for Endpoint
- EDR in block mode
- Attack surface reduction
- Next-generation protection (antivirus, antimalware, and other threat protection capabilities)