The Virus.Win32.Gpcode.ak malware encrypts user files of various formats, such as DOC, TXT, PDF, XLS, JPG, PNG, CPP. To recover files that have been encrypted by Virus.Win32.Gpcode.ak, use the PhotoRec tool.
To avoid infection:
- Download and install Kaspersky Internet Security, which protects your PC against file-encrypting and screen-locking malware.
- Follow the recommendations in this article.
How to recover files using the PhotoRec tool
To recover files you will need an external storage drive, such as a USB drive.
- Download the TestDisk archive from the vendor’s website and extract the files.
- Save the extracted files to the external storage.
- Connect the external storage to the infected PC.
- Open the folder with the saved files and run photorec_win.exe.
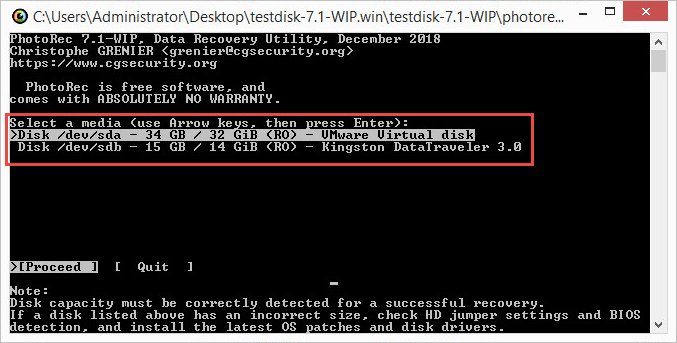
- Select the disk the tool is saved on. Press Enter.
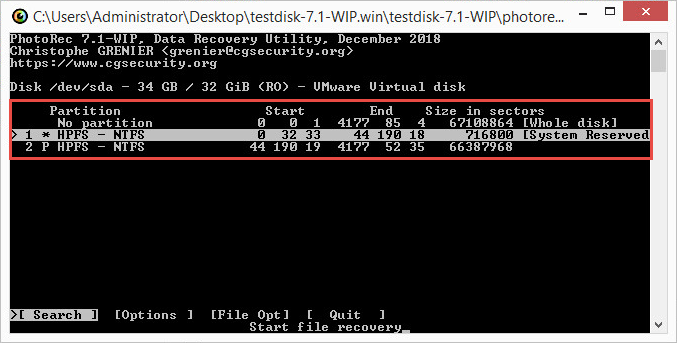
- Select the disk partition to scan. Press Enter on the keyboard. If the disk has multiple partitions, repeat this step for each one.
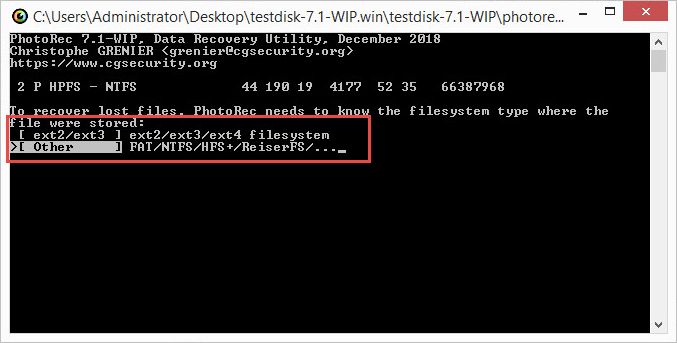
- Select the file system type. Press Enter on the keyboard.
- Select the disk space to scan for encrypted files. Press Enter on the keyboard.
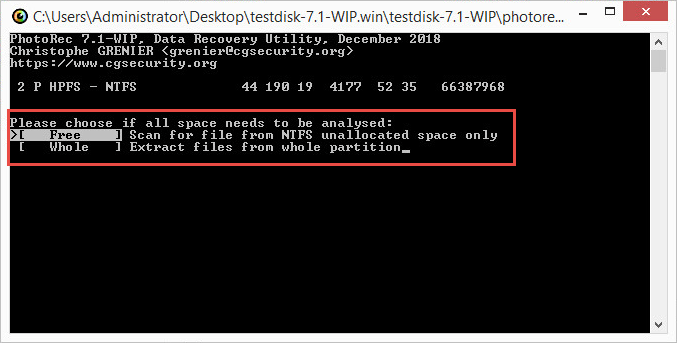
- Specify the folder in which to save the decrypted files.
- Go to the root folder. To do so, select the “…” folder twice.
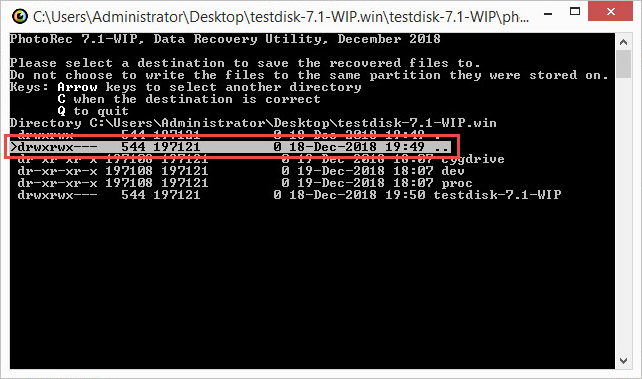
- Select the external storage drive.
- Create a folder on the external storage drive in which to save the decrypted files. Name it, for example, Recovered.
- Select the Recovered folder.
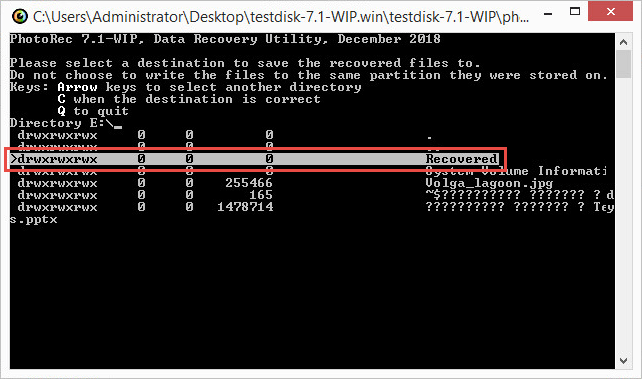
- Press Y on the keyboard.
- Go to the root folder. To do so, select the “…” folder twice.
- Wait until the scan has completed.
The decrypted files will be saved on the external storage drive in the specified folder under names such as t*.jpg or t*.txt.
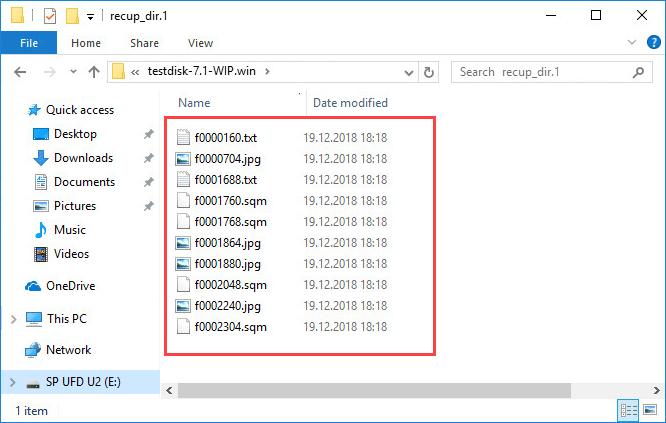
How to rename and sort decrypted files
Using the StopGpcode tool, you can rename and sort decrypted files:
- Download the StopGpcode tool and save it to an external storage drive.
- Connect the external storage to the infected PC.
- Open the command line.
- Run the command:
Where:
- -r <decrypted files> — path to the folder containing the files decrypted by the PhotoRec tool
- -i <encrypted files> — path to the disk or folder containing the encrypted files
- -o <files with recovered names> — path to the folder where the files with recovered names will be saved
The tool will collate the sizes of the decrypted and encrypted files and save to the folder:
- “Sorted” decrypted files with recovered names, copying the original folder structures.
- “Conflicted” decrypted files without recovered names.
Editor by : BEST Antivirus KBS Team

