Microsoft Defender for Identity lateral movement path detection relies on queries that identify local admins on specific machines. These queries are performed with the SAM-R protocol, using the Defender for Identity Service account created during Defender for Identity installation Step 2. Connect to AD.
Configure SAM-R required permissions
To ensure Windows clients and servers allow your Defender for Identity account to perform SAM-R, a modification to Group Policy must be made to add the Defender for Identity service account in addition to the configured accounts listed in the Network access policy. Make sure to apply group policies to all computers except domain controllers.
Note
Before enforcing new policies such as this one, it is critical to make sure that your environment remains secure, and any changes will not impact your application compatibility. Do this by first enabling and then verifying the compatibility of proposed changes in audit mode before making changes to your production environment. You may observe increased SAM-R traffic, generated by the Defender for Identity sensors.
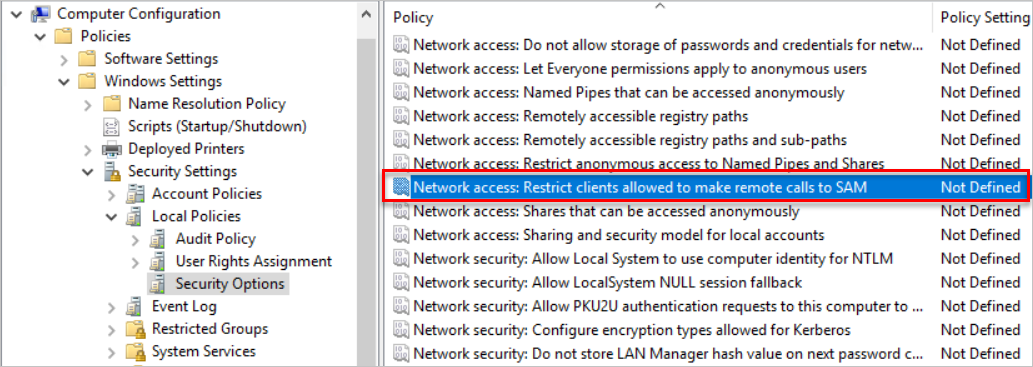
- Locate the policy:
- Policy Name: Network access – Restrict clients allowed to make remote calls to SAM
- Location: Computer configuration, Windows settings, Security settings, Local policies, Security options
- Add the Defender for Identity service account to the list of approved accounts able to perform this action on your modern Windows systems.
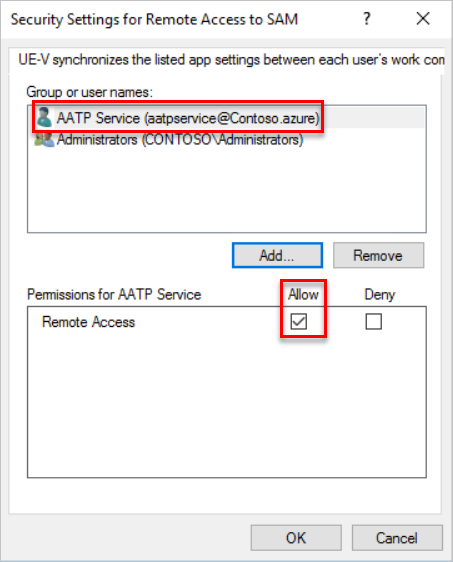
- AATP Service (the Defender for Identity service account created during installation) now has the privileges needed to perform SAM-R in the environment.
For more on SAM-R and this Group Policy, see Network access: Restrict clients allowed to make remote calls to SAM.
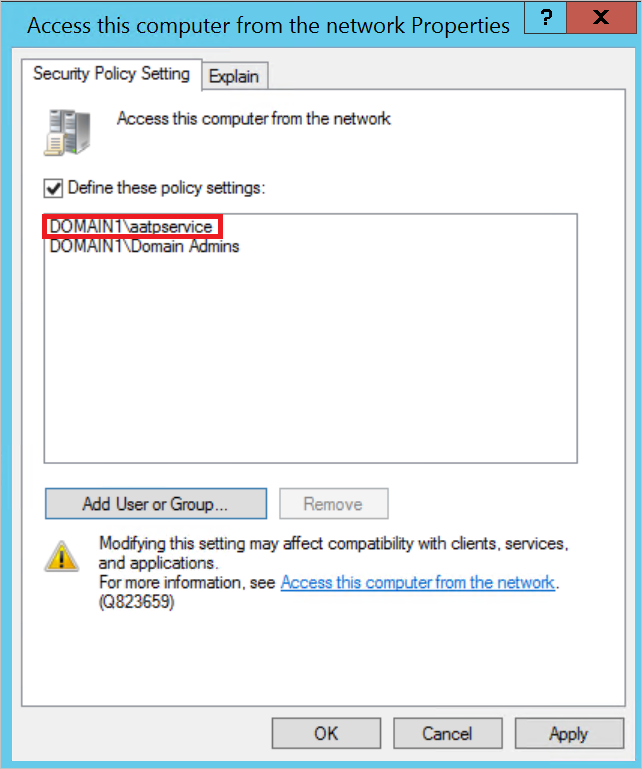
Access this computer from the network setting
If you’ve defined the Access this computer from the network setting in any GPO that applies to computers in your domain, you need to add the Defender for Identity service account to the list of allowed accounts for that setting:
Note
The setting is not enabled by default. If you have not enabled it previously, you don’t need to modify it to allow Defender for Identity to make remote calls to SAM.
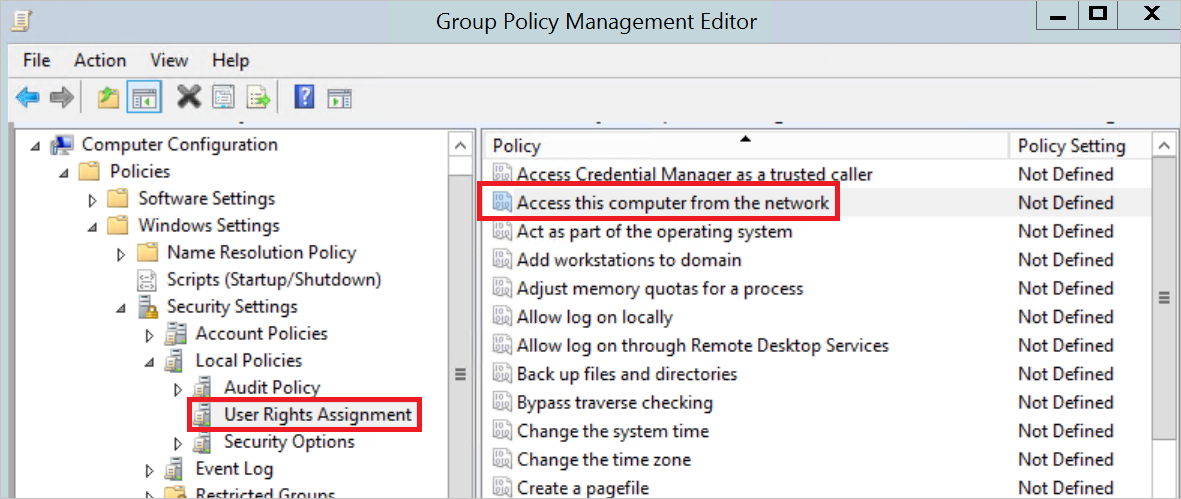
To add the service account, go to the policy and navigate to Computer Configuration -> Policies -> Windows Settings -> Local Policies -> User Right Assignment. Then open the setting Access this computer from the network.
Then add the Defender for Identity service account to the list of approved accounts.