|
Since the Release XI of Aether, the technique of exploitation that has been detected is shown within the activity of exploits, along with the program that has been compromised.
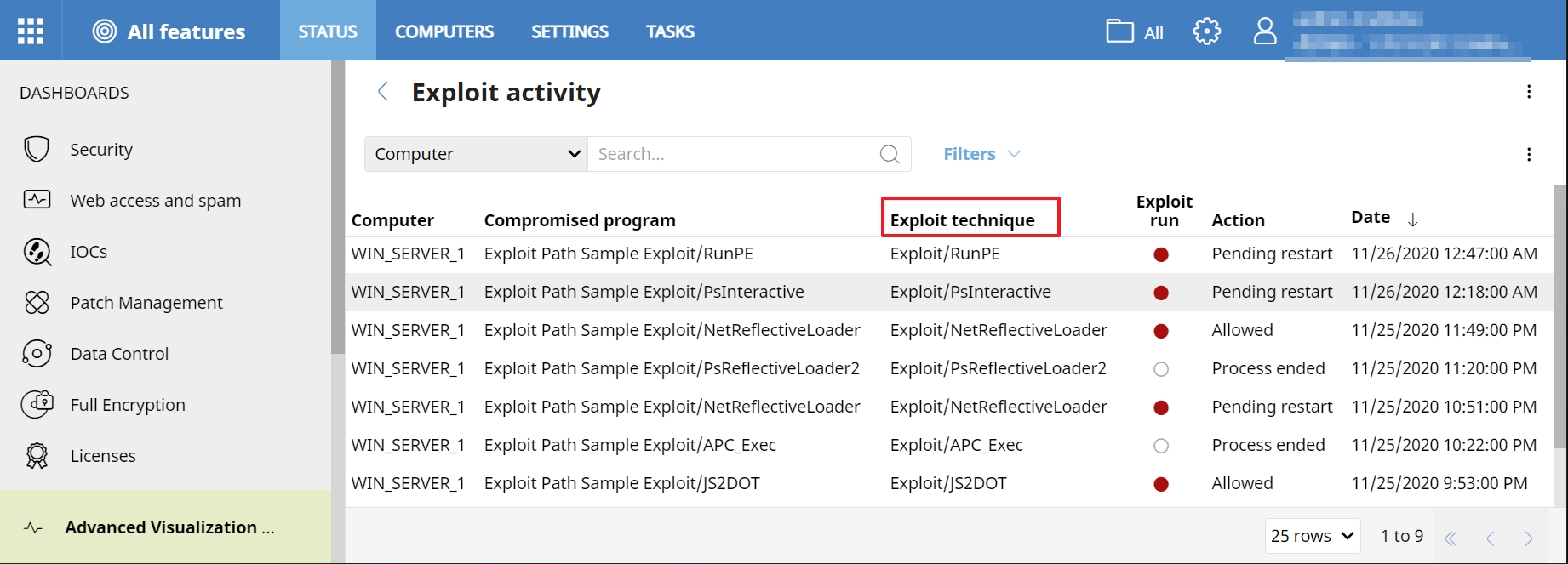
In the following table you will find the different techniques monitored, as well as a brief description of these:
| Name of Technique |
Description of Technique |
| Exploit/Metasploit | Metaploit shellcode signature detection |
| Exploit/ReflectiveLoader | Reflective executable loading (metasploit, cobalt strike, etc) |
| Exploit/RemoteAPCInjection | Remote code injection via APCs |
| Exploit/DynamicExec | Execution of code in pages without execution permissions (32 bits only) |
| Exploit/HookBypass | Hook bypass in running functions |
| Exploit/ShellcodeBehavior | Code execution on MEM_PRIVATE pages that do not correspond to a PEPE |
| Exploit/ROP1 | Execution of memory management APIs when the stack is out of the thread’s limits |
| Exploit/IE_GodMode | GodMode technique in Internet Explorer |
| Exploit/RunPE | Process hollowing techniques / RunPE |
| Exploit/PsReflectiveLoader1 | Powershell – Reflective executable loading (mimikatz, etc) |
| Exploit/PsReflectiveLoader2 | Powershell – Reflective executable loading (mimikatz, etc)) |
| Exploit/NetReflectiveLoader | NET reflective load (Assembly.Load) |
| Exploit/JS2DOT | JS2DOT technique |
| Exploit/Covenant | Covenant detection framework |
| Exploit/DumpLsass | lsass Process Memory Dump |
| Exploit/APC_Exec | Local code execution via APC |
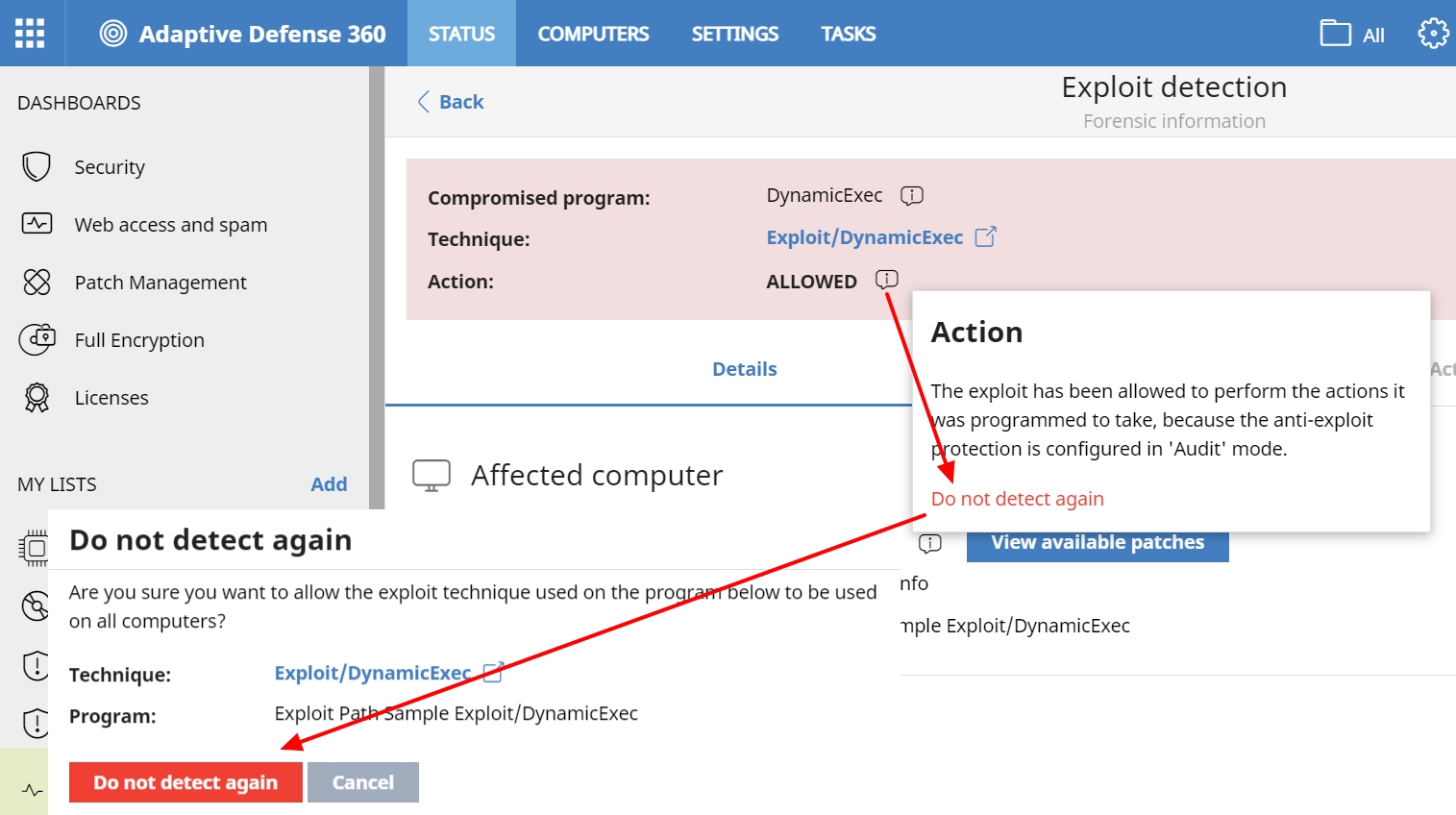
Additionally, the possibility of excluding the detection of a technique for a specific program has been added. In this way, in the event that the client wants to allow, for whatever reason, an exception for a specific process or program, it can be done, and continue to protect the rest of the processes against this attempt at exploitation.
To do this, in the detection of the exploit, within the tooltip accessible from Action, there is the option Do not detect again.