Note
We’ve renamed Microsoft Cloud App Security. It’s now called Microsoft Defender for Cloud Apps. In the coming weeks, we’ll update the screenshots and instructions here and in related pages. For more information about the change, see this announcement. To learn more about the recent renaming of Microsoft security services, see the Microsoft Ignite Security blog.
After you’ve reviewed the list of discovered apps in your environment, you can secure your environment by approving safe apps (Sanctioned) or prohibiting unwanted apps (Unsanctioned) in the following ways.
Sanctioning/unsanctioning an app
You can unsanction a specific risky app by clicking the three dots at the end of the row. Then select Unsanction. Unsanctioning an app doesn’t block use, but enables you to more easily monitor its use with the Cloud Discovery filters. You can then notify users of the unsanctioned app and suggest an alternative safe app for their use.
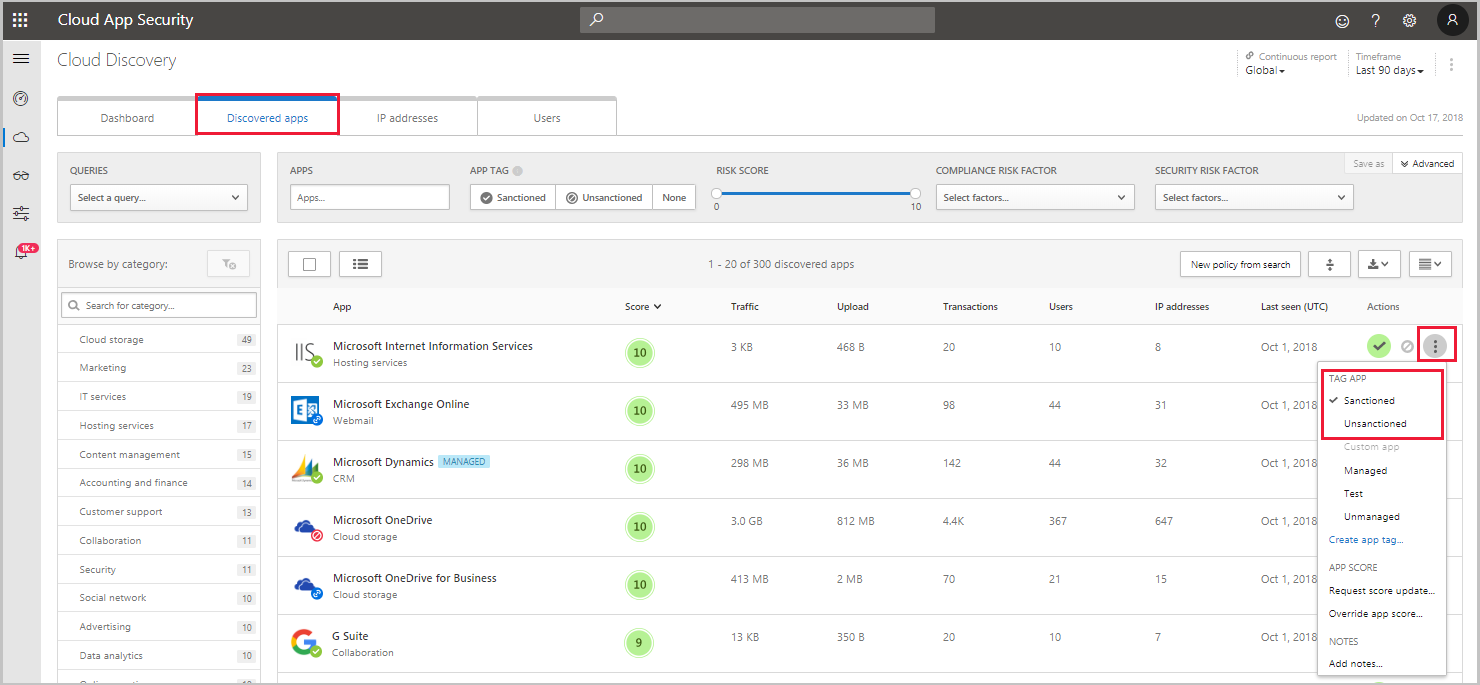
If you have a list of apps you want to sanction or unsanction, use the checkbox to select the apps you want to manage, then select the action.
To query a list of unsanctioned apps, you can generate a block script using the Defender for Cloud Apps APIs.
Note
If your tenant uses Microsoft Defender for Endpoint, Zscaler NSS, or iboss, any app you mark as unsanctioned is automatically blocked by Defender for Cloud Apps, and the following sections regarding creating blocking scripts are unnecessary. For more information, see Integrate with Microsoft Defender for Endpoint, Integrate with Zscaler, and Integrate with iboss respectively.
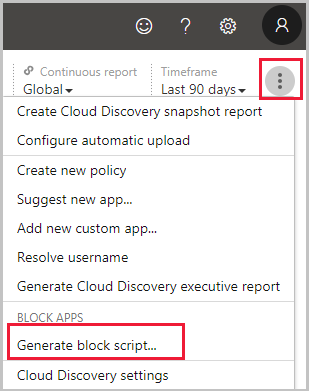
Export a block script to govern discovered apps
Defender for Cloud Apps enables you to block access to unsanctioned apps by using your existing on-prem security appliances. You can generate a dedicated block script and import it to your appliance. This solution doesn’t require redirection of all of the organization’s web traffic to a proxy.
- In the Cloud Discovery dashboard, tag any apps you want to block as Unsanctioned.

- In the title bar, click on the three dots and select Generate block script….
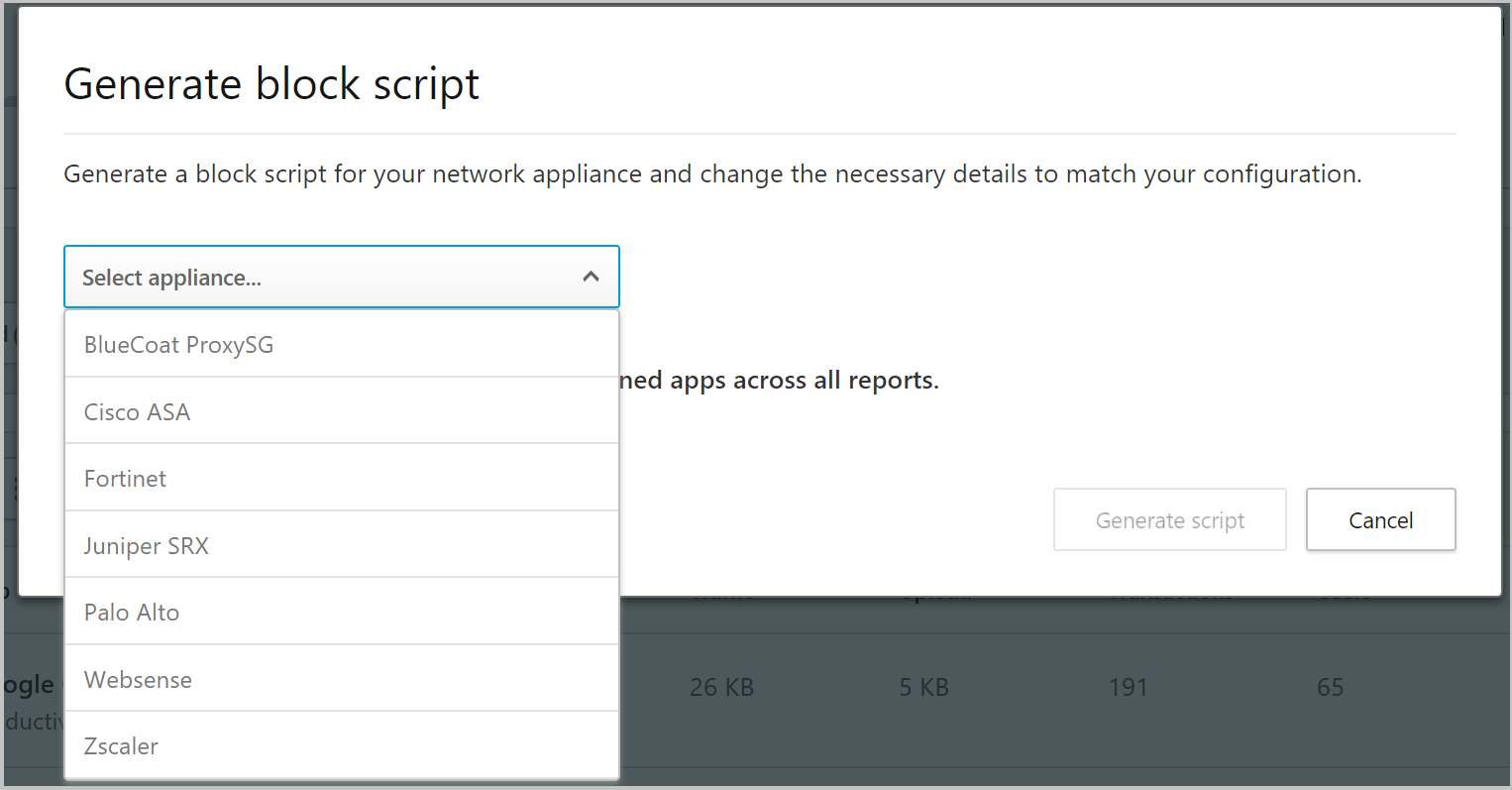
- In Generate block script, select the appliance you want to generate the block script for.
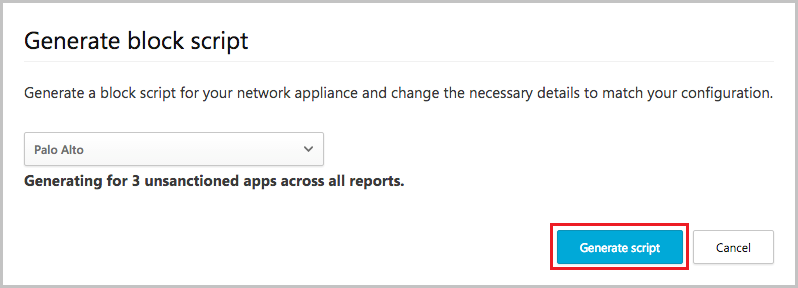
- Then, click the Generate script button to create a block script for all your unsanctioned apps. By default, the file will be named with the date on which it was exported and the appliance type you selected. 2017-02-19_CAS_Fortigate_block_script.txt would be an example file name
- Import the file created to your appliance.

