Applies to: Microsoft 365 Defender
This article will guide you in the process of setting up the evaluation for Microsoft Defender for Endpoint environment.
For more information about this process, see the overview article.
Before enabling Microsoft Defender for Endpoint, be sure you understand the architecture and can meet the requirements.
Understand the architecture
The following diagram illustrates Microsoft Defender for Endpoint architecture and integrations.
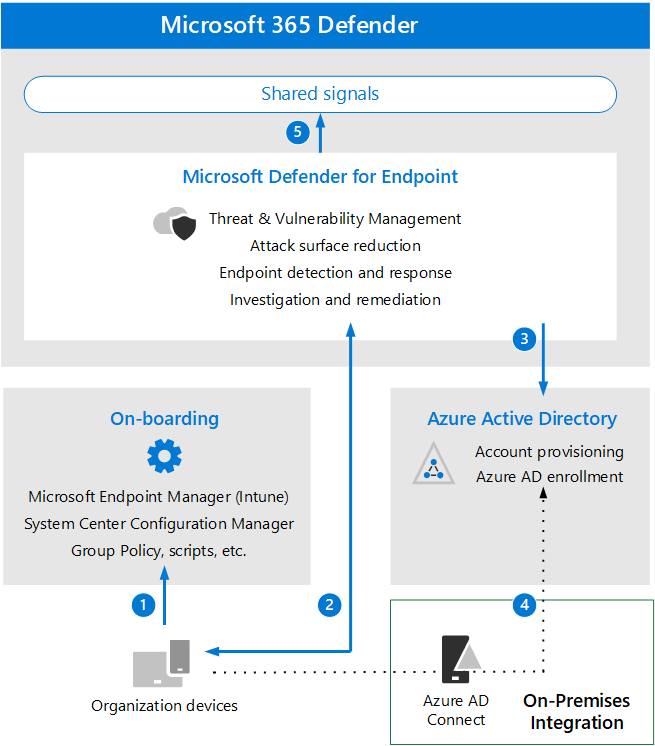
The following table describes the illustration.
| Call-out | Description |
|---|---|
| 1 | Devices are on-boarded through one of the supported management tools. |
| 2 | On-boarded devices provide and respond to Microsoft Defender for Endpoint signal data. |
| 3 | Managed devices are joined and/or enrolled in Azure Active Directory. |
| 4 | Domain-joined Windows devices are synchronized to Azure Active Directory using Azure Active Directory Connect. |
| 5 | Microsoft Defender for Endpoint alerts, investigations, and responses are managed in Microsoft 365 Defender. |
Understand key concepts
The following table identified key concepts that are important to understand when evaluating, configuring, and deploying Microsoft Defender for Endpoint:
| Concept | Description | More information |
|---|---|---|
| Administration Portal | Microsoft 365 Defender portal to monitor and assist in responding to alerts of potential advanced persistent threat activity or data breaches. | Microsoft Defender for Endpoint portal overview |
| Attack Surface Reduction | Help reduce your attack surfaces by minimizing the places where your organization is vulnerable to cyberthreats and attacks. | Overview of attack surface reduction |
| Endpoint Detection and Response | Endpoint detection and response capabilities provide advanced attack detections that are near real-time and actionable. | Overview of endpoint detection and response capabilities |
| Behavioral Blocking and Containment | Behavioral blocking and containment capabilities can help identify and stop threats, based on their behaviors and process trees even when the threat has started execution. | Behavioral blocking and containment |
| Automated Investigation and Response | Automated investigation uses various inspection algorithms based on processes that are used by security analysts and designed to examine alerts and take immediate action to resolve breaches. | Use automated investigations to investigate and remediate threats |
| Advanced Hunting | Advanced hunting is a query-based threat-hunting tool that lets you explore up to 30 days of raw data so that you can proactively inspect events in your network to locate threat indicators and entities. | Overview of advanced hunting |
| Threat Analytics | Threat analytics is a set of reports from expert Microsoft security researchers covering the most relevant threats. | Track and respond to emerging threats |
For more detailed information about the capabilities included with Microsoft Defender for Endpoint, see What is Microsoft Defender for Endpoint.
SIEM integration
You can integrate Microsoft Defender for Endpoint with Microsoft Sentinel to more comprehensively analyze security events across your organization and build playbooks for effective and immediate response.
Microsoft Defender for Endpoint can also be integrated into other Security Information and Event Management (SIEM) solutions. For more information, see Enable SIEM integration in Microsoft Defender for Endpoint.

