Note
We’ve renamed Microsoft Cloud App Security. It’s now called Microsoft Defender for Cloud Apps. In the coming weeks, we’ll update the screenshots and instructions here and in related pages. For more information about the change, see this announcement. To learn more about the recent renaming of Microsoft security services, see the Microsoft Ignite Security blog.
You can create app discovery policies to alert you when new apps are detected. Defender for Cloud Apps also searches all the logs in your Cloud Discovery for anomalies.
Creating an app discovery policy
Discovery policies enable you to set alerts that notify you when new apps are detected within your organization.
- Go to Control > Policies > Shadow IT.
- Click Create policy and select App discovery policy.
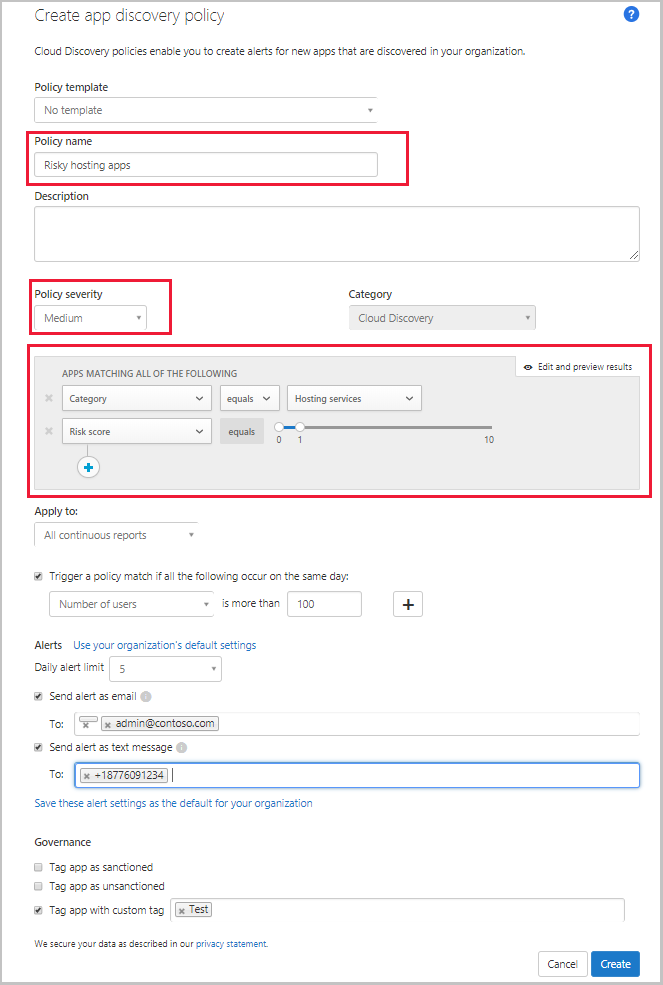
- Give your policy a name and description. If you want, you can base it on a template. For more information on policy templates, see Control cloud apps with policies.
- Set the Severity of the policy.
- To set which discovered apps trigger this policy, add filters.
- You can set a threshold for how sensitive the policy should be. Enable Trigger a policy match if all the following occur on the same day. You can set criteria that the app must exceed daily to match the policy. Select one of the following criteria:
- Daily traffic
- Downloaded data
- Number of IP addresses
- Number of transactions
- Number of users
- Uploaded data
- Set a Daily alert limit under Alerts. Select whether the alert is sent as an email, a text message, or both. Then provide phone numbers and email addresses as needed.
- Clicking Save alert settings as the default for your organization enables future policies to use the setting.
- If you have a default setting, you can select Use your organization’s default settings.
- Select Governance actions to apply when an app matches this policy. It can tag policies as Sanctioned, Unsanctioned, or a custom tag.
- Click Create.
Note
- Newly created discovery policies (or policies with updated continuous reports) trigger an alert once in 90 days per app per continuous report, regardless of whether there are existing alerts for the same app. So, for example, if you create a policy for discovering new popular apps, it may trigger additional alerts for apps that have already been discovered and alerted on.
- Data from snapshot reports do not trigger alerts in app discovery policies.
For example, if you’re interested in discovering risky hosting apps found in your cloud environment, set your policy as follows:
Set the policy filters to discover any services found in the hosting services category, and that have a risk score of 1, indicating they’re highly risky.
Set the thresholds that should trigger an alert for a certain discovered app at the bottom. For instance, alert only if over 100 users in the environment used the app and if they downloaded a certain amount of data from the service. Additionally, you can set the limit of daily alerts you wish to receive.
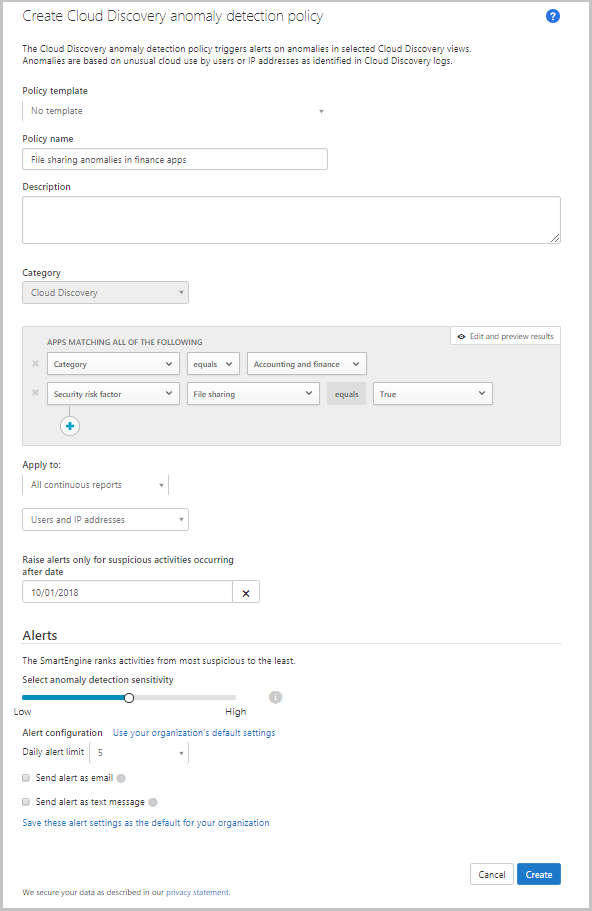
Cloud Discovery anomaly detection
Defender for Cloud Apps searches all the logs in your Cloud Discovery for anomalies. For instance, when a user, who never used Dropbox before, suddenly uploads 600 GB to it, or when there are a lot more transactions than usual on a particular app. The anomaly detection policy is enabled by default. It’s not necessary to configure a new policy for it to work. However, you can fine-tune which types of anomalies you want to be alerted about in the default policy.
- In the console, click on Control followed by Policies.
- Click Create policy and select Cloud Discovery anomaly detection policy.
- Give your policy a name and description. If you want, you can base it on a template, For more information on policy templates, see Control cloud apps with policies.
- To set which discovered apps trigger this policy, click Add filters.
The filters are chosen from drop-down lists. To add filters, click the plus button. To remove a filter, you click the ‘X’.
- Under Apply to choose whether this policy applies All continuous reports or Specific continuous reports. Select whether the policy applies to Users, IP addresses, or both.
- Select the dates during which the anomalous activity occurred to trigger the alert under Raise alerts only for suspicious activities occurring after date.
- Set a Daily alert limit under Alerts. Select whether the alert is sent as an email, a text message, or both. Then provide phone numbers and email addresses as needed.
- Clicking Save alert settings as the default for your organization enables future policies to use the setting.
- If you have a default setting, you can select Use your organization’s default settings.
- Click Create.