Overview
Today’s threat landscape is overrun by fileless malware and that lives off the land, highly polymorphic threats that mutate faster than traditional solutions can keep up with, and human-operated attacks that adapt to what adversaries find on compromised devices. Traditional security solutions aren’t sufficient to stop such attacks; you need artificial intelligence (AI) and device learning (ML) backed capabilities, such as behavioral blocking and containment, included in Defender for Endpoint.
Behavioral blocking and containment capabilities can help identify and stop threats, based on their behaviors and process trees even when the threat has started execution. Next-generation protection, EDR, and Defender for Endpoint components and features work together in behavioral blocking and containment capabilities.
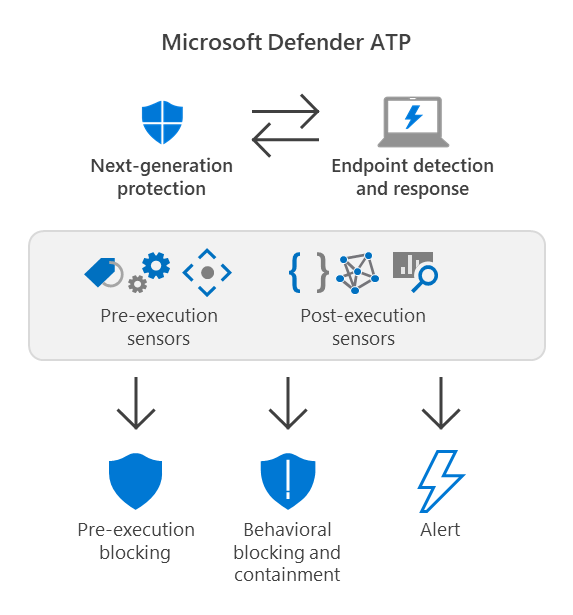
Behavioral blocking and containment capabilities work with multiple components and features of Defender for Endpoint to stop attacks immediately and prevent attacks from progressing.
- Next-generation protection (which includes Microsoft Defender Antivirus) can detect threats by analyzing behaviors, and stop threats that have started running.
- Endpoint detection and response (EDR) receives security signals across your network, devices, and kernel behavior. As threats are detected, alerts are created. Multiple alerts of the same type are aggregated into incidents, which makes it easier for your security operations team to investigate and respond.
- Defender for Endpoint has a wide range of optics across identities, email, data, and apps, in addition to the network, endpoint, and kernel behavior signals received through EDR. A component of Microsoft 365 Defender, Defender for Endpoint processes and correlates these signals, raises detection alerts, and connects related alerts in incidents.
With these capabilities, more threats can be prevented or blocked, even if they start running. Whenever suspicious behavior is detected, the threat is contained, alerts are created, and threats are stopped in their tracks.
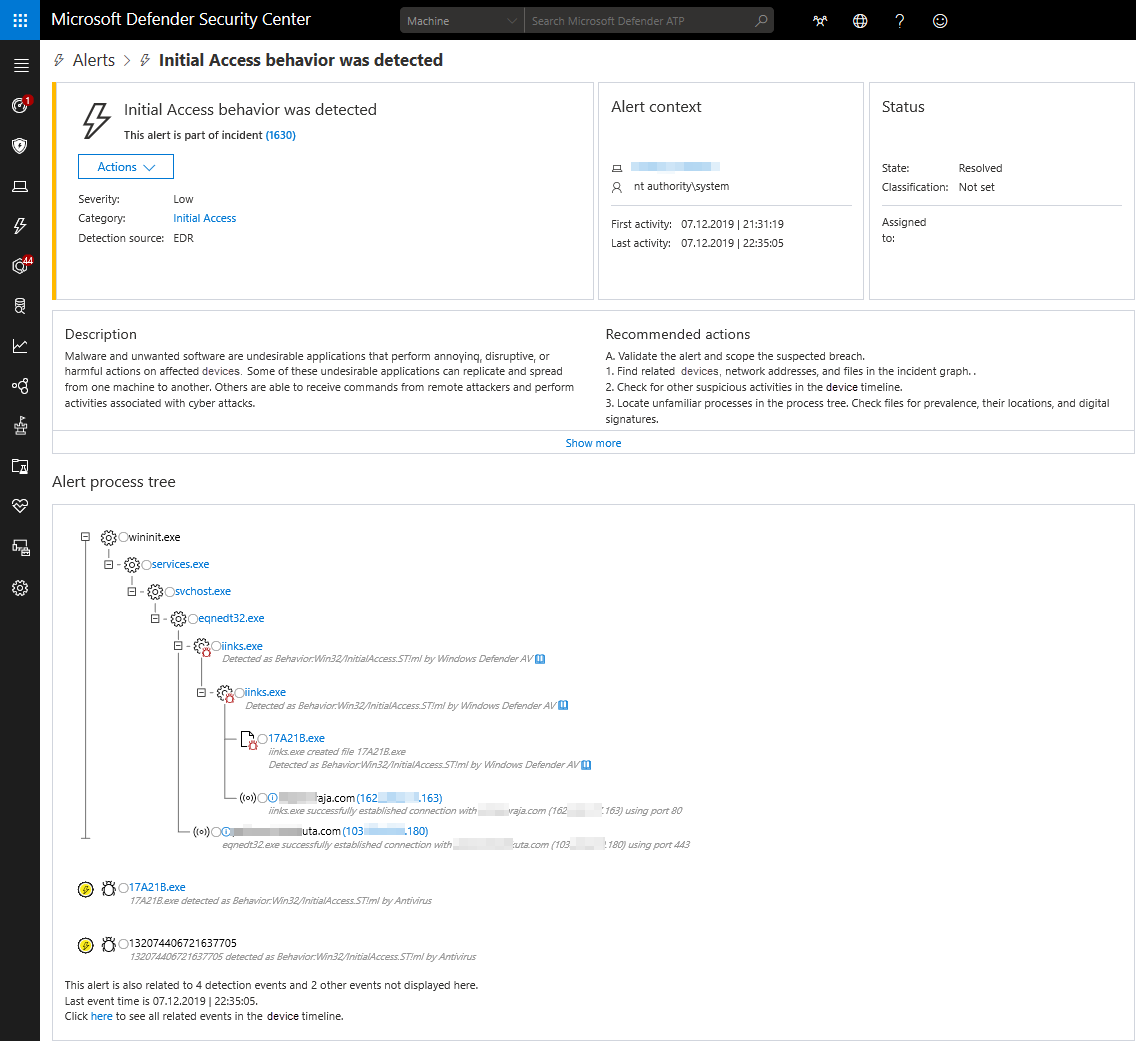
The following image shows an example of an alert that was triggered by behavioral blocking and containment capabilities:
Components of behavioral blocking and containment
- On-client, policy-driven attack surface reduction rules Predefined common attack behaviors are prevented from executing, according to your attack surface reduction rules. When such behaviors attempt to execute, they can be seen in Microsoft 365 Defender as informational alerts. Attack surface reduction rules aren’t enabled by default; you configure your policies in the Microsoft 365 Defender portal.
- Client behavioral blocking Threats on endpoints are detected through machine learning, and then are blocked and remediated automatically. (Client behavioral blocking is enabled by default.)
- Feedback-loop blocking (also referred to as rapid protection) Threat detections are observed through behavioral intelligence. Threats are stopped and prevented from running on other endpoints. (Feedback-loop blocking is enabled by default.)
- Endpoint detection and response (EDR) in block mode Malicious artifacts or behaviors that are observed through post-breach protection are blocked and contained. EDR in block mode works even if Microsoft Defender Antivirus isn’t the primary antivirus solution. (EDR in block mode isn’t enabled by default; you turn it on in Microsoft 365 Defender.)
Expect more to come in the area of behavioral blocking and containment, as Microsoft continues to improve threat protection features and capabilities. To see what’s planned and rolling out now, visit the Microsoft 365 roadmap.
Examples of behavioral blocking and containment in action
Behavioral blocking and containment capabilities have blocked attacker techniques such as the following:
- Credential dumping from LSASS
- Cross-process injection
- Process hollowing
- User Account Control bypass
- Tampering with antivirus (such as disabling it or adding the malware as exclusion)
- Contacting Command and Control (C&C) to download payloads
- Coin mining
- Boot record modification
- Pass-the-hash attacks
- Installation of root certificate
- Exploitation attempt for various vulnerabilities
Below are two real-life examples of behavioral blocking and containment in action.
Example 1: Credential theft attack against 100 organizations
As described in In hot pursuit of elusive threats: AI-driven behavior-based blocking stops attacks in their tracks, a credential theft attack against 100 organizations around the world was stopped by behavioral blocking and containment capabilities. Spear-phishing email messages that contained a lure document were sent to the targeted organizations. If a recipient opened the attachment, a related remote document was able to execute code on the user’s device and load Lokibot malware, which stole credentials, exfiltrated stolen data, and waited for further instructions from a command-and-control server.
Behavior-based device learning models in Defender for Endpoint caught and stopped the attacker’s techniques at two points in the attack chain:
- The first protection layer detected the exploit behavior. Device learning classifiers in the cloud correctly identified the threat as and immediately instructed the client device to block the attack.
- The second protection layer, which helped stop cases where the attack got past the first layer, detected process hollowing, stopped that process, and removed the corresponding files (such as Lokibot).
While the attack was detected and stopped, alerts, such as an “initial access alert,” were triggered and appeared in the Microsoft 365 Defender portal.
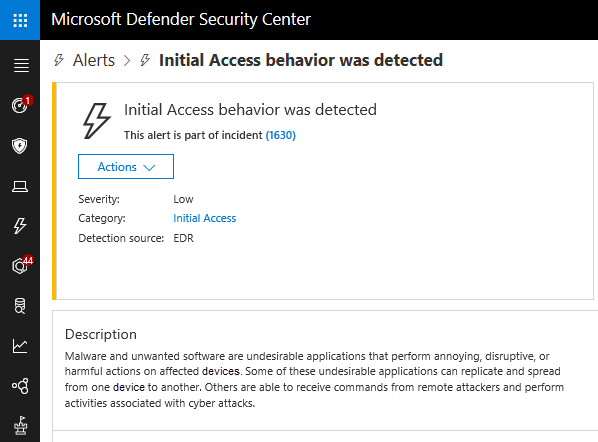
This example shows how behavior-based device learning models in the cloud add new layers of protection against attacks, even after they have started running.
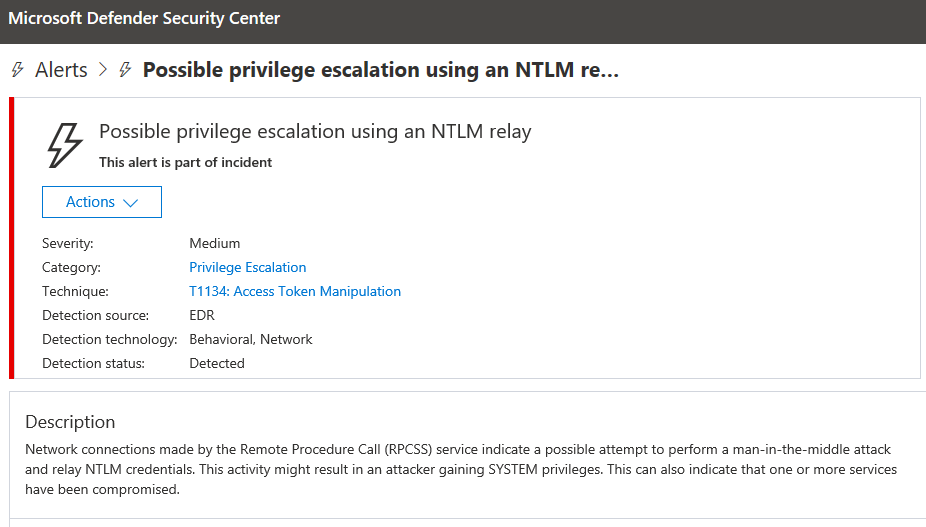
Example 2: NTLM relay – Juicy Potato malware variant
As described in the recent blog post, Behavioral blocking and containment: Transforming optics into protection, in January 2020, Defender for Endpoint detected a privilege escalation activity on a device in an organization. An alert called “Possible privilege escalation using NTLM relay” was triggered.
The threat turned out to be malware; it was a new, not-seen-before variant of a notorious hacking tool called Juicy Potato, which is used by attackers to get privilege escalation on a device.
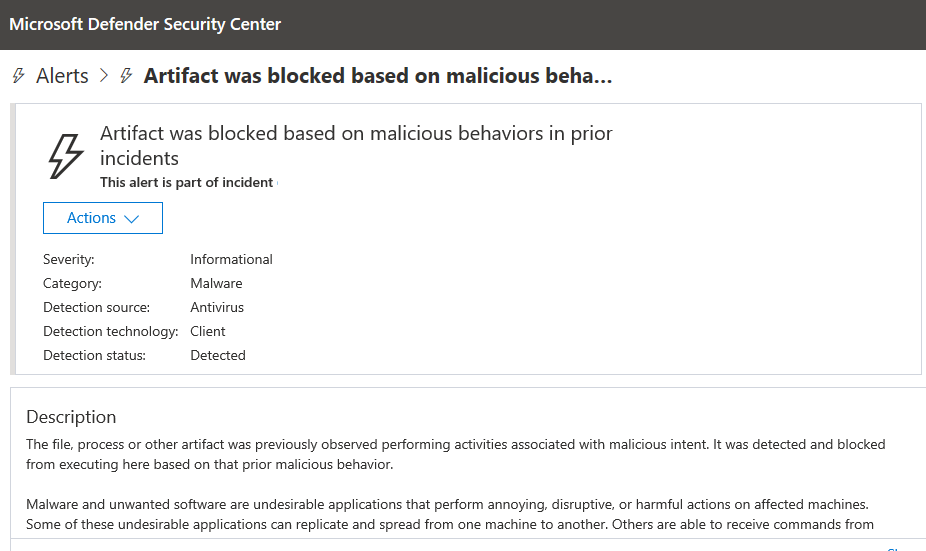
Minutes after the alert was triggered, the file was analyzed, and confirmed to be malicious. Its process was stopped and blocked, as shown in the following image:
A few minutes after the artifact was blocked, multiple instances of the same file were blocked on the same device, preventing more attackers or other malware from deploying on the device.
This example shows that with behavioral blocking and containment capabilities, threats are detected, contained, and blocked automatically.