Details
The Host-based Intrusion Prevention System (HIPS) monitors events inside the operating system and reacts accordingly based on a set of pre-defined rules to recognize suspicious system behavior. When this type of activity is identified, the HIPS self-defense mechanism stops the offending program or process from carrying out a potentially harmful activity. Additional HIPS rules can be defined manually by the user.
Solution
 ESET Security Management Center (ESMC) users: Perform these steps in ESMC
ESET Security Management Center (ESMC) users: Perform these steps in ESMC
- Open the main program window of your Windows ESET product.
- Press the F5 key to access Advanced setup.
- Click Detection Engine → HIPS and then click Edit next to Rules.

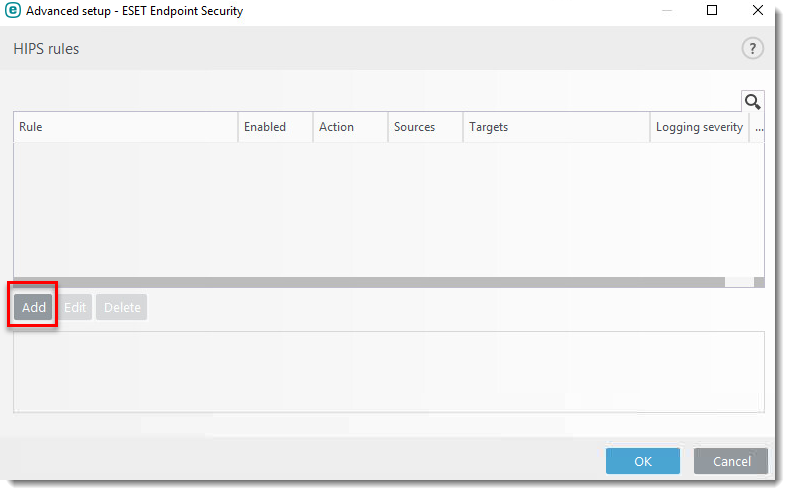
- Click Add.
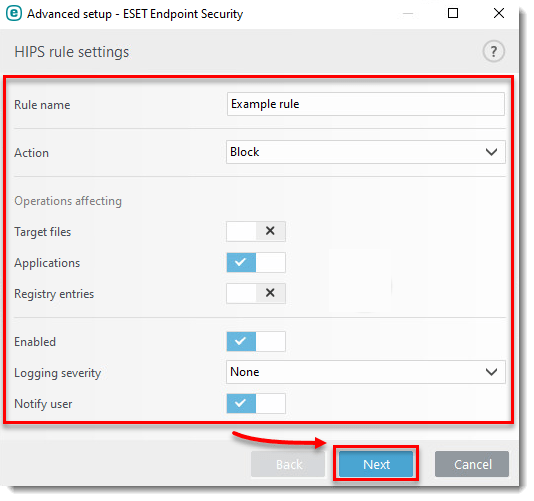
- Configure your rule. In this example, we are blocking operations affecting applications and the user will be notified of the action. Click Next.
- In the Source applications window, select your desired option from the drop-down menu. In this example, the HIPS rule will block any application that attempts to modify registry values. Click Next.

- In the Application operation window, click the slider bar next to the operation(s) you want to block. In this example, the HIPS rule will block any application that attempts to debug another application. Click Next.

- In the Applications window, select your desired option from the drop-down menu. In this example, the rule will apply to all applications. Click Finish.

- Click OK → OK. Restart your Windows operating system for the changes to take effect.


