How to use the tool in normal or safe mode
- Download the TDSSKiller tool.
-
To protect your devices against threats, install Kaspersky Internet Security.
- Run TDSSKiller.exe on the infected computer.
- Carefully read through the Kaspersky End User License Agreement. Click Accept if you agree with all the points.
- Carefully read through the Kaspersky Security Network Statement. Click Accept if you agree with all the points.
- Click Start scan.
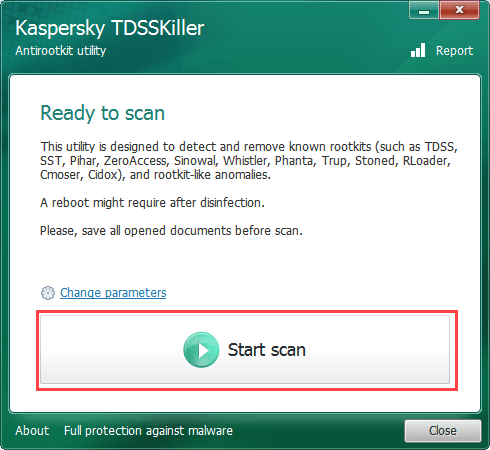
- Wait until the scan and disinfection have been completed.
You do not need to reboot your computer after disinfection.
How to use the tool in silent mode from the command line
To use the TDSSKiller tool from the command line, use the parameters in the table below:
| Parameter | Description |
|---|---|
| -accepteula | Confirms your acceptance of the End User License Agreement. |
| -accepteulaksn | About participation in Kaspersky Security Network |
| -l <file_name> | Write the report to a file. |
| -qpath <folder_name> | Select the location of the quarantine folder. |
| -qall | Copy all objects to quarantine, including clean ones. |
| -qsus | Only copy suspicious files to quarantine. |
| -qmbr | Copy all master boot records (MBR) to quarantine. |
| -qboot | Copy all boot sectors to quarantine. |
| -quefi | Copy all UEFI extensions to quarantine. |
| -dcexact | Automatically disinfect or delete known threats. Apply it with the key -silent to disinfect a large number of computers in a network. |
| -qcsvc <service_name> | Copy the specified service to quarantine. |
| -dcsvc <service_name> | Delete the specified service. |
| -sigcheck | Detect files that don’t have a digital signature, or have an invalid one.
These files could be infected. If you suspect that it’s an infected file, scan it using OpenTip. |
| -tdlfs | Detect TDL-3/4 system files that are created by TDL-3/4 rootkits in the last hard drive sectors for storing files. All these files can be copied to quarantine. |
| -silent | Start a silent scan. This can be applied in order to start the tool centrally across a network. |
| -freboot | Install the extended monitoring driver and reboot before scan. |
| -fixmbr <drive_name> | Restore the master boot record (MBR) on the specified disk drive. |
| -fixboot <partition_name> | Restore VBR and EIPL on the specified partition. |
For example, to scan the computer and write a detailed report to the report.txt file, which will be created in the folder with the TDSSKiller tool, use the command:
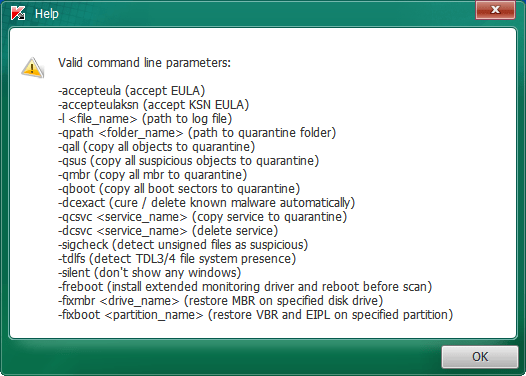
To view a list of the available command line parameters for the TDSSKiller tool, use the command:
List of supported operating systems
- Microsoft Windows XP SP2, SP3
- Microsoft Windows Vista
- Microsoft Windows Vista SP1, SP2
- Microsoft Windows 7
- Microsoft Windows 7 SP1
- Microsoft Windows 8, 8.1
- Microsoft Windows 10 TH1, TH2, RS1, RS2, RS3, RS4, RS5, RS6
- Microsoft Windows Server 2003 R2 Standard / Enterprise SP2
- Microsoft Windows Server 2003 Standard / Enterprise SP2
- Microsoft Windows Server 2008 Standard / Enterprise SP2
- Microsoft Windows Small Business Server 2011
- Microsoft Windows Server 2008 R2 Standard / Enterprise SP0 and later 64-bit
- Microsoft Windows Server 2012 64-bit
- Microsoft Windows Server 2012 R2 64-bit
- Microsoft Windows Server 2016 64-bit
List of malware that TDSSKiller detects and removes
The TDSSKiller tool is designed to detect and remove malware from the Rootkit.Win32.TDSS family, as well as bootkits and rootkits. These include the following malicious applications:
- Backdoor.Win32.Phanta.a,b
- Backdoor.Win32.Sinowal.knf,kmy
- Backdoor.Win32.Trup.a,b
- Rootkit.Boot.Mebusta.a
- Rootkit.Boot.Backboot.c
- Rootkit.Boot.Aeon.a
- Rootkit.Boot.Adrasteia.a
- Rootkit.Boot.Backboot.a
- Rootkit.Boot.Batan.a
- Rootkit.Boot.Bootkor.a
- Rootkit.Boot.Clones.a
- Rootkit.Boot.CPD.a,b
- Rootkit.Boot.Fisp.a
- Rootkit.Boot.Geth.a
- Rootkit.Boot.Goodkit.a
- Rootkit.Boot.Harbinger.a
- Rootkit.Boot.Krogan.a
- Rootkit.Boot.Lapka.a
- Rootkit.Boot.MyBios.b
- Rootkit.Boot.Nimnul.a
- Rootkit.Boot.Nix.a
- Rootkit.Boot.Pihar.a,b,c
- Rootkit.Boot.Plite.a
- Rootkit.Boot.Prothean.a
- Rootkit.Boot.Qvod.a
- Rootkit.Boot.Sawlam.a
- Rootkit.Boot.Smitnyl.a
- Rootkit.Boot.SST.a,b
- Rootkit.Boot.SST.b
- Rootkit.Boot.Wistler.a
- Rootkit.Boot.Xpaj.a
- Rootkit.Boot.Yurn.a
- Rootkit.Win32.PMax.gen
- Rootkit.Win32.Stoned.d
- Rootkit.Win32.TDSS
- Rootkit.Win32.TDSS.mbr
- Rootkit.Win32.ZAccess.aml,c,e,f,g,h,i,j,k
- Trojan-Clicker.Win32.Wistler.a,b,c
- Trojan-Dropper.Boot.Niwa.a
- Trojan-Ransom.Boot.Mbro.d,e
- Trojan-Ransom.Boot.Mbro.f
- Trojan-Ransom.Boot.Siob.a
- Trojan-Spy.Win32.ZBot
- Virus.Win32.Cmoser.a
- Virus.Win32.Rloader.a
- Virus.Win32.TDSS.a,b,c,d,e
- Virus.Win32.Volus.a
- Virus.Win32.ZAccess.k
- Virus.Win32.Zhaba.a,b,c
Source : Official Kaspersky Brand
Editor by : BEST Antivirus KBS Team

