Important
Microsoft Defender for Business is now in preview, and will roll out gradually to customers and IT Partners who sign-up here to request it. We will onboard an initial set of customers and partners in the coming weeks and will expand the preview leading up to general availability. Note that preview will launch with an initial set of scenarios, and we will be adding capabilities regularly.
Some information in this article relates to prereleased products/services that might be substantially modified before they are commercially released. Microsoft makes no warranties, express or implied, for the information provided here.
Microsoft Defender for Business (preview) provides a streamlined setup and configuration experience, designed especially for the small and medium-sized business. Use this article as a guide.
The setup and configuration process
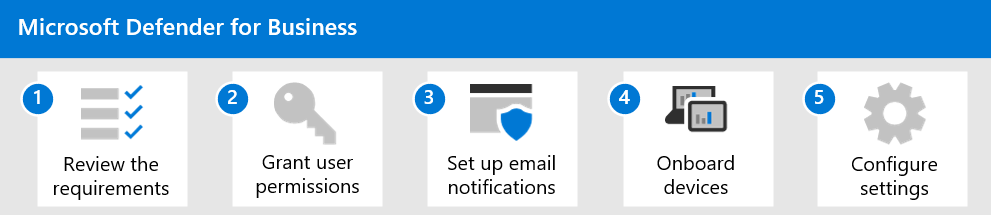
| Step | Article | Description |
|---|---|---|
| 1 | Review the requirements | Review the requirements, including supported operating systems, for Microsoft Defender for Business (preview). See Microsoft Defender for Business (preview) requirements. |
| 2 | Assign roles and permissions | People on your security team need permissions to perform tasks, such as reviewing detected threats & remediation actions, viewing & editing policies, onboarding devices, and using reports. You can grant these permissions through certain roles. See Assign roles and permissions. |
| 3 | Set up email notifications | You can specify who should receive email notifications when alerts are triggered or new vulnerabilities are discovered. See Set up email notifications. |
| 4 | Onboard devices | Microsoft Defender for Business (preview) is set up so that you can choose from several options to onboard your company’s devices. See Onboard devices to Microsoft Defender for Business (preview). |
| 5 | Configure your security settings and policies | You can choose from several options to configure your security settings and policies, including a simplified configuration process or Microsoft Endpoint Manager. See Configure your security settings and policies. |

