Important
The improved Microsoft 365 Defender portal is now available. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 Defender portal. Learn what’s new.
Important
Some information relates to prereleased product which may be substantially modified before it’s commercially released. Microsoft makes no warranties, express or implied, with respect to the information provided here.
Applies to:
To implement a multi-tenant delegated access solution, take the following steps:
- Enable role-based access control for Defender for Endpoint via the Microsoft 365 Defender portal and connect with Azure Active Directory (Azure AD) groups.
- Configure Governance Access Packages for access request and provisioning.
- Manage access requests and audits in Microsoft Myaccess.
Enable role-based access controls in Microsoft Defender for Endpoint in Microsoft 365 Defender portal
- Create access groups for MSSP resources in Customer AAD: Groups
These groups will be linked to the Roles you create in Defender for Endpoint in Microsoft 365 Defender portal. To do so, in the customer AD tenant, create three groups. In our example approach, we create the following groups:
- Tier 1 Analyst
- Tier 2 Analyst
- MSSP Analyst Approvers
- Create Defender for Endpoint roles for appropriate access levels in Customer Defender for Endpoint in Microsoft 365 Defender portal roles and groups.
To enable RBAC in the customer Microsoft 365 Defender portal, access Permissions > Endpoints roles & groups > Roles with a user account with Global Administrator or Security Administrator rights.
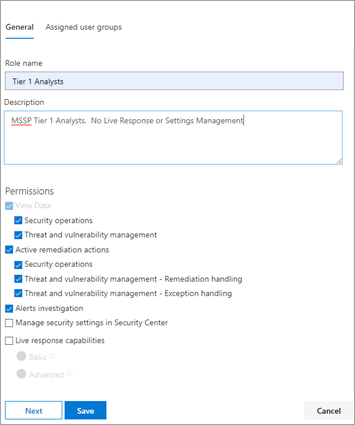
Then, create RBAC roles to meet MSSP SOC Tier needs. Link these roles to the created user groups via “Assigned user groups”.
Two possible roles:
- Tier 1 Analysts
Perform all actions except for live response and manage security settings. - Tier 2 Analysts
Tier 1 capabilities with the addition to live response
For more information, see Use role-based access control.
- Tier 1 Analysts
Configure Governance Access Packages
- Add MSSP as Connected Organization in Customer AAD: Identity Governance
Adding the MSSP as a connected organization will allow the MSSP to request and have accesses provisioned.
To do so, in the customer AD tenant, access Identity Governance: Connected organization. Add a new organization and search for your MSSP Analyst tenant via Tenant ID or Domain. We suggest creating a separate AD tenant for your MSSP Analysts.
- Create a resource catalog in Customer AAD: Identity Governance
Resource catalogs are a logical collection of access packages, created in the customer AD tenant.
To do so, in the customer AD tenant, access Identity Governance: Catalogs, and add New Catalog. In our example, we will call it MSSP Accesses.
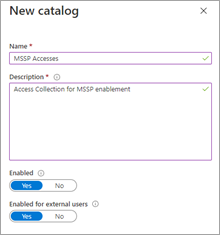
Further more information, see Create a catalog of resources.
- Create access packages for MSSP resources Customer AAD: Identity Governance
Access packages are the collection of rights and accesses that a requestor will be granted upon approval.
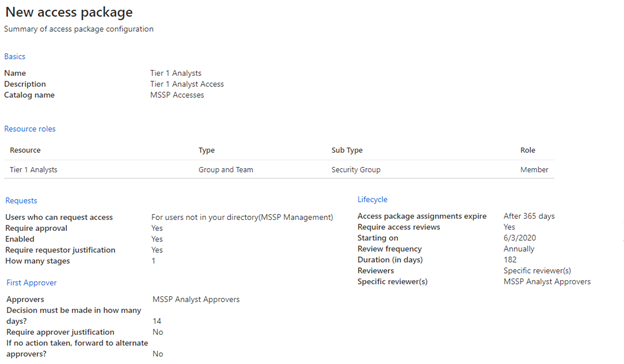
To do so, in the customer AD tenant, access Identity Governance: Access Packages, and add New Access Package. Create an access package for the MSSP approvers and each analyst tier. For example, the following Tier 1 Analyst configuration creates an access package that:
- Requires a member of the AD group MSSP Analyst Approvers to authorize new requests
- Has annual access reviews, where the SOC analysts can request an access extension
- Can only be requested by users in the MSSP SOC Tenant
- Access auto expires after 365 days
For more information, see Create a new access package.
- Provide access request link to MSSP resources from Customer AAD: Identity Governance
The My Access portal link is used by MSSP SOC analysts to request access via the access packages created. The link is durable, meaning the same link may be used over time for new analysts. The analyst request goes into a queue for approval by the MSSP Analyst Approvers.
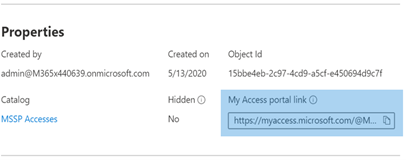
The link is located on the overview page of each access package.
Manage access
- Review and authorize access requests in Customer and/or MSSP myaccess.
Access requests are managed in the customer My Access, by members of the MSSP Analyst Approvers group.
To do so, access the customer’s myaccess using:
https://myaccess.microsoft.com/@<Customer Domain>.Example:
https://myaccess.microsoft.com/@M365x440XXX.onmicrosoft.com#/ - Approve or deny requests in the Approvals section of the UI.
At this point, analyst access has been provisioned, and each analyst should be able to access the customer’s Microsoft 365 Defender portal:
https://security.microsoft.com/?tid=<CustomerTenantId>with the permissions and roles they were assigned.
Important
Delegated access to Microsoft Defender for Endpoint in the Microsoft 365 Defender portal currently allows access to a single tenant per browser window.

