Note
We’ve renamed Microsoft Cloud App Security. It’s now called Microsoft Defender for Cloud Apps. In the coming weeks, we’ll update the screenshots and instructions here and in related pages. For more information about the change, see this announcement. To learn more about the recent renaming of Microsoft security services, see the Microsoft Ignite Security blog.
Cloud Discovery data can now be enriched with Azure Active Directory username data. When you enable this feature, the username, received in discovery traffic logs, is matched and replaced by the Azure AD username. Cloud Discovery enrichment enables the following features:
- You can investigate Shadow IT usage by Azure Active Directory user.
- You can correlate the Discovered cloud app use with the API collected activities.
- You can then create custom logs based on Azure AD user groups. For example, a Shadow IT report for a specific Marketing department.
Prerequisites
- Data source must provide username information
- Office 365 app connector connected
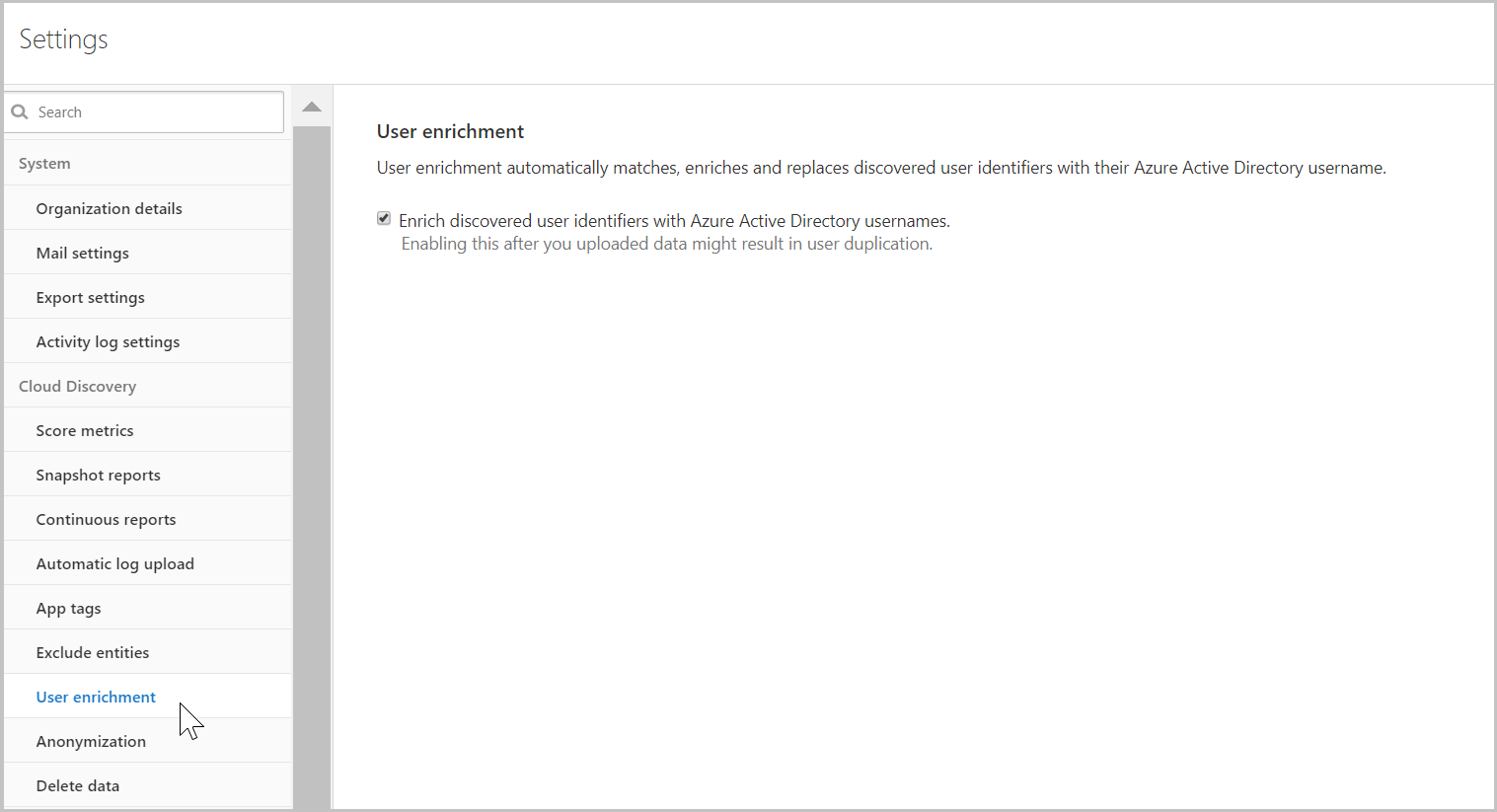
Enabling user data enrichment
- Under the Settings cog, select Settings.
- In the Settings page, under Cloud Discovery, select User enrichment.
- In the User enrichment tab, select Enrich discovered user identifiers with Azure Active Directory usernames. This option enables Defender for Cloud Apps to use Azure Active Directory data to enrich usernames by default.