This article is designed to help you understand how Microsoft Defender for Identity functionality is represented in the Microsoft Defender for Cloud Apps portal.
Leveraging existing on-premise detections and abnormal behavior analytics, accessing Defender for Identity using the Microsoft Defender for Cloud Apps portal provides the ability to detect and alert on sensitive data exfiltration across your enterprise. This hybrid offering analyzes activity and alerts based on User and Entity Behavior Analytics (UEBA) to determine risky behaviors, and provides an investigation priority score to streamline your incident response for compromised identities.
In this article you’ll learn:
- Service overview
- New ways to access Defender for Identity
- Licensing prerequisites
- Where to find Defender for Identity tracked activities in Defender for Cloud Apps
Service overview
Integrating with Defender for Identity, the Defender for Cloud Apps portal provides alerts and insights from:
- Microsoft Defender for Cloud Apps, which identifies attacks within a cloud session, covering not only Microsoft products but also third-party applications
- Microsoft Defender for Identity, which uses machine learning and behavioral analytics to identify attacks across your on-premises network
- Azure Active Directory Identity Protection, which detects and proactively prevents user and sign-in risks to identities in the cloud
Prerequisites
For complete user investigation features across the hybrid environment, you must have:
- A valid license for Microsoft Defender for Cloud Apps
- A valid license for Microsoft Defender for Identity connected to your Active Directory instance
Note
- If you don’t have a subscription for Defender for Cloud Apps, you will still be able to use the Defender for Cloud Apps portal to investigate Defender for Identity alerts and deep dive on users and their on-premise managed activities, but you won’t receive related insights from your cloud applications.
- Defender for Identity administrators may require new permissions to access Defender for Cloud Apps. To learn how to assign permissions to Defender for Cloud Apps, see Manage admin access.
See Defender for Identity integration to learn how to quickly enable Defender for Identity in Defender for Cloud Apps.
Defender for Identity in Defender for Cloud Apps
See the Defender for Cloud Apps quickstart to familiarize yourself with the basics of using the Defender for Cloud Apps portal.
Alerts
Defender for Identity alerts are displayed within the Defender for Cloud Apps Alerts queue. Additional alert filtering options are available only when viewing alerts using Defender for Cloud Apps. Defender for Identity alerts are filtered using the application filter to Active Directory.
Alert management
When using Defender for Identity with Defender for Cloud Apps, closing alerts in one service won’t automatically close them in the other service. More specifically, closing alerts in Defender for Cloud Apps won’t close them in Defender for Identity, but closing alerts in Defender for Identity will synchronize the closure in Defender for Cloud Apps. Decide where to manage and remediate alerts to avoid duplicated efforts.
SIEM notification
If both your services (Defender for Identity and Defender for Cloud Apps) are currently configured to send alert notifications to a SIEM, after enabling Defender for Identity integration in Defender for Cloud Apps, you’ll start to receive duplicate SIEM notifications for the same alert. One alert will be issued from each service and they’ll have different alert IDs. To avoid duplication and confusion, decide where you intend to perform alert management, and then stop SIEM notifications being sent from the other service.
Activities
Defender for Identity alerts are displayed within the Defender for Cloud Apps Activity log. Additional activity filtering options and features are available only when viewing alerts using Defender for Cloud Apps. See Defender for Identity activities using Microsoft Defender for Cloud Apps to learn how to filter and create new activity policies.
User pages
User pages contain the Investigation Priority Score of each user and an activity log of all actions.
To access a user page of a system user:
- Open Alerts from the main menu.
- Select and filter the alerts queue for a specific user by using the User Name field.
or
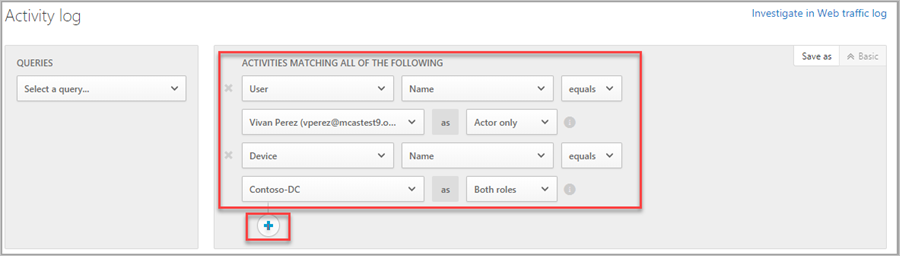
- From the Investigate menu, select Activity log.
- Filter the Activity log queue by user.
Join the Community
Do you have more questions, or an interest in discussing Defender for Identity and related security with others? Join the Defender for Identity Community today!

