Suspicious Activity Monitoring is a feature included in Malwarebytes Endpoint Detection and Response. It watches for potentially malicious behavior by monitoring the processes, registry, file system, and network activity on the endpoint.
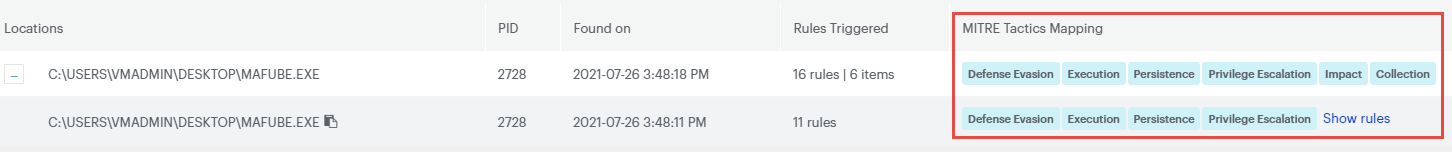
From the Suspicious Activity screen, you can click the Locations item or the number of rules triggered to view the Suspicious Activity Details screen.
This screen shows specific details of the chosen Suspicious Activity to help you better understand the activities of this file or process. These details can help you make an educated decision on what action you should perform on the item. This article provides an overview of the Suspicious Activity Details screen.
Suspicious Activity Rules Triggered
The tile at the top of the Suspicious Activity Details screen shows a list of files Malwarebytes found suspicious as well as any files or processes that spawned from the primary file or process. Click the Show Summary button next to Rules Triggered Suspicious Activity to expand details. Here you can see all the MITRE ATT&CK detection rules involved in making the overall suspicious activity. Click MITRE ATT&CK Framework at the top for more information.
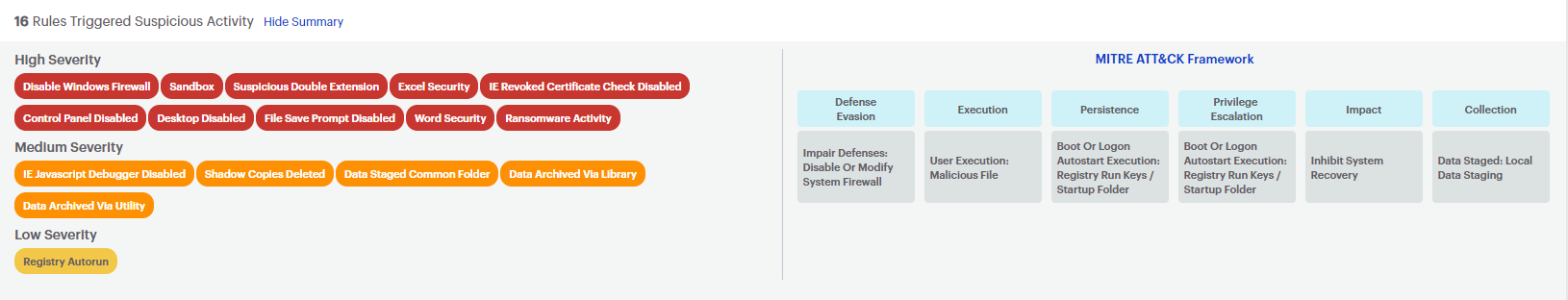
MITRE Tactics Mapping categorizes suspicious activity detections based on the exhibited behaviors of the file or process. We provide a Show rules link to view the detection rules that triggered this suspicious activity detection.
The detection rules are color coded based on severity and the MITRE ATT&CK Framework:
- Red: High Severity
- Yellow: Medium Severity
- Blue: Low Severity
You can click each color-coded rule to reveal details about the specific detection rule. In the MITRE Tactics Mapping column, click Show rules to list all trigger rules for the detection.
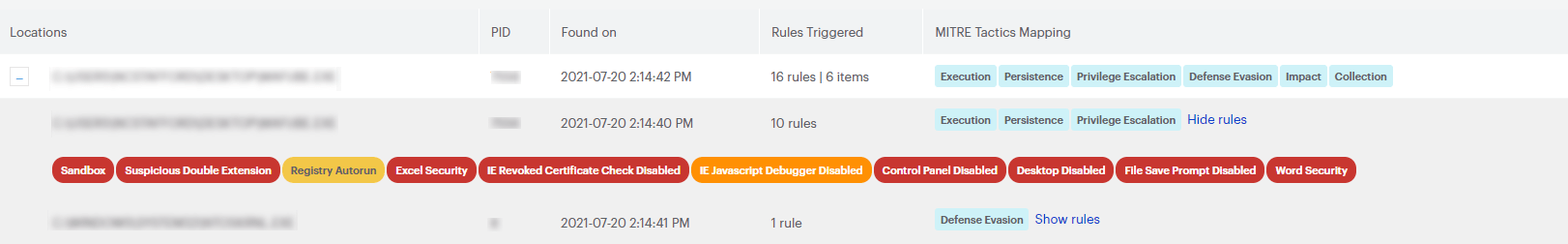
When you click a trigger rule, a window appears to show a description of the rule and context. Below shows an example ransomware activity.
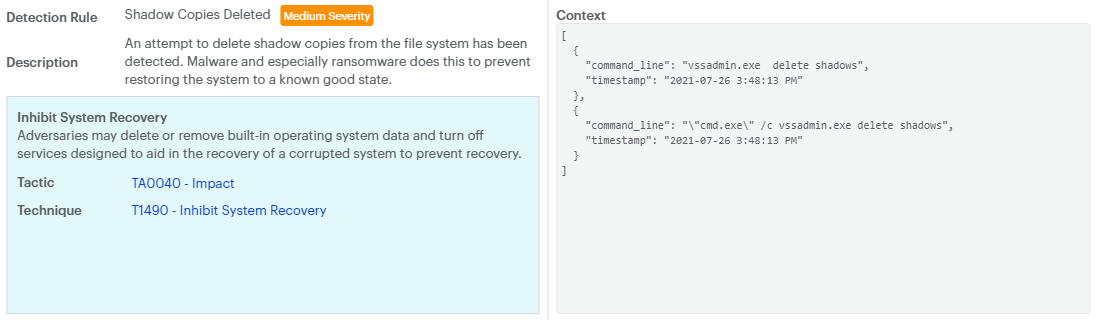
A trigger rule displays the following information pulled from MITRE Tactic Mapping:
- Detection Rule
- Severity
- Description
- Context
- MITRE ATT&CK Tactic Name
- Tactic: Link to MITRE ATT&CK Tactic
- Technique: Link to MITRE ATT&CK Technique
Process Graph
The tile under the Suspicious Activity records is the Process Graph, which shows a visual representation of the files or processes touched by the suspicious activity, including any files or processes spawned from the original file or process.
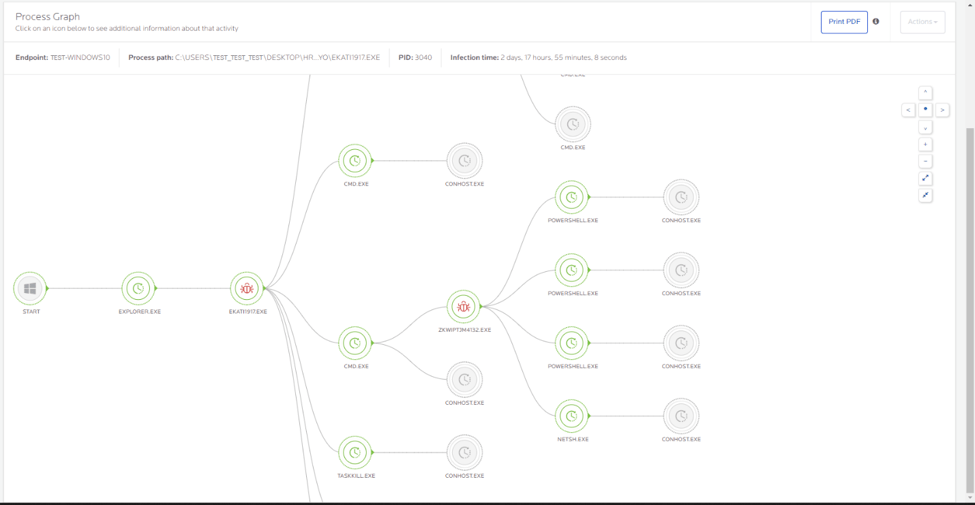
The Process Graph is made up of nodes representing files or processes with links representing the relationships between files or processes. These could be executed, spawned or touched files or processes. The Process Graph has several display controls in the upper right of the graph allowing you to zoom in/out or re-position the graph. Click the Print PDF button above the Process Graph if you to print copies of the graph.
Node details
Click on a node to see deeper details on that specific file or process. The available information differs depending on the color of the node selected. Green nodes are typically benign files or processes and red nodes represent actual suspicious files or processes.
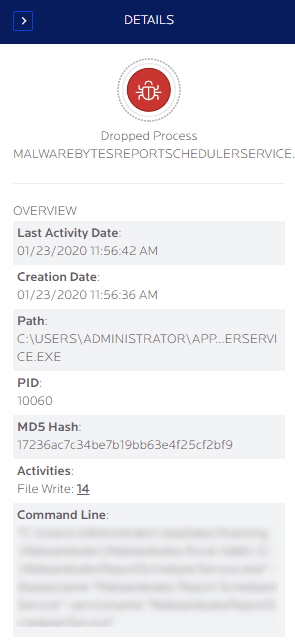
Node details show the following information:
- Last activity Date
- Creation Date
- full Path
- process ID
- MD5 Hash
- Activities
- Command line parameters
Some nodes contain raw activities performed by the file or process. Next to the Activities there is typically a number associated with the File Write, File Read or Reg set Value. Click this number to reveal a comprehensive list of raw activities executed by the file or process.
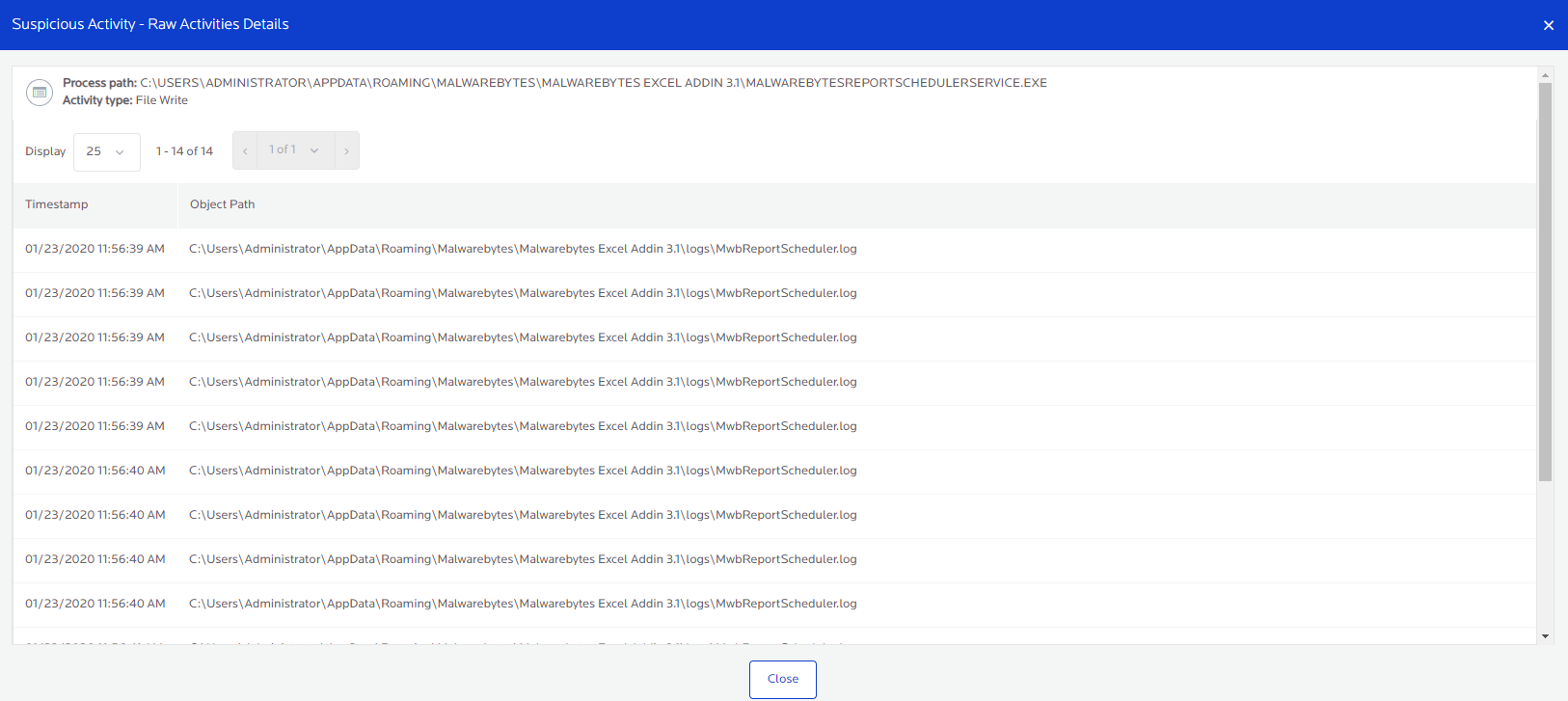
Raw activities can be:
- File Writes: When the file or process attempted to write to the file system, including renaming of files common during a ransomware attack.
- Read Files: When the file or process attempts to read other files within the file system.
- Reg Set Values: When the file or process attempts to make changes to the Windows Registry.
Source : Official Malwarebytes Brand
Editor by : BEST Antivirus KBS Team

