Issue
- Your ESET product detected a Win32/Filecoder.Crysis infection
- Decrypt specific variants of your files using the ESETCrysisDecryptor.exe tool
- Your personal files have become encrypted
- Your files have been renamed with one of the following extensions: .xtbl, .crysis, .crypt, .lock, .crypted, .dharma, .wallet, .onion
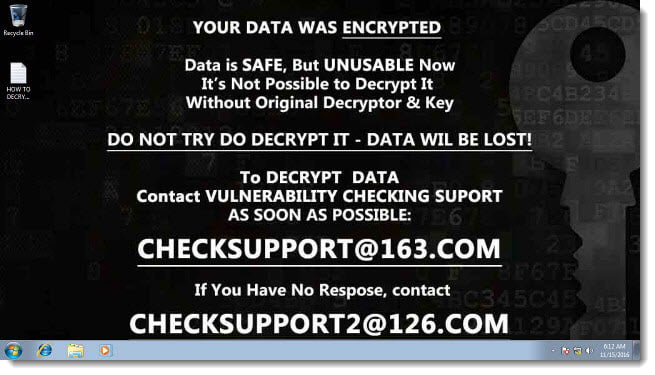
- You receive one of the following messages on your computer’s desktop background, or in a .txt, .html or .png file:
– “Attention! Your computer was attacked by virus-encoder.. [email protected]”
– “Your data was encrypted… Do not try to decrypt it – data wil be lost… [email protected]”
– “To restore information email technical support”
– “all your data was crypted to get it back write to [email protected]”
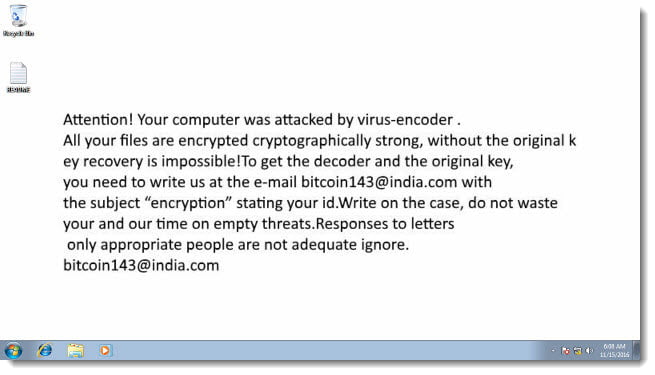
Figure 1-1
Click +Details for more information and additional images associated with this ransomware
Details
Win32/Filecoder.Crysis is a trojan that encrypts files on local drives. The user is told they must send information and make a payment using the Bitcoin payment service in order to decrypt their files.
- Win32/Filecoder.Crysis threat description on virusradar.com
- welivesecurity.com :: Beyond TeslaCrypt: Crysis family lays claim to parts of its territory
Indicators of compromise
.{%EmailAddress%}.CrySiS
.{%EmailAddress%–%EmailAddress%}.xtbl
.[%EmailAddress%].dharma
.ID%hexnum%.%EmailAddress%.xtbl
.id-%hexnum%.{%EmailAddress%}.crypt
.id-%hexnum%.{%EmailAddress%}.lock
.id-%hexnum%.{%EmailAddress%}.crypted
.[%EmailAddress%].wallet
.[%EmailAddress%].onion
Image gallery
Solution
- Download the ESET Crysis decryptor tool version 2.0.4.0 and save the file to your desktop.
- Click Start → All Programs → Accessories, right-click Command prompt and then select Run as administrator from the context menu.
- Windows 8 / 8.1 / 10 users: press the Windows key + Q to search for applications, type Command prompt into the Search field, right-click Command prompt and then select Run as administrator from the context menu.
- Type the command
cd %userprofile%\Desktop(do not replace “userprofile” with your username–type the command exactly as shown) and then press Enter. - Type the command
ESETCrysisDecryptor.exeand press Enter. - Read and agree to the end-user license agreement.
- Type
ESETCrysisDecryptor.exe C:and press Enter to scan the C drive. To scan a different drive replaceC:with the applicable drive letter.
- The ESET Crysis decryptor tool will run and the “Looking for infected files…” message will be displayed. If an infection is discovered, follow the prompts from the ESET Crysis decryptor tool to clean your system.
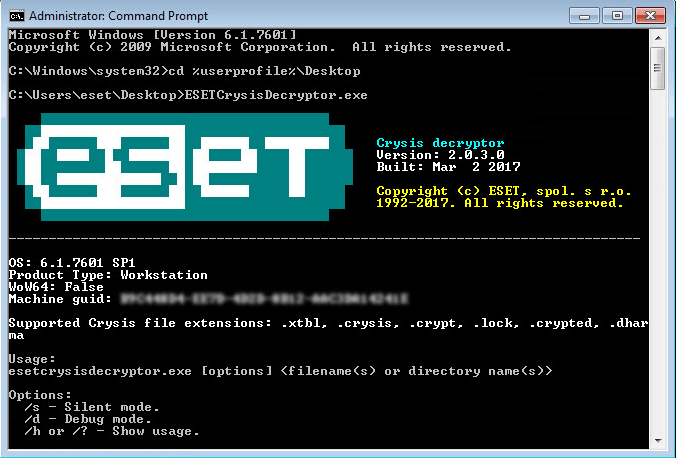
Figure 1-2