Important
The improved Microsoft 365 Defender portal is now available. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 Defender portal. Learn what’s new.
Applies to:
- Microsoft 365 Defender
- Microsoft Defender for Endpoint
Important
Some information relates to prereleased product which may be substantially modified before it’s commercially released. Microsoft makes no warranties, express or implied, with respect to the information provided here.
You can quickly contain threats or address compromised assets that you find in advanced hunting using powerful and comprehensive action options. With these options, you can:
- Take various actions on devices
- Quarantine files
Required permissions
To take action through advanced hunting, you need a role in Microsoft Defender for Endpoint with permissions to submit remediation actions on devices. If you can’t take action, contact a global administrator about getting the following permission:
Active remediation actions > Threat and vulnerability management – Remediation handling
Take various actions on devices
You can take the following actions on devices identified by the DeviceId column in you query results:
- Isolate affected devices to contain an infection or prevent attacks from moving laterally
- Collect investigation package to obtain more forensic information
- Run an antivirus scan to find and remove threats using the latest security intelligence updates
- Initiate an automated investigation to check and remediate threats on the device and possibly other affected devices
- Restrict app execution to only Microsoft-signed executable files, preventing subsequent threat activity through malware or other untrusted executables
To learn more about how these response actions are performed through Microsoft Defender for Endpoint, read about response actions on devices.
Quarantine files
You can deploy the quarantine action on files so that they are automatically quarantined when encountered. When selecting this action, you can choose between the following columns to identify which files in your query results to quarantine:
SHA1— In most advanced hunting tables, this is the SHA-1 of the file that was affected by the recorded action. For example, if a file was copied, this would be the copied file.InitiatingProcessSHA1— In most advanced hunting tables, this is the file responsible for initiating the recorded action. For example, if a child process was launched, this would be the parent process.SHA256— This is the SHA-256 equivalent of the file identified by theSHA1column.InitiatingProcessSHA256— This is the SHA-256 equivalent of the file identified by theInitiatingProcessSHA1column.
To learn more about how quarantine actions are taken and how files can be restored, read about response actions on files.
Note
To locate files and quarantine them, the query results should also include DeviceId values as device identifiers.
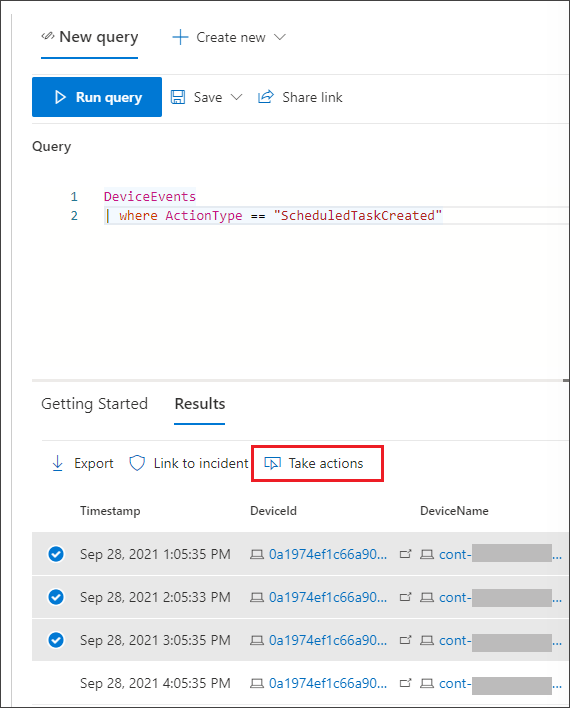
Take action
To take any of the described actions, select one or more records in your query results and then select Take actions. A wizard will guide you through the process of selecting and then submitting your preferred actions.
Review actions taken
Each action is individually recorded in the action center under Action center > History (security.microsoft.com/action-center/history). Go to the action center to check the status of each action.
Note
Some tables in this article might not be available in Microsoft Defender for Endpoint. Turn on Microsoft 365 Defender to hunt for threats using more data sources. You can move your advanced hunting workflows from Microsoft Defender for Endpoint to Microsoft 365 Defender by following the steps in Migrate advanced hunting queries from Microsoft Defender for Endpoint.

