Note
We’ve renamed Microsoft Cloud App Security. It’s now called Microsoft Defender for Cloud Apps. In the coming weeks, we’ll update the screenshots and instructions here and in related pages. For more information about the change, see this announcement. To learn more about the recent renaming of Microsoft security services, see the Microsoft Ignite Security blog.
Microsoft Defender for Cloud Apps integrates with Azure Active Directory Identity Protection to provide user entity behavioral analytics (UEBA) across a hybrid environment. For more information about the machine learning and behavioral analytics provided by Identity Protection, see What is Identity Protection?.
Prerequisites
- A Cloud App Security Admin account to enable integration between Identity Protection and Defender for Cloud Apps.
Enable Identity Protection
Note
The Identity Protection feature is enabled by default. However, if the feature was disabled, you can use these steps to enable it.
To enable Defender for Cloud Apps integration with Identity Protection:
- In Defender for Cloud Apps, under the settings cog, select Settings.
- Under Threat Protection, select Azure AD Identity Protection.
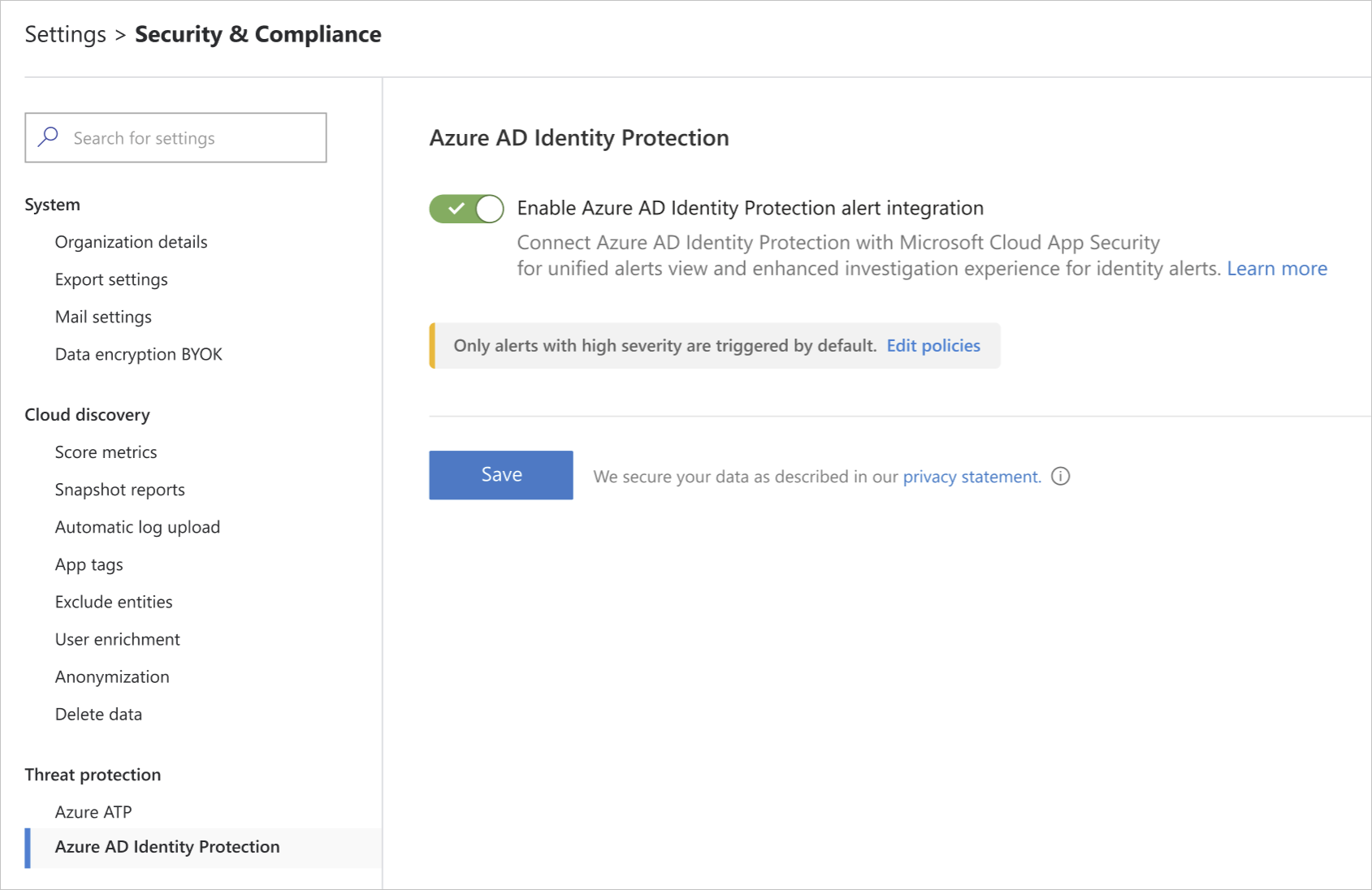
- Select Enable Azure AD Identity Protection alert integration and then click Save.
After enabling Identity Protection integration, you’ll be able to see alerts for all the users in your organization.
Disable Identity Protection
To disable Defender for Cloud Apps integration with Identity Protection:
- In Defender for Cloud Apps, under the settings cog, select Settings.
- Under Threat Protection, select Azure AD Identity Protection.
- Clear Enable Azure AD Identity Protection alert integration and then click Save.
Note
- When the integration is disabled, existing Identity Protection alerts are kept in accordance with Defender for Cloud Apps retention policies.
- Since Defender for Cloud Apps only consumes interactive logins from Azure AD, some alerts may not show related activities. You can investigate such activities in the Azure AD portal.
Configure Identity Protection Policies
The Identity Protection policies can be fine-tuned to your organization’s need using the severity slider. The sensitivity slider allows you to control which alerts are ingested. In this way, you can adapt the detection according to your coverage needs and your (SNR) targets.
The following policies are available:
| Policy | Description | Default state | Default Severity |
|---|---|---|---|
| Leaked Credentials | Shows leaked credentials alerts, user’s valid credentials have been leaked | Enabled | Low – Receive all alerts |
| Risky sign-in | Aggregates multiple risky sign-in detections, sign-ins that weren’t performed by the user | Enabled | High – Receive only high severity alerts |
Note
Defender for Cloud Apps does not send email notifications for Identity Protection alerts. However, you can configure email notifications for them in the Identity Protection portal.
Next steps
If you run into any problems, we’re here to help. To get assistance or support for your product issue, please open a support ticket.

