Applies to:
- Download the MDE Client Analyzer tool to the Windows machine you need to investigate.
- Extract the contents of MDEClientAnalyzer.zip on the machine.
- Open an elevated command line:
- Go to Start and type cmd.
- Right-click Command prompt and select Run as administrator.
- Enter the following command and press Enter:
dos
HardDrivePath\MDEClientAnalyzer.cmdReplace HardDrivePath with the path to which the tool was extracted to, for example:
dosC:\Work\tools\MDATPClientAnalyzer\MDEClientAnalyzer.cmd
In addition to the above, there is also an option to collect the analyzer support logs using live response..
Note
On Windows 10, Windows Server 2019 or later OS editions, or Windows 11, the client analyzer script calls into an executable file called MDEClientAnalyzer.exe to run the connectivity tests to cloud service URLs.
On Windows 8.1, Windows Server 2016 or previous OS editions, the client analyzer script calls into an executable file called MDEClientAnalyzerPreviousVersion.exe to run connectivity tests for Command and Control (CnC) URLs while also calling into Microsoft Monitoring Agent connectivity tool TestCloudConnection.exe for Cyber Data channel URLs.
All the PowerShell scripts and modules included with the analyzer are Microsoft-signed. If files have been modified in any way, then the analyzer is expected to exit with the following error:
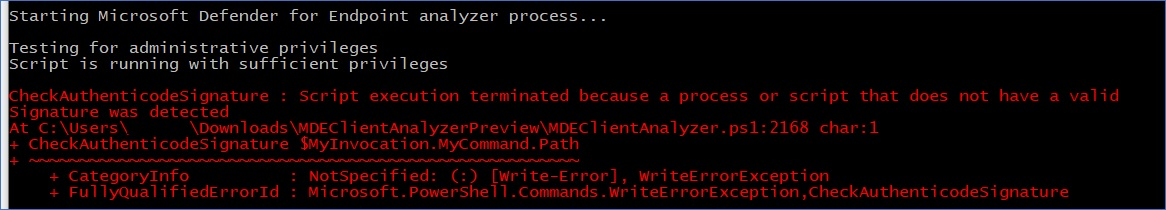
If this error is shown, then the issuerInfo.txt output will contain detailed information about why that happened and what file was affected:
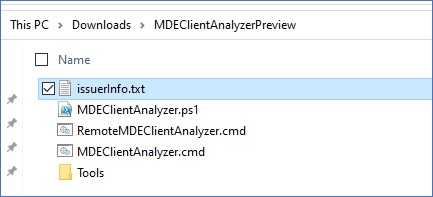
Example contents after MDEClientAnalyzer.ps1 is modified:
Result package contents on Windows
Note
The exact files captured may change depending on factors such as:
- The version of windows on which the analyzer is run.
- Event log channel availability on the machine.
- The start state of the EDR sensor (Sense is stopped if machine is not yet onboarded).
- If an advanced troubleshooting parameter was used with the analyzer command.
By default, the unpacked MDEClientAnalyzerResult.zip file will contain the following items.
- MDEClientAnalyzer.htm
This is the main HTML output file, which will contain the findings and guidance that the analyzer script run on the machine can produce.
- SystemInfoLogs [Folder]
- AddRemovePrograms.csv
Description: List of x86 installed software on x64 OS software collected from registry.
- AddRemoveProgramsWOW64.csv
Description: List of x86 installed software on x64 OS software collected from registry.
- CertValidate.log
Description: Detailed result from certificate revocation executed by calling into CertUtil.
- dsregcmd.txt
Description: Output from running dsregcmd. This provides details about the Azure AD status of the machine.
- IFEO.txt
Description: Output of Image File Execution Options configured on the machine
- MDEClientAnalyzer.txt
Description: This is verbose text file showing with details of the analyzer script execution.
- MDEClientAnalyzer.xml
Description: XML format containing the analyzer script findings.
- RegOnboardedInfoCurrent.Json
Description: The onboarded machine information gathered in JSON format from the registry.
- CertValidate.log
- RegOnboardingInfoPolicy.Json
Description: The onboarding policy configuration gathered in JSON format from the registry.
- SCHANNEL.txt
Description: Details about SCHANNEL configuration applied to the machine such gathered from registry.
- SessionManager.txt
Description: Session Manager specific settings gather from registry.
- SSL_00010002.txt
Description: Details about SSL configuration applied to the machine gathered from registry.
- SCHANNEL.txt
- AddRemovePrograms.csv
- EventLogs [Folder]
- utc.evtx
Description: Export of DiagTrack event log
- senseIR.evtx
Description: Export of the Automated Investigation event log
- sense.evtx
Description: Export of the Sensor main event log
- OperationsManager.evtx
Description: Export of the Microsoft Monitoring Agent event log
- utc.evtx

